Vulnerability mining technology based on reinforcement learning
A reinforcement learning and vulnerability mining technology, applied in the field of reinforcement learning-based vulnerability mining technology, can solve problems such as inability to arrange and partition products, and achieve the effect of reducing scale, improving performance, and reducing additional resource consumption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
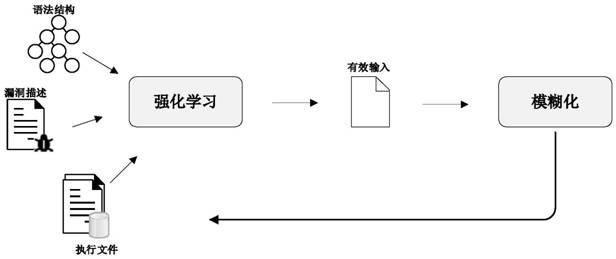
[0044] according to figure 1 , the embodiment of the present invention provides a semantic reasoning mechanism flow, using reinforcement learning to generate input containing the required semantics, in order to make it more practical, we learn from the different influences of symbols and operations defined in the grammar To start, understanding these semantics can more reasonably generate inputs that satisfy the properties provided by the vulnerability description. Combining fuzzification with reinforcement learning has another benefit. The large execution time provides rich data and precise predictions for learning to understand the semantics. , the learned model is continuously updated during the fuzzification process, providing the possibility for more efficient inputs that may trigger vulnerabilities. State-of-the-art fuzzing frameworks such as AFL use these states to guide input generation, however, how to properly mix different criteria can affect Input generation, our r...
Embodiment 2
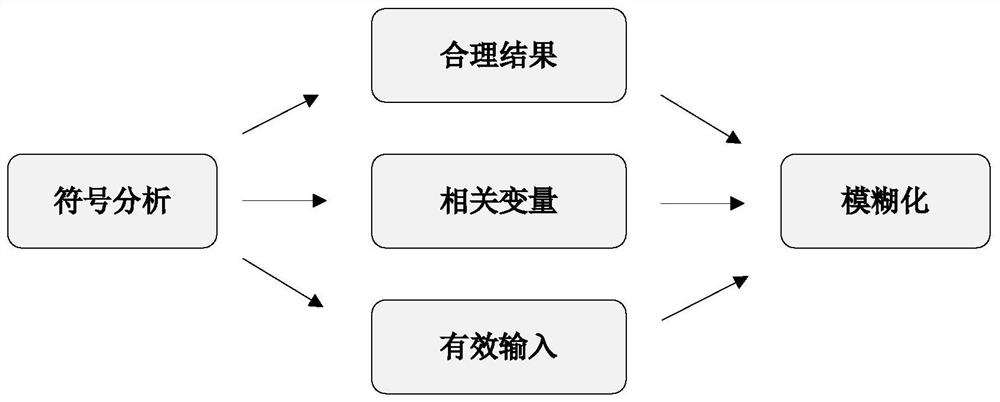
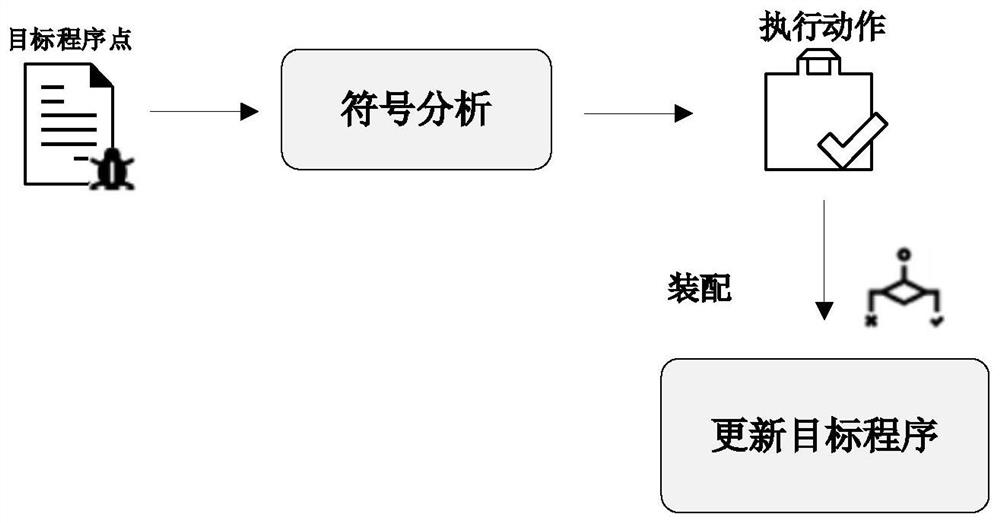
[0046] according to figure 2 and image 3, the embodiment of the present invention provides a process of guiding the fuzzification process by a symbolic analysis engine. Symbolic execution is one of the most powerful methods for detecting vulnerabilities, and it can accurately generate an input that guides execution to a specific program point, for example, A single condition x*x=100 may be difficult to randomly mutate to generate a feasible value x=10. For an integer variable x, the probability is less than 10 to 20. As the number of path conditions increases, large-scale programs exacerbate this problem, and constraint solving makes up for it To address the shortcomings of random mutation in handling complex path conditions, the combination of the two methods improves the ability of vulnerability detection. However, the effectiveness of constraint solving is mainly constrained by well-known performance problems in constraint solving, and our proposed method exploits the adv...
Embodiment 3
[0049] Combined with the content of the first and second embodiments above, the embodiment of the present invention uses the "exploration-utilization" model method to guide the mutation selection strategy of the fuzzer. The model framework can be used to evaluate the effect of mutation benefit, automatically adjust the mutation operation strategy, replace the random strategy in the original AFL mutation algorithm, and realize the optimization of AFL mutation performance;
[0050] There are multiple operations in AFL mutation, which are represented by n. Each mutation operation can be regarded as a different gambling machine. For each mutation operation, θn is used to represent the probability that the subsample generated by this mutation operation will generate a new path. Finally, by calculating the previous mutation, similar to the way of selecting the "best" rocker k, the mutation operation with the highest probability is selected for the next round of mutation. The probabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com