Micro-service access control method, system and device based on security attribute
A security attribute and access control technology, applied in the field of network security, can solve problems such as system microservice attacks, hidden dangers, and no countermeasures, and achieve the effects of clear system hierarchy, enhanced security management, and reduced performance problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
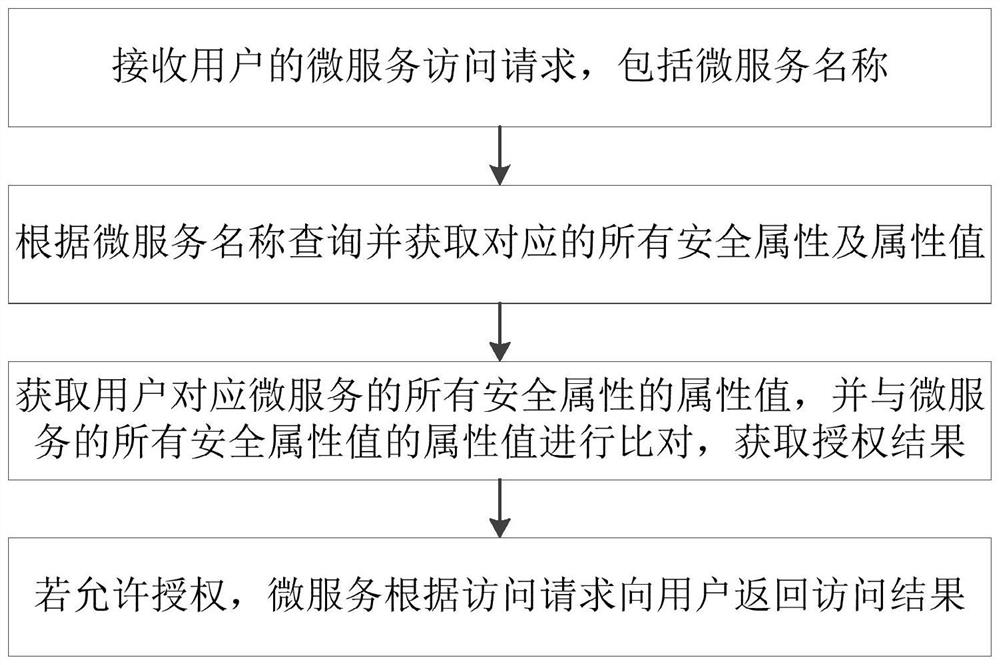
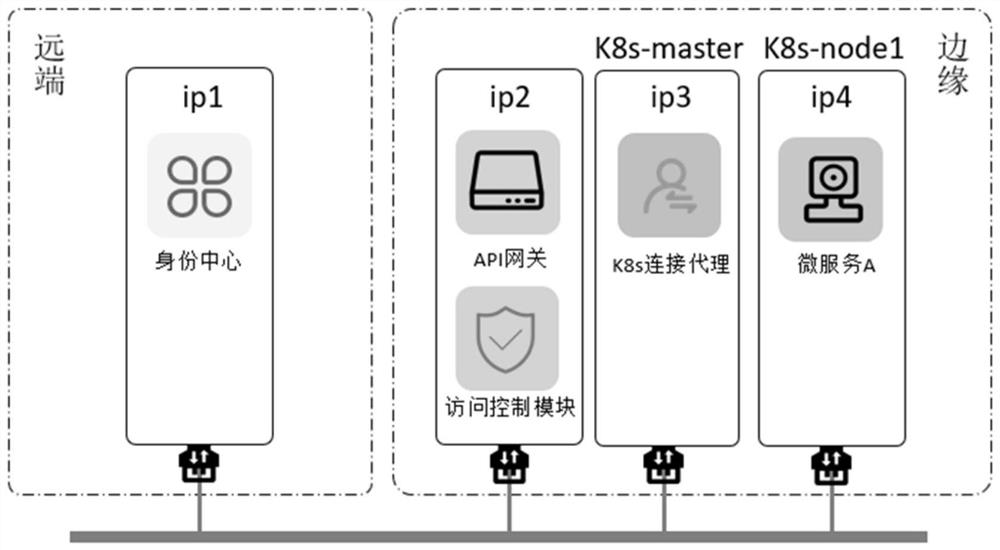
[0122] Such as Figure 4 As shown in , the user initiates an access request to the microservice resource Pod, and the process is as follows:
[0123] After the user passes the JWT token verification of the gateway;
[0124] The request will be forwarded to the interface for reading Pod details in the system ( / k8s / pods / detail);
[0125] The system parses the two parameters of the desired Pod's namespace (namespace) and name (podName) carried in the request parameter;
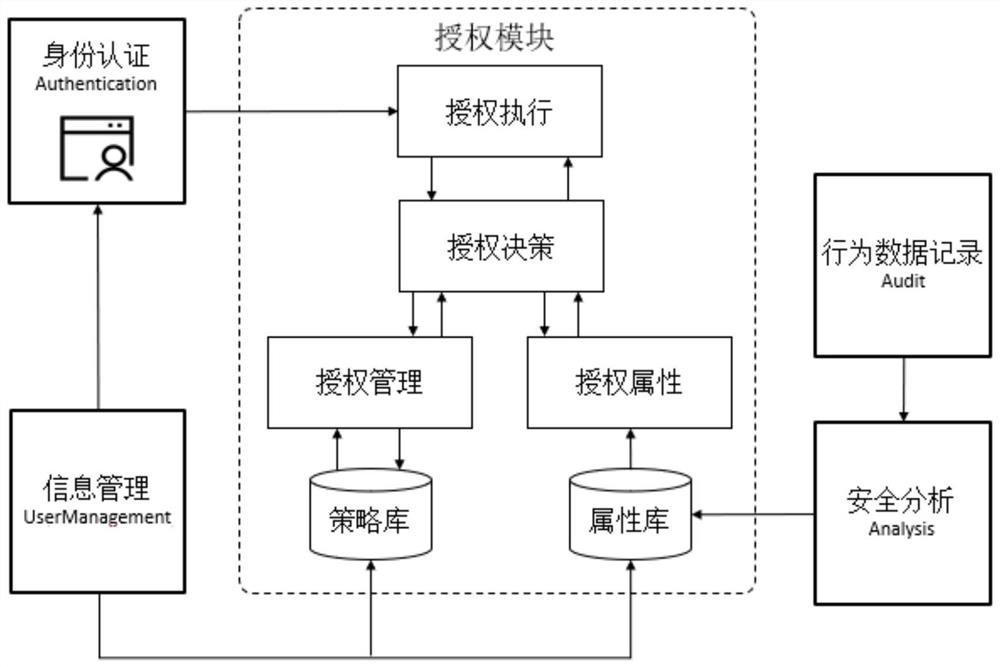
[0126] The system will query the resource_attr table in the database according to the Pod name to obtain the two values of the resource's danger level (dangerLevel) and security level (securityLevel), and query the user's two attribute values in attributes (attributes).
[0127] If the user's risk factor is higher than the microservice resource, or the user's security level is lower than the resource, the system will reject the user's request;
[0128] After the user passes the attribute verification of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com