Zero-knowledge proving method and system based on SM2 algorithm
A zero-knowledge proof and algorithm technology, applied in the field of information security, to achieve the effect of smooth execution, reduced data transmission, and small amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
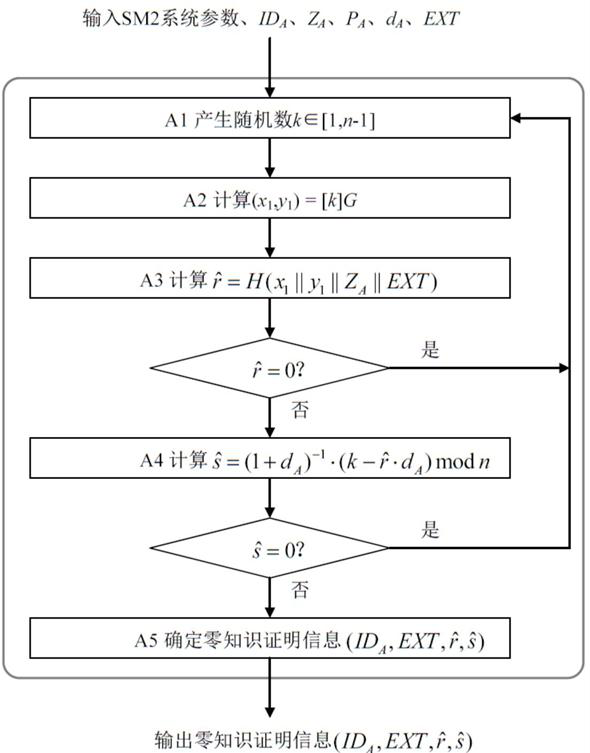
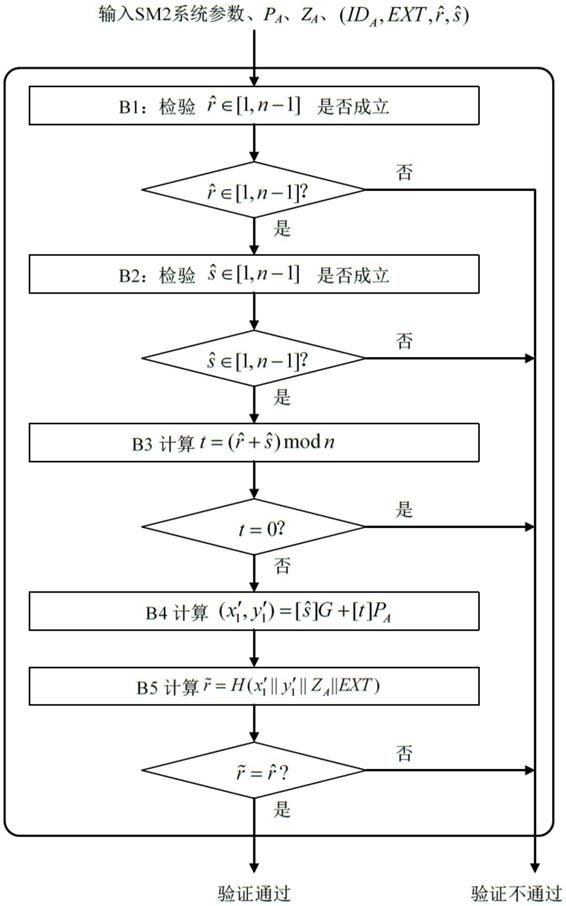
[0057] First illustrate the sign, abbreviation and symbol used in the present invention:
[0058] A : Prover User A 。
[0059] B : verifier user B 。
[0060] a , b : finite field F q elements in , which define the finite field F q an elliptic curve on E .
[0061] d A : User A's private key.
[0062] E ( F q ): finite field F q upper elliptic curve E All rational points of (including points at infinity or zero O ) set consisting of.
[0063] F q :Include q A finite field of elements.
[0064] G : elliptic curve E A base point of whose order is a prime number.
[0065] H (): Cryptographic hash function, which can be selected as the SM3 algorithm. For details of the SM3 algorithm, refer to GB / T 32905 "Information Security Technology SM3 Cryptographic Hash Algorithm".
[0066] ID A : The distinguishable identifier of user A.
[0067] mod n :mold n operation. For example, 23 mod 7 = 2.
[0068] n : G point order ( n yes# E ( F q ) prime ...
Embodiment 2
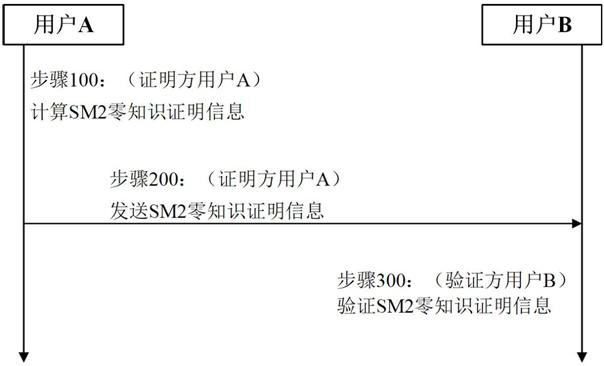
[0138] In order to realize the zero-knowledge proof method based on the SM2 algorithm of embodiment 1, such as Figure 4 As shown, this embodiment proposes a zero-knowledge proof system based on the SM2 algorithm, including: a connected zero-knowledge proof information generation subsystem and a zero-knowledge proof information verification subsystem;
[0139] The zero-knowledge proof information generation subsystem is deployed on the prover, and is used for the prover user A to generate and send SM2 zero-knowledge proof information; specifically, the zero-knowledge proof information generation subsystem includes a first control scheduling module and a communication with the second A first hash module, a first SM2 module, a first transmission data codec module and a random number generator module connected to a control scheduling module;
[0140] The functions of each module in the zero-knowledge proof information generating subsystem are as follows:
[0141] Random Number G...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com