Social network graph acquisition method and system and electronic equipment
A technology of social network and acquisition method, applied in the fields of systems and electronic devices, and acquisition method of social network graph, can solve the problem that attackers cannot analyze and identify target objects, social network graphs have low privacy, and are easy to destroy the structural attributes of social network graphs. and other issues to achieve the effect of maintaining structural properties, improving privacy and security, and improving usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
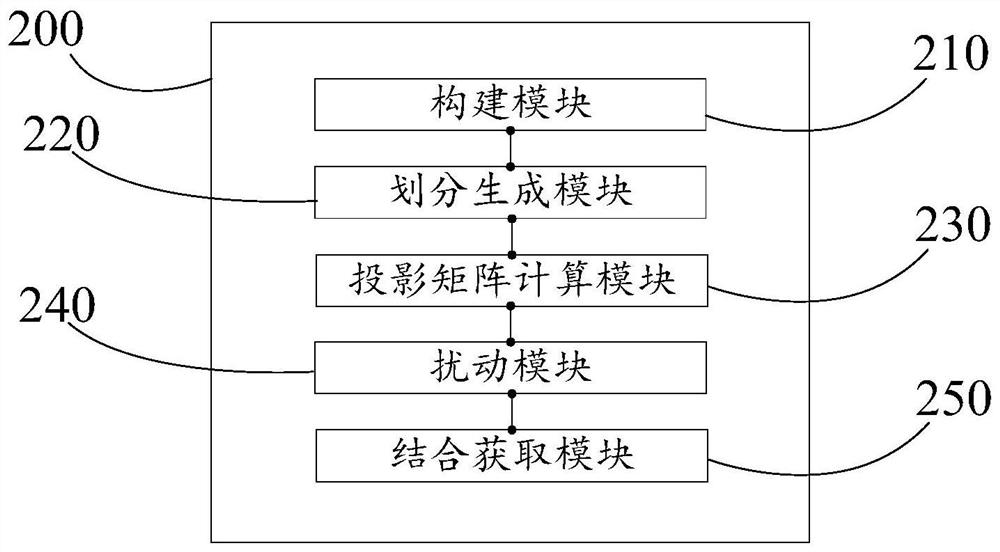
[0047] Such as figure 1 As shown, a method for obtaining a social network graph in an embodiment of the present invention includes the following steps:
[0048] S1. Construct an undirected graph according to the social network data of multiple preset users, wherein the nodes in the undirected graph represent the preset users, and the edges between any two nodes in the undirected graph represent the There is a social relationship between the two preset users corresponding to the two nodes;
[0049] S2. Perform community division on the undirected graph to obtain multiple subgraphs, and generate an adjacency matrix for each subgraph;
[0050] S3. Calculate the projection matrix of the adjacency matrix of each subgraph according to the adjacency matrix of each subgraph and the first preset Gaussian matrix corresponding to each subgraph;
[0051] S4. Using the second preset Gaussian matrix corresponding to each sub-image to perturb each projection matrix to obtain a perturbed proj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com