Network intrusion detection method based on improved BYOL self-supervised learning
A technology of network intrusion detection and supervised learning, which is applied in neural learning methods, biological neural network models, and platform integrity maintenance. It can solve problems such as poor detection ability of unknown attacks, premature convergence of genetic algorithms, and high false alarm rate, and achieve optimal BYOL loss function, enhancing various performance indicators, evaluating scientific and comprehensive effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Combine below Figure 1-31 The present invention is further described, but the protection scope of the present invention is not limited to the content.
[0042] In the interest of clarity, not all features of an actual embodiment are described, and in the following description, well-known functions and constructions are not described in detail since they would obscure the invention with unnecessary detail and should be considered in the development of any actual embodiment , a large number of implementation details must be made to achieve the specific goals of the developer, such as changing from one embodiment to another according to the constraints of the relevant system or the relevant business, in addition, it should be considered that such development work may be complex and time-consuming Yes, but it is just routine work for those skilled in the art.
[0043] Table 2 Symbol Explanation
[0044]
[0045]
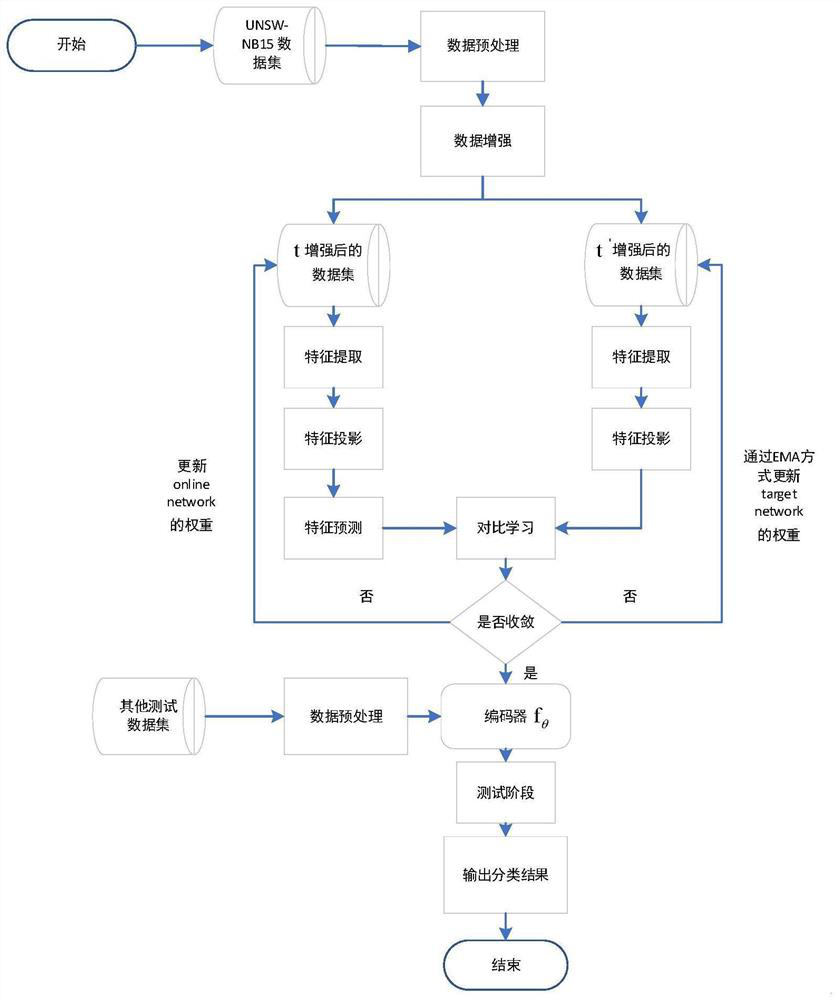
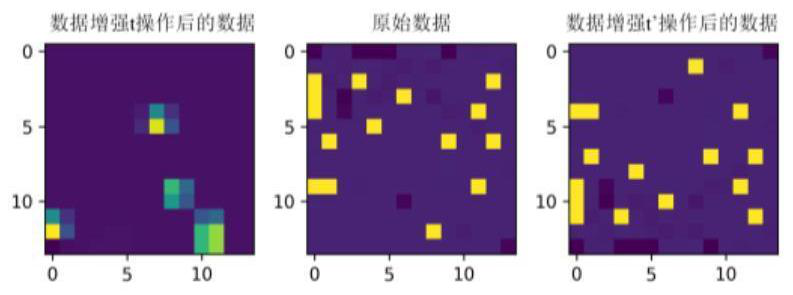
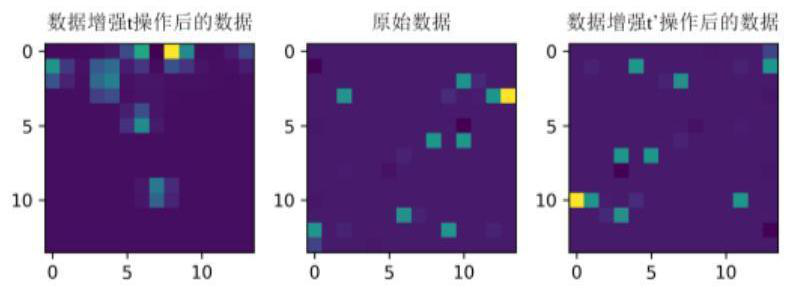
[0046] like figure 1 As shown, an improved BYOL se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com