Traceable access control method based on double block chains
An access control and blockchain technology, applied in encryption devices with shift registers/memory, digital transmission systems, secure communication devices, etc., can solve the problem of inability to determine the credibility of third-party authorization centers and low encryption efficiency of data files , Unable to guarantee reliability and other issues, to reduce the risk of being attacked, improve reliability, and prevent file loss and tampering.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to make the purpose, technical solutions and advantages of the present application more clearly understood, the present application will be described in further detail below with reference to the accompanying drawings and embodiments.
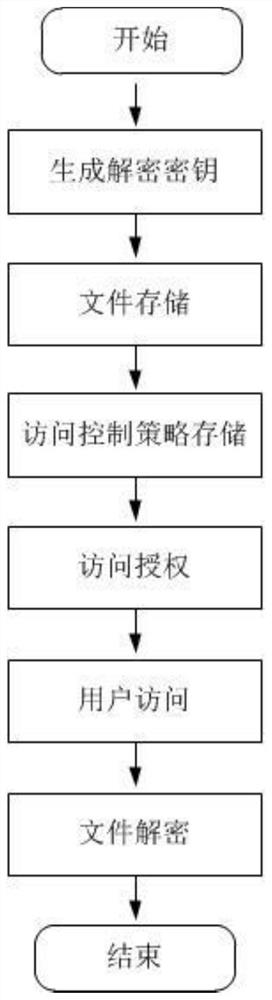
[0062] In the method for traceability access control based on dual blockchains described in this embodiment, the flow chart is as follows figure 1 shown, including the following steps:
[0063] S10, generate a decryption key
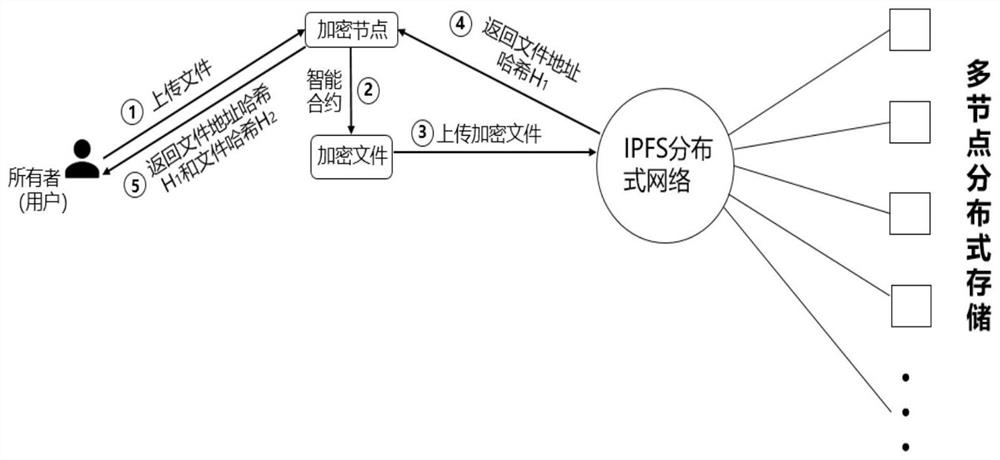
[0064] Users who use this method to upload files or access files need to register first to obtain an exclusive decryption key. During registration, users upload their own attributes to the user management point. After receiving their own attributes sent by the client, the user management point executes the unpaired CP-ABE algorithm to assign a user ID UID and a global parameter PP to each user. The user management point calls the smart contract to manage the attribute set, generates the public key PK and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com