Key consulting method for switching mobile station in wireless local network
A technology of wireless local area network and key negotiation, applied in the field of wireless local area network communication, can solve the problem that the process security of mobile station switching access point cannot be guaranteed, increase the design complexity of identity authentication and key negotiation, and increase the cost of wireless network construction and other problems, to achieve the effect of improving the roaming switching speed, simplifying the synchronization judgment steps, and improving the switching speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in more detail below in conjunction with the accompanying drawings and specific embodiments.
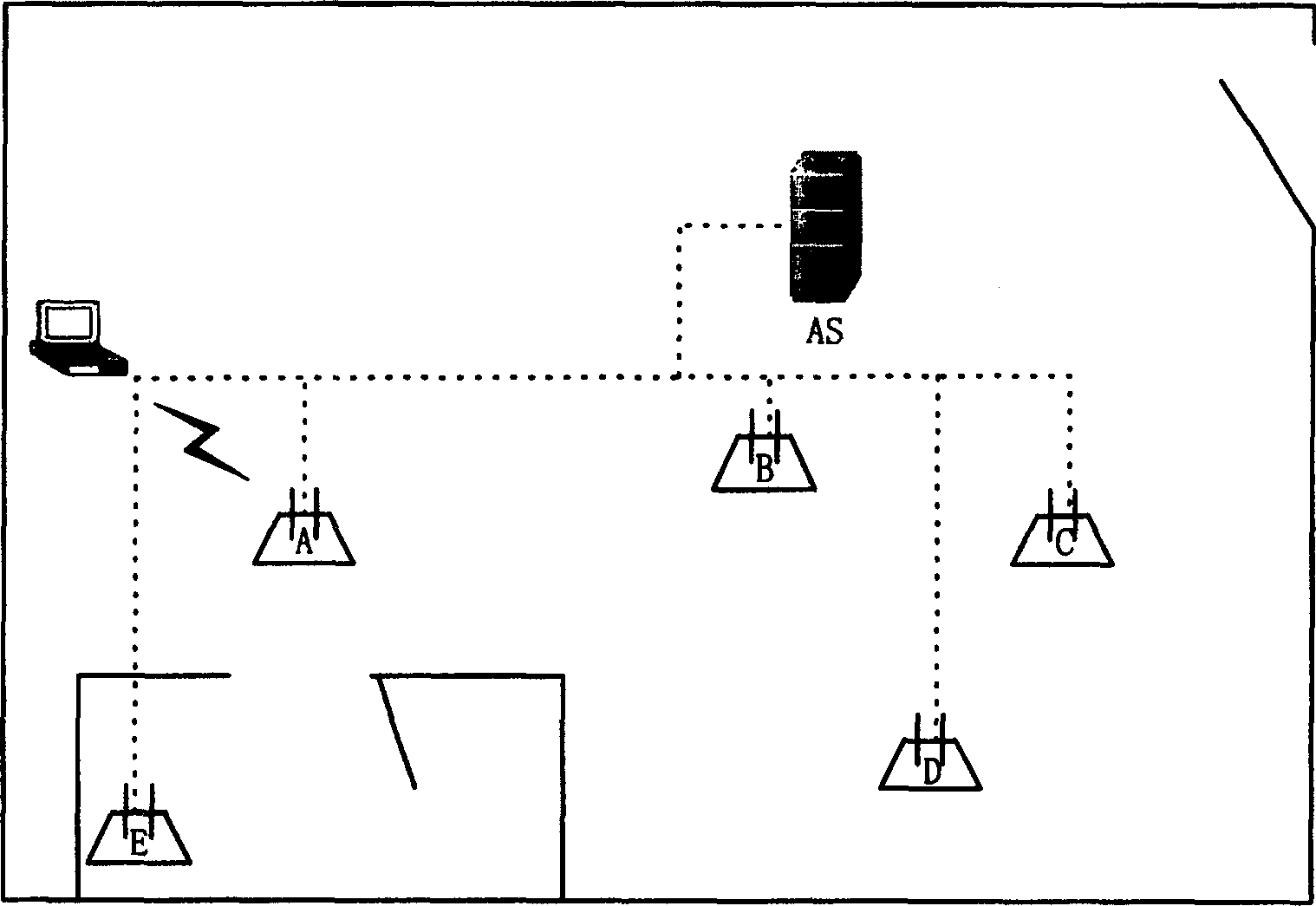
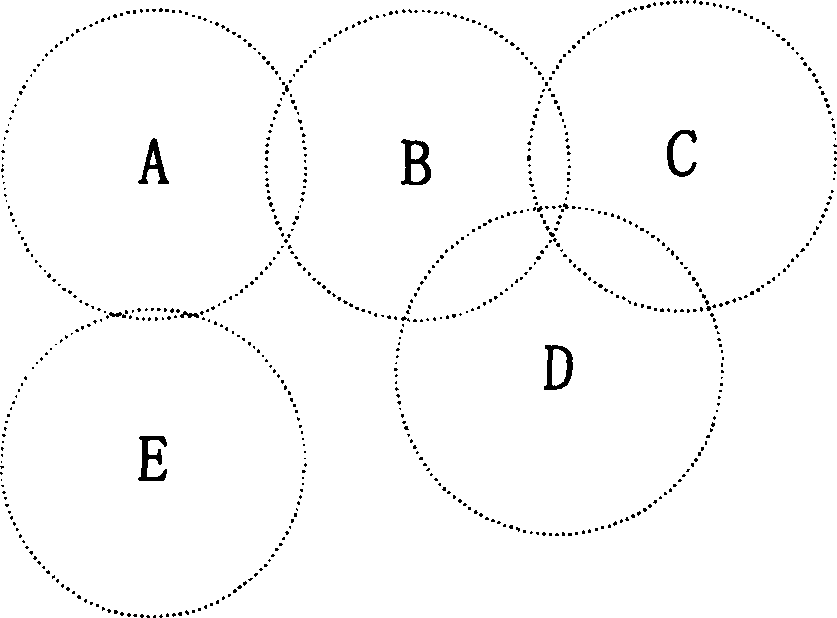
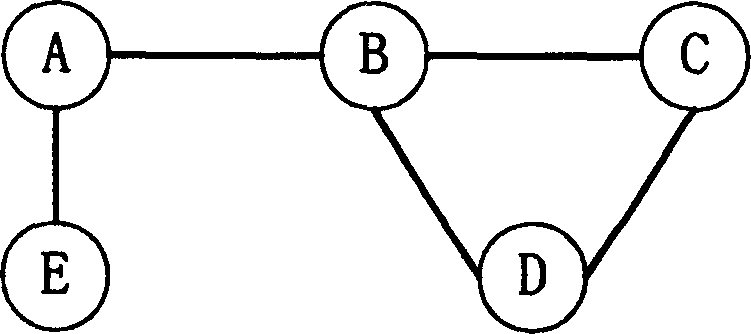
[0031] The network composition structure involved in the method for pre-negotiating the master key in the wireless local area network of the present invention is as follows:figure 1 As shown, in the schematic diagram of the network composition structure, access points (AP: Access Point) A, B, C, D, E are a group of adjacent access points, wherein, access point A is a mobile station (STA : the current access point of Station), the access points B and E are the neighbor access points of the current access point A, and the authentication server (AS: Authentication Server) is connected to each access point. figure 2 Shown is the coverage map corresponding to the group of access points. image 3 Shown is a schematic diagram of the topology corresponding to the group of access points. The coverage distribution of each access point and the to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com