Data access control method of DDS distributed system
A data access control and distributed system technology, applied in digital data authentication, digital data protection, electronic digital data processing, etc., can solve the problem of high message complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
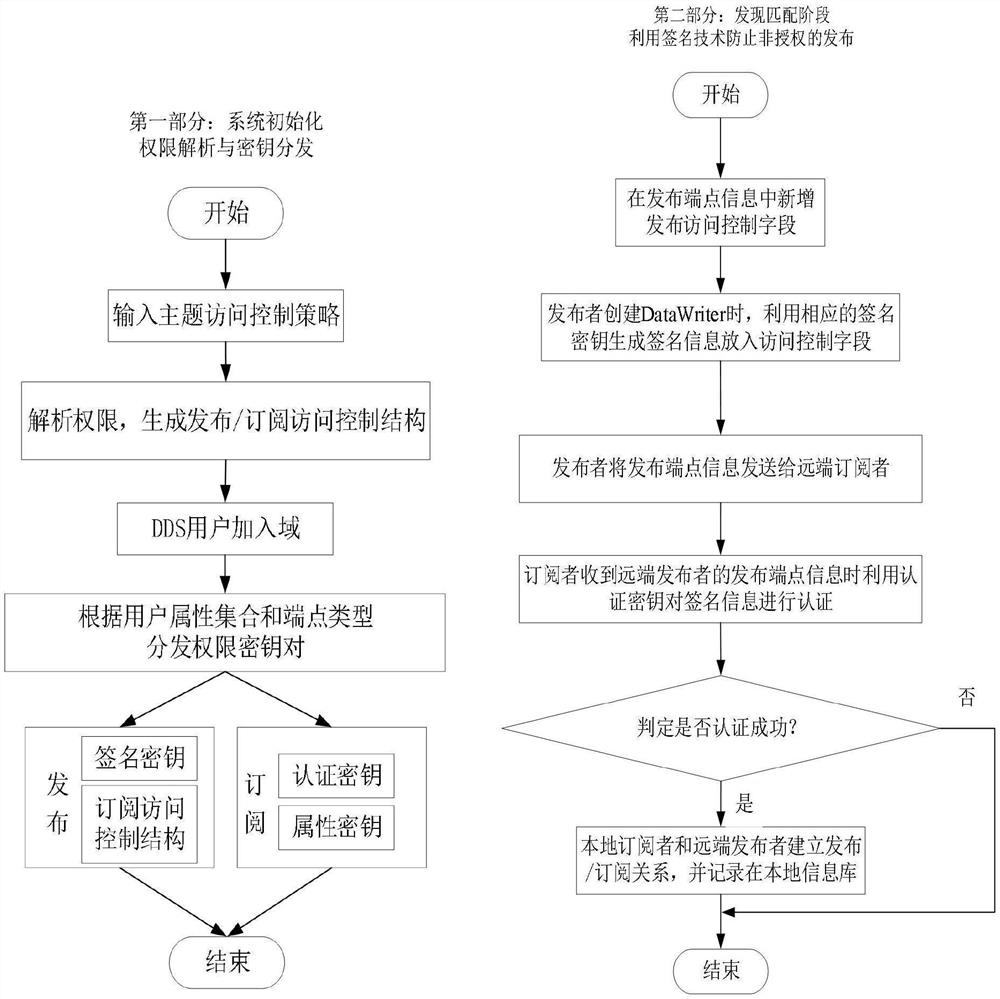
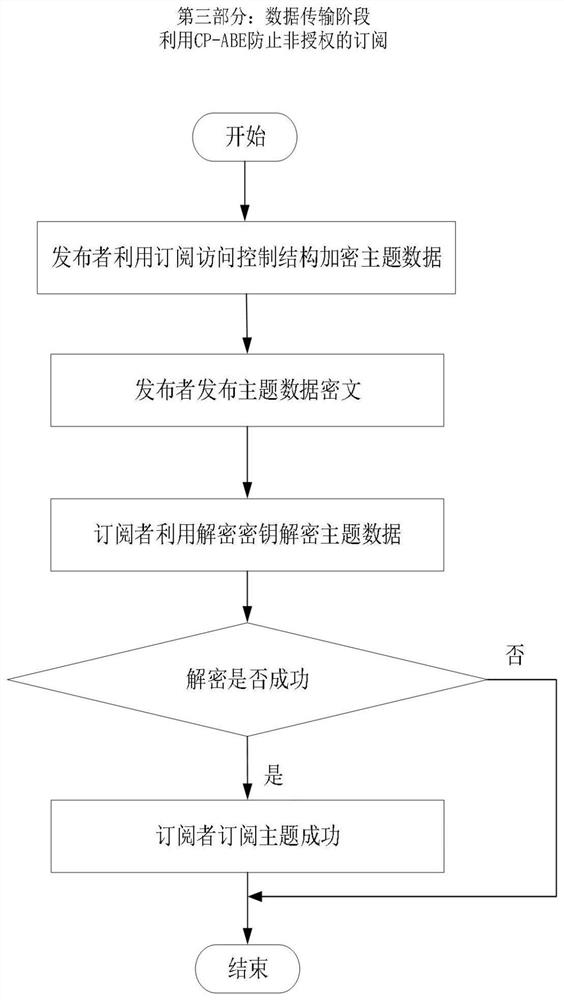
[0036] Example: such as figure 1 Shown, a kind of data access control method of DDS distributed system, comprises the following steps:
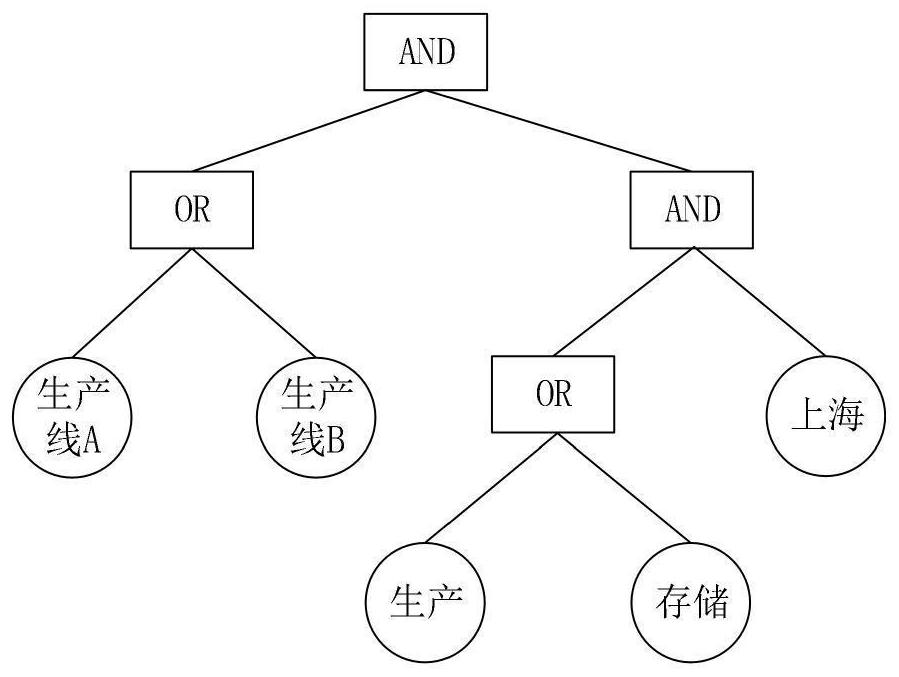
[0037] First, the access control policy of the DDS data management center for a single topic (Topic1) in the system data resources (see Table 1, where 1 / 2 means that only one of the two attributes is satisfied, and 1 / 1 means that there is only one attribute and requires Satisfied) to analyze and generate the release access control structure T of topic Topic1 p1 and subscribe to the access control structure T s1 Respectively as figure 2 and image 3 shown. At the same time, the DDS data management center generates a signature authentication key pair {GK1 , VK 1}.
[0038] Table 1 Topicl access control policy
[0039]
[0040] Secondly, DDS users user1, user2 (publisher), user3, user4 (subscriber) in the distributed system submit user attribute sets to the data management center, as shown in Table 2. The DDS data management center g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com