File security protection method and device
A security protection and file technology, applied in the field of information security, can solve problems such as file information leakage, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
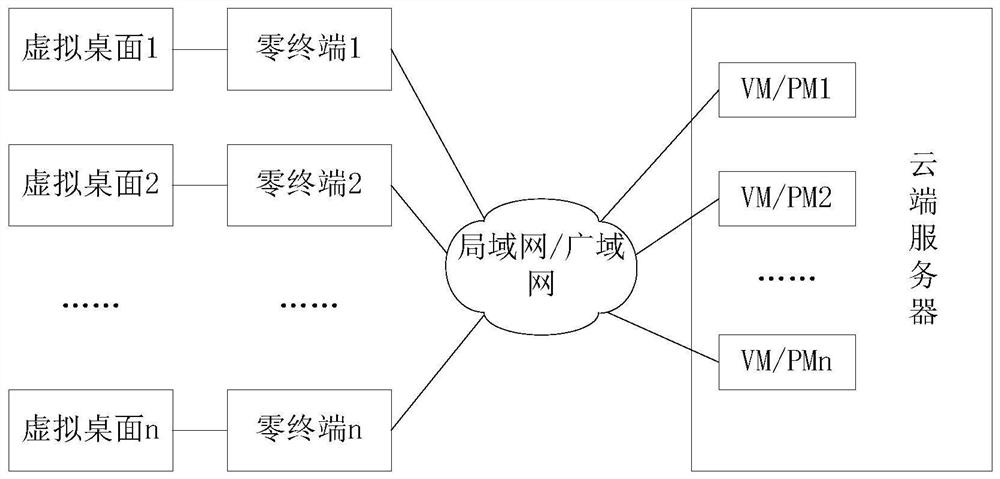
[0023] In the cloud office system, based on VGTP (image lossless transmission protocol), it mainly includes zero terminal (built-in VGTP-R terminal, referred to as R terminal) and cloud server (built-in VGTP-S terminal, referred to as S terminal). Among them, the R terminal is used to receive the virtual desktop image from the cloud, and at the same time reversely transmit the local mouse and keyboard information to the cloud, and the cloud injects it into the virtual desktop corresponding to the current R terminal. Generated by the VM / PM allocated by the terminal; the S terminal is an image acquisition and encoding module running in the cloud virtual operating system, and is also responsible for the injection function of user input data. The cloud server is generally based on the IAAS (Infrastructure as a Service, infrastructure as a service) architecture, which is a server with a strong virtual host function, which can provide multiple VM / PM management functions through the h...
Embodiment 2
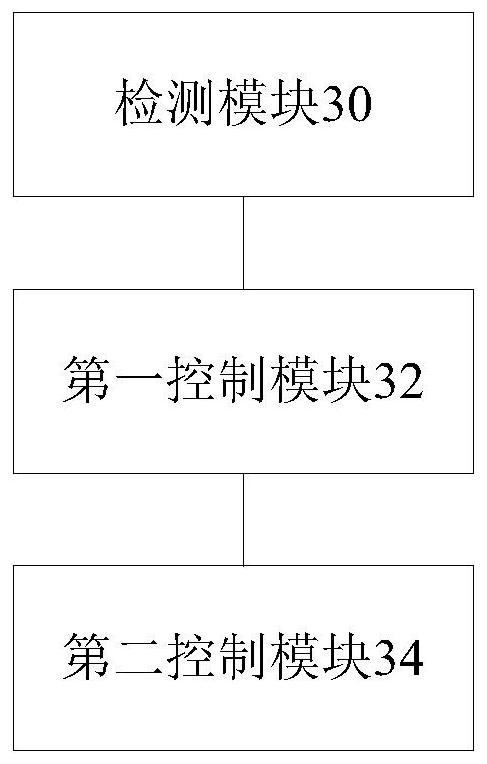
[0045] According to the embodiment of the present application, there is also provided a file security protection device for implementing the above-mentioned file security protection method, each module in the file security protection device corresponds to the implementation steps of the file security protection method in Embodiment 1 one by one . Specifically, as image 3 As shown, the device includes a detection module 30, a first control module 32 and a second control module 34, wherein:
[0046] The detection module 30 is configured to detect the operation information of the zero terminal.
[0047] Specifically, the main body of the file security protection device is usually a target server, which can be a virtual machine or a physical machine running on a cloud server, and a detection module is installed inside it to detect user operation information uploaded by the zero terminal, so as to determine Whether the current user is reading the shared file, so as to set the co...
Embodiment 3
[0063] According to an embodiment of the present application, a non-volatile storage medium is also provided, the non-volatile storage medium includes a stored program, wherein, when the program is running, the device where the non-volatile storage medium is located is controlled to perform the above-mentioned file security protection method.
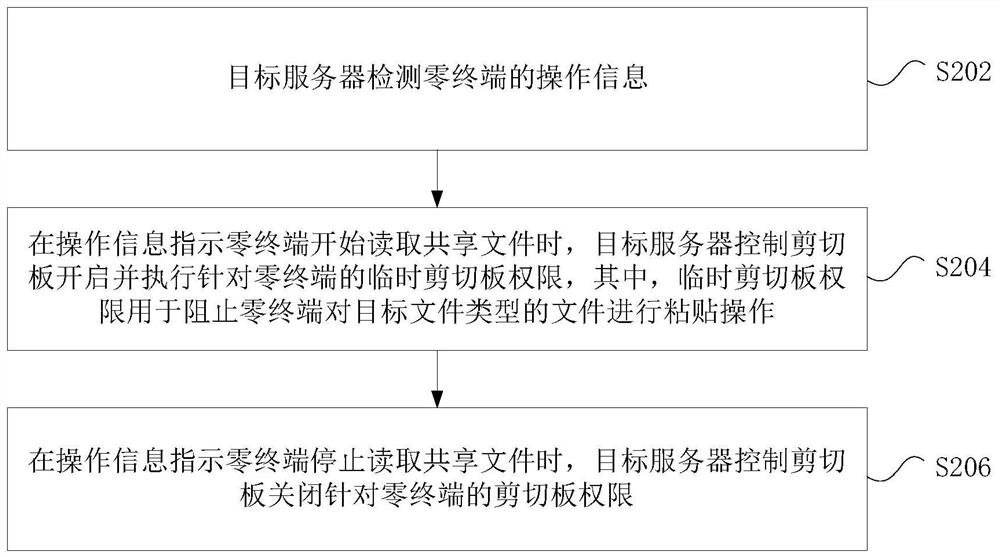
[0064] Optionally, when the program is running, the device where the non-volatile storage medium is located is controlled to perform the following steps: the target server detects the operation information of the zero terminal; when the operation information indicates that the zero terminal starts to read the shared file, the target server controls the clipboard Enable and execute the temporary clipboard permission for the zero terminal, where the temporary clipboard permission is used to prevent the zero terminal from pasting the target file type; when the operation information indicates that the zero terminal stops reading the shared f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com