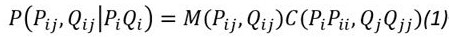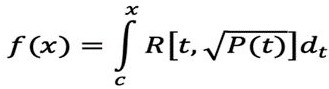Signature identification-based digital certificate authentication method
A technology for digital identification and signature authentication, which is applied in the field of information security and can solve problems such as fraudulent use of identities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
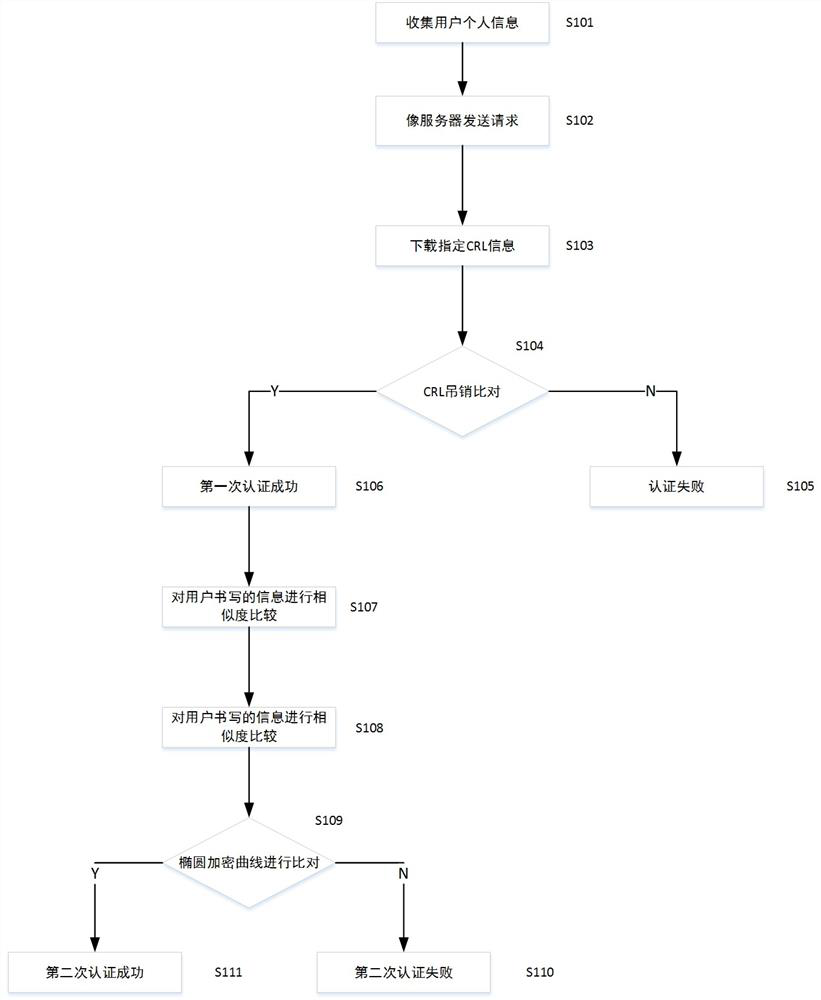
[0029] figure 1 A flow chart of an authentication method based on signature recognition digital certificate according to an exemplary embodiment of the present invention is shown.
[0030] First, collect the feature matrix of the signature information specified by the user according to the above method in S101.
[0031] Log in the designated server address in S102.
[0032] In S102, the server downloads the specified CRL file from the specified publishing website.
[0033] At S103 the server accesses the CR1 file to check the validity of the certificate.
[0034] In S104, if the information of the certificate is recorded in the specified CRL information, the expiration of the certificate ends.
[0035] After the verification in S105 is successful, the first verification is successful.
[0036] In S106, the user writes and inputs the specified information, and performs matrix similarity calculation through the above-mentioned algorithm,
[0037]
[0038] After several i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com