A Logical Encryption Method for Integrated Circuit Function Output Protection
An output protection, integrated circuit technology, applied in the field of logic encryption of integrated circuit function output protection, can solve the problems of many iterations, long time, long encryption time, etc., to achieve the effect of improving the degree of confusion and reducing the number of encryption iterations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings.
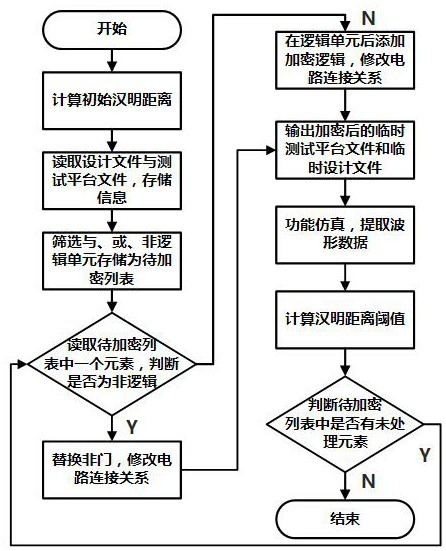
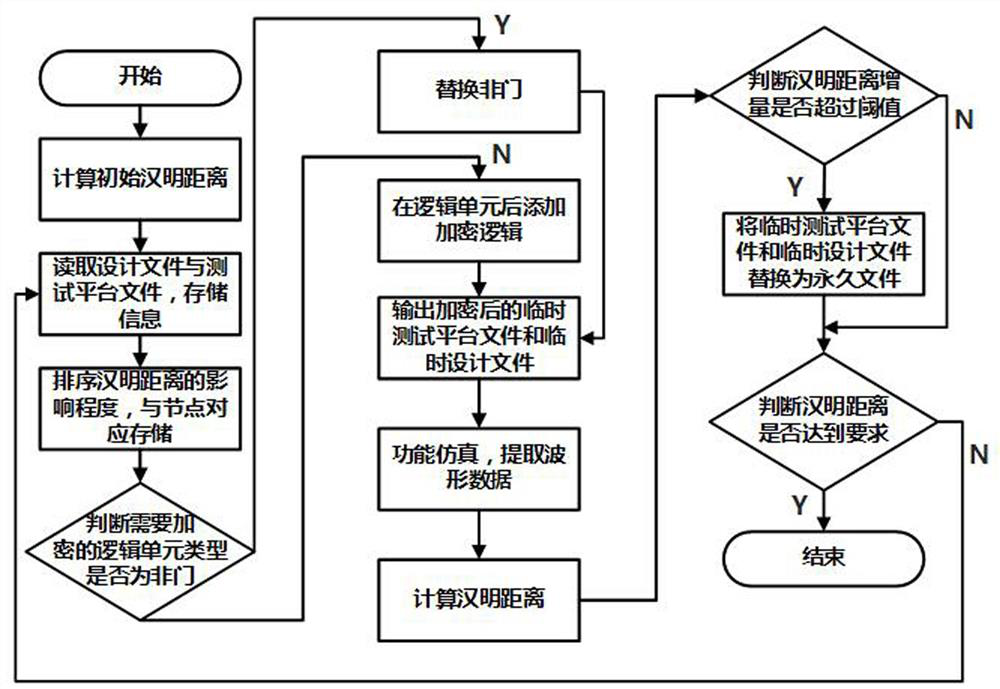
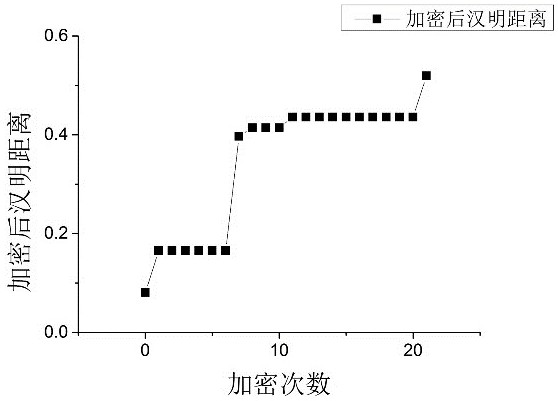
[0032] A kind of logical encryption method for the protection of integrated circuit function output proposed by the present invention, the main purpose is to prevent an attacker from using the output to crack the key or insert a hardware Trojan horse that leaks information after the circuit is logically encrypted. The protected circuit design file can be a circuit that has been processed by logic encryption before, and the circuit design file mentioned in the present invention and the unencrypted circuit design file can be a circuit file that has been inserted into a key through logic encryption before. Contains AND, OR, NOT gate logic units.
[0033] The present invention mainly can be divided into two steps:
[0034] like figure 1 As shown, in the first step, in order to focus the processing on the circuit nodes that have a greater impact on the output Hamming dist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com