Network terminal access control method based on bypass control technology
An access control and network terminal technology, applied in the field of network security, can solve problems such as inability to prevent attacks and risks, network terminal security threats, etc., and achieve good network adaptability, good practicability, and high reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
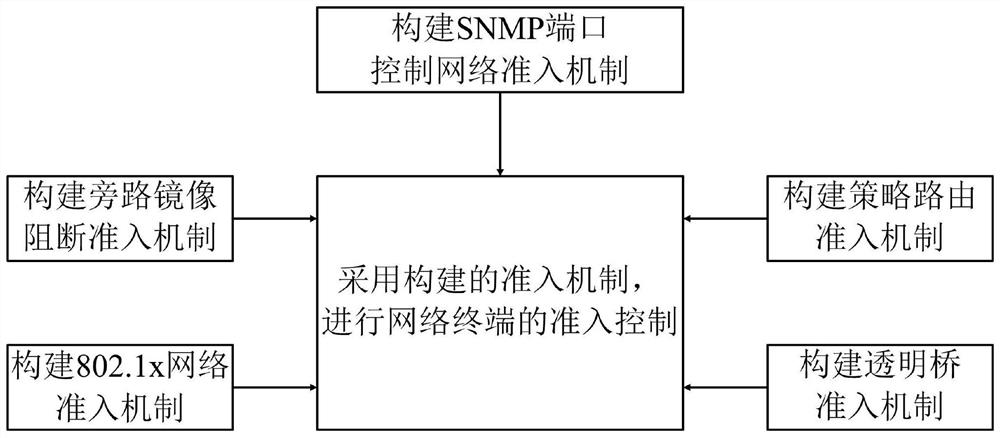
Image
Examples
Embodiment 1
[0029] The compatibility of the desktop management system needs to be compatible with the company’s desktop terminal management system to ensure that the log information is finally sent to the network and information security risk monitoring and early warning platform through the desktop management system. The access client must meet the technical specifications for the interface with the desktop client, including:
[0030] (1) Access the client to detect the running status and version information of the desktop management client;
[0031] (2) The access client reports its own running status and version to the desktop management client;
[0032] (3) The access client pushes the terminal user prompt message to the desktop management client, and the desk management client performs a pop-up window prompt;
[0033] (4) The access client obtains the terminal registration information in the desk management client,
[0034] (5) The access management terminal must meet the technical ...
Embodiment 2
[0037] Log management, local access log record storage, storage time not less than 6 months, access log record query; query based on MAC address, IP address, fingerprint, user, department information, at least according to device IP, MAC address, department Sorting and displaying results; log management of illegal private connection, illegal counterfeiting, and network-to-network abnormal events, including precise query and fuzzy query, and providing a response handling interface to block suspicious terminals at the port level; abnormal behavior of HUB and layer-2 devices log management, and can provide a response and disposal interface to block suspicious terminals at the port level; log management of terminal security baseline network access inspection status, including precise query and fuzzy query, and statistics of device network access based on time, department, and operating system dimensions. Report the access log and terminal security baseline inspection log to the man...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com