Identity authentication method and device
An identity authentication and identity technology, which is applied in the field of identity authentication methods and devices, can solve the problems of identifying access controllers, requesting equipment, and network security risks, and achieve the effects of real-time authentication, exposure prevention, and confidentiality protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
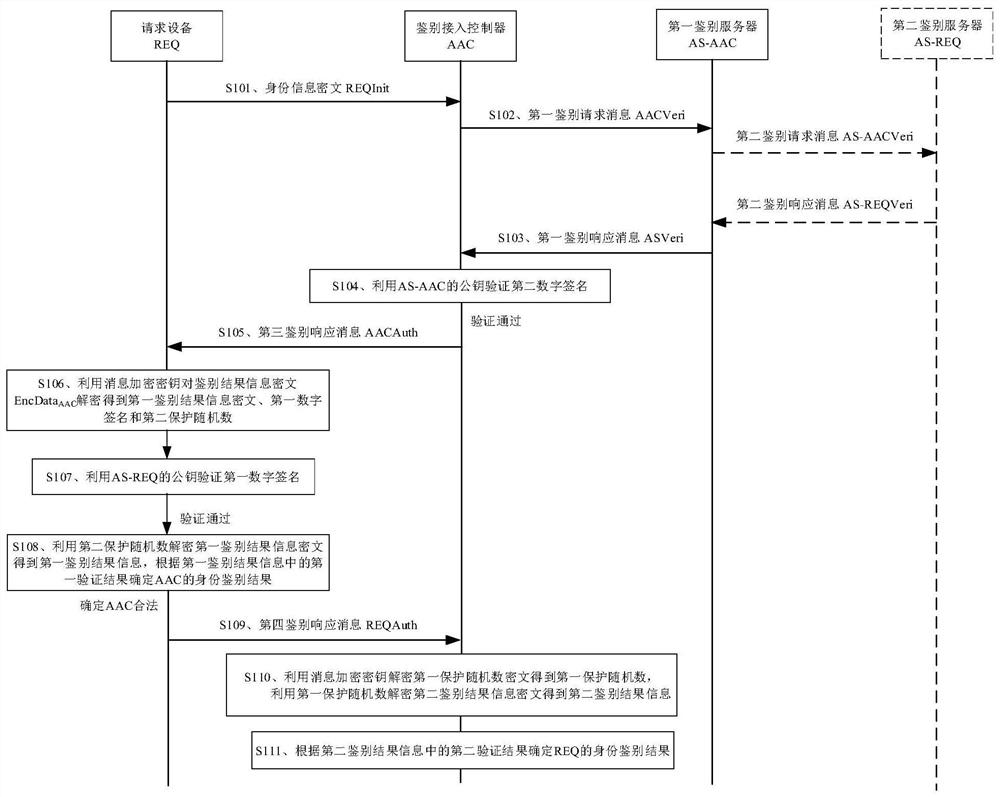
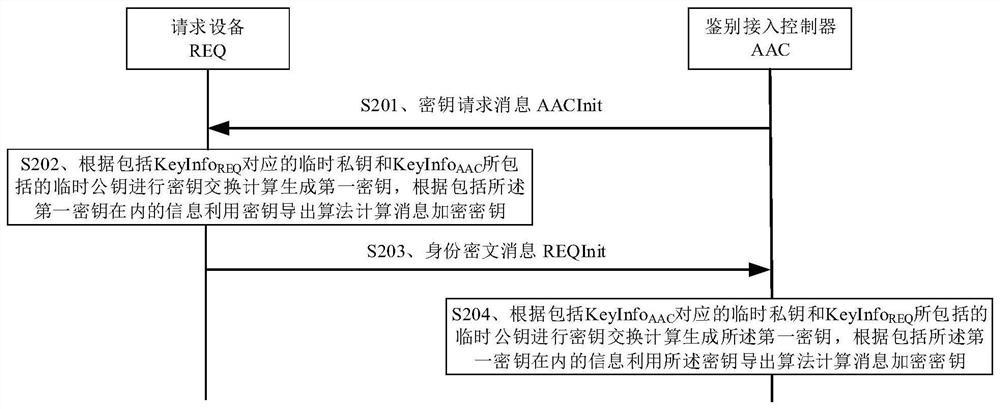
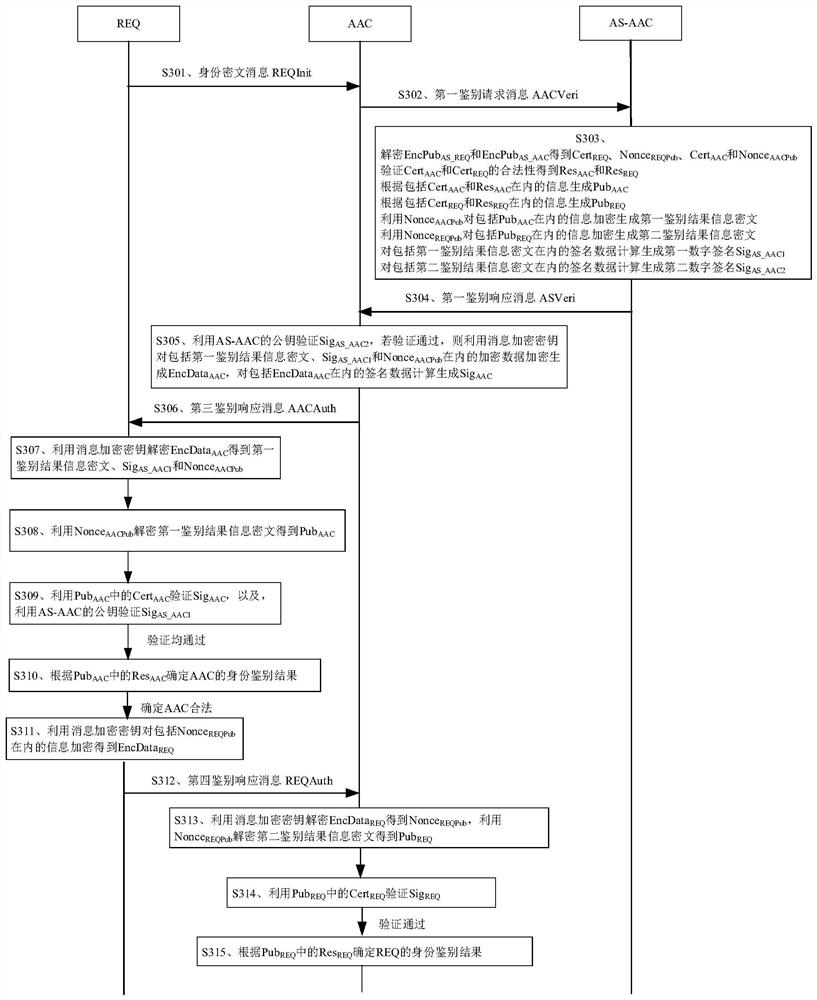
[0060] In a communication network, the requesting device can access the network through the authentication access controller. In order to ensure that the requesting device accessing the network belongs to a legitimate user, the authentication access controller needs to authenticate the identity of the requesting device. Similarly, in order to ensure that the network accessed by the requesting device belongs to a legitimate network, the requesting device also needs to authenticate the identity of the authentication access controller.
[0061] Taking the current wireless communication and mobile communication scenarios as an example, in the scenario where the requesting device accesses the wireless network through the authentication access controller, the requesting device may be a mobile phone, a personal digital assistant (PDA), a tablet computer, etc. The terminal device, the authentication access controller can be a network side device such as a wireless access point and a wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com