A blockchain-based access control method that can hide policies and attributes
An access control and blockchain technology, applied in the field of access control based on blockchain-based hidden policies and attributes, can solve privacy threats, expose user identities, etc., and achieve the effect of enhancing robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The specific implementation process of the present invention will be further described below with reference to the accompanying drawings.
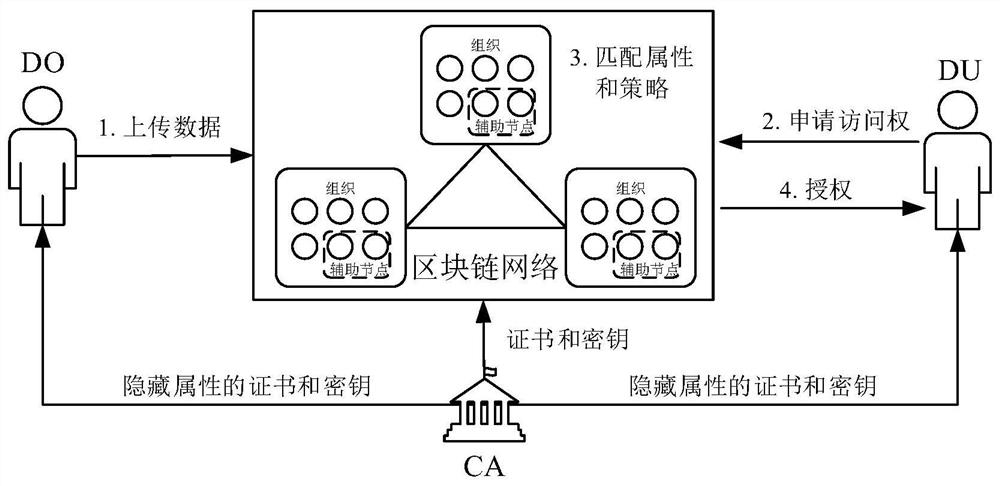
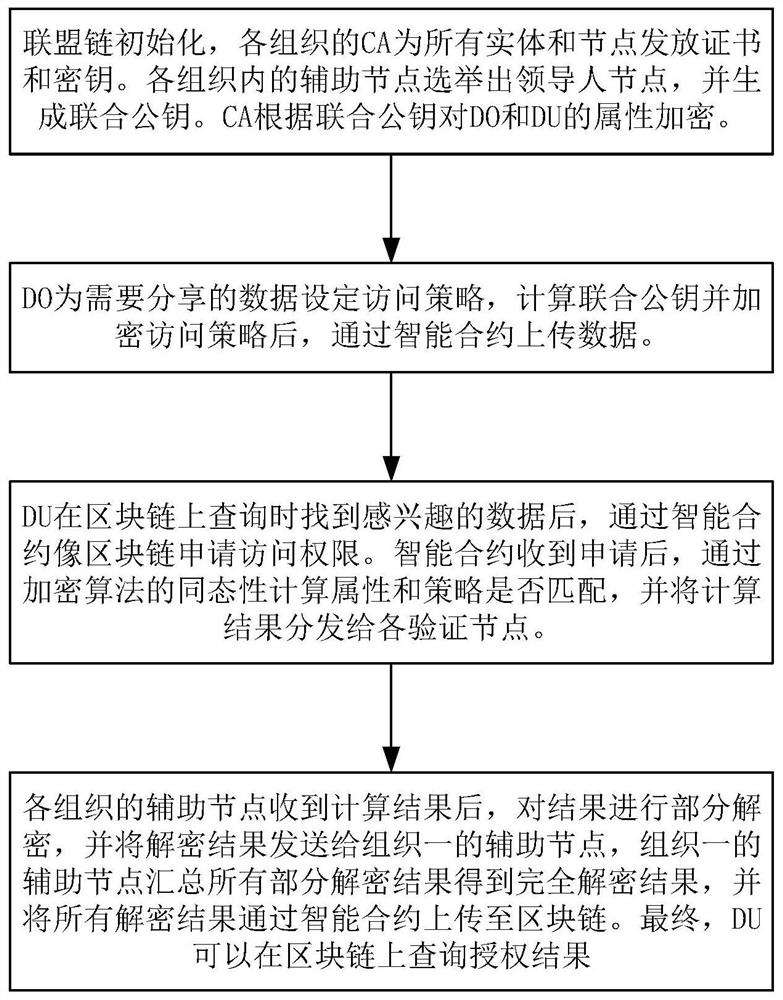
[0040] A blockchain-based access control method that can hide policies and attributes, comprising the following steps:
[0041] Step 1: Consortium blockchain initialization.
[0042] Specifically, it includes the following steps:
[0043] Step 1.1: Consortium formation.
[0044] Multiple organizations form alliances to jointly build blockchain networks. Any node that wants to join the blockchain network needs to apply for a certificate issued by its organization's CA. This certificate is associated with the node's public-private key pair (BPK, BSK), and the node can use the private key to sign the transactions it sends. .
[0045] Step 1.2: Generate joint public key.
[0046] The administrator of each organization selects at least two nodes within the organization as secondary nodes, which should have sufficient resources to pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com