Network active defense method and device based on deceptive artificial intelligence
A technology of active defense and artificial intelligence, applied in electrical components, transmission systems, etc., can solve the problems of data security is difficult to guarantee, network attack defense cannot play a good effect, etc., to improve security and avoid system obstruction. stagnation, the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
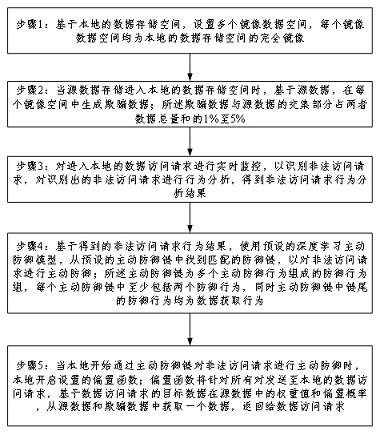
[0035] Such as figure 1 As shown, the network active defense method based on deceptive artificial intelligence, the method performs the following steps:
[0036] Step 1: Based on the local data storage space, set multiple mirror data spaces, each mirror data space is a complete mirror image of the local data storage space;
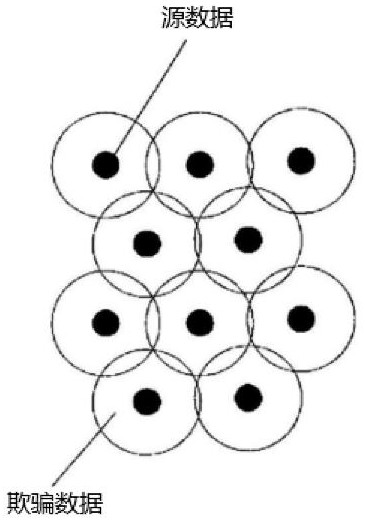
[0037] Step 2: When the source data storage enters the local data storage space, generate spoofed data in each mirrored data space based on the source data; the intersection of the spoofed data and the source data accounts for 1% of the total sum of the two data to 5%;
[0038] Step 3: Real-time monitoring of incoming data access requests to identify illegal access requests, conduct behavioral analysis of identified illegal access requests, and obtain illegal access request behavior analysis results;
[0039] Step 4: Based on the obtained illegal access request behavior results, find a matching defense chain from the preset active defense chains to activ...
Embodiment 2
[0045] On the basis of the previous embodiment, the mirrored data space is connected in parallel with the local data storage space; at the same time, the mirrored data spaces are connected in parallel.
Embodiment 3
[0047] On the basis of the previous embodiment, the step 2 is based on the source data, and the method for generating fraudulent data in each image data space performs the following steps: Randomly select part of the data in the source data as the intersection of the fraudulent data and the source data For the part, the data other than the intersection part in the source data is used to generate a fraudulent part using the data mapping equation; the data mapping equation is expressed by the following formula: Among them, K n is the generated fraudulent part, n value represents the number of generated fraudulent data; A represents the data other than the intersection part in the source data;
[0048] Specifically, after breaking through a host, an attacker often uses this host as a base to attack other hosts (to conceal its intrusion path and avoid leaving clues). They can use network monitoring methods to try to break into other hosts in the same network; they can also att...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com