Attribute-based encryption and block chain combined trusted data access control scheme
A technology of data access control and attribute-based encryption, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problems of blockchain storage bottleneck, weak access control capability, blockchain occupation, etc., to ensure confidentiality security and integrity, guaranteeing confidentiality, and relieving storage pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings, wherein the symmetric encryption and decryption algorithm is exemplified by AES, and the hash algorithm is exemplified by the SHA256 algorithm:
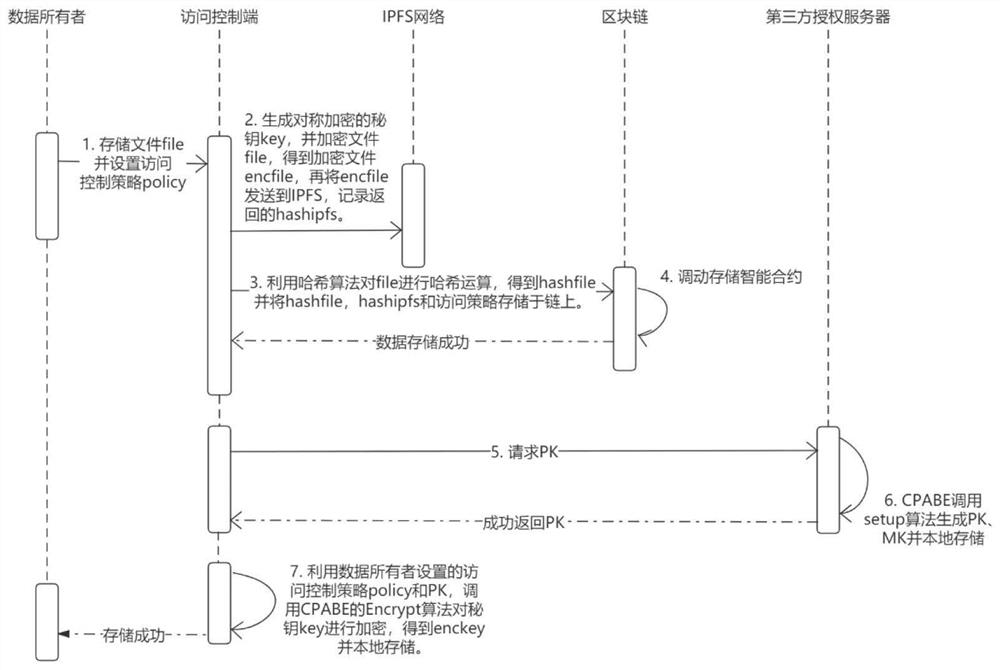
[0033] The first step: data storage, such as figure 1 As shown, the specific processing is as follows:
[0034] Step 101: the data owner Owner selects the file file to be stored, and sets the access control strategy policy of the file;
[0035] Step 102-1: The Owner has a unique key key of the symmetric encryption algorithm. If the Owner has not previously generated a key key, the access control end will call the key generation algorithm of the symmetric encryption to generate the Key of the Owner. The key generation method is: key = AES. Gen(Owner);
[0036] Step 102-2: The access control terminal invokes the encryption algorithm of symmetric encryption to encrypt the file file to obtain the encrypted file encfile....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com