Cloud computing-oriented organization-label access control method
An access control and cloud computing technology, applied in the field of network security, can solve problems such as role flooding, achieve the effect of fine-grained improvement, easy implementation, and enhanced privacy protection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
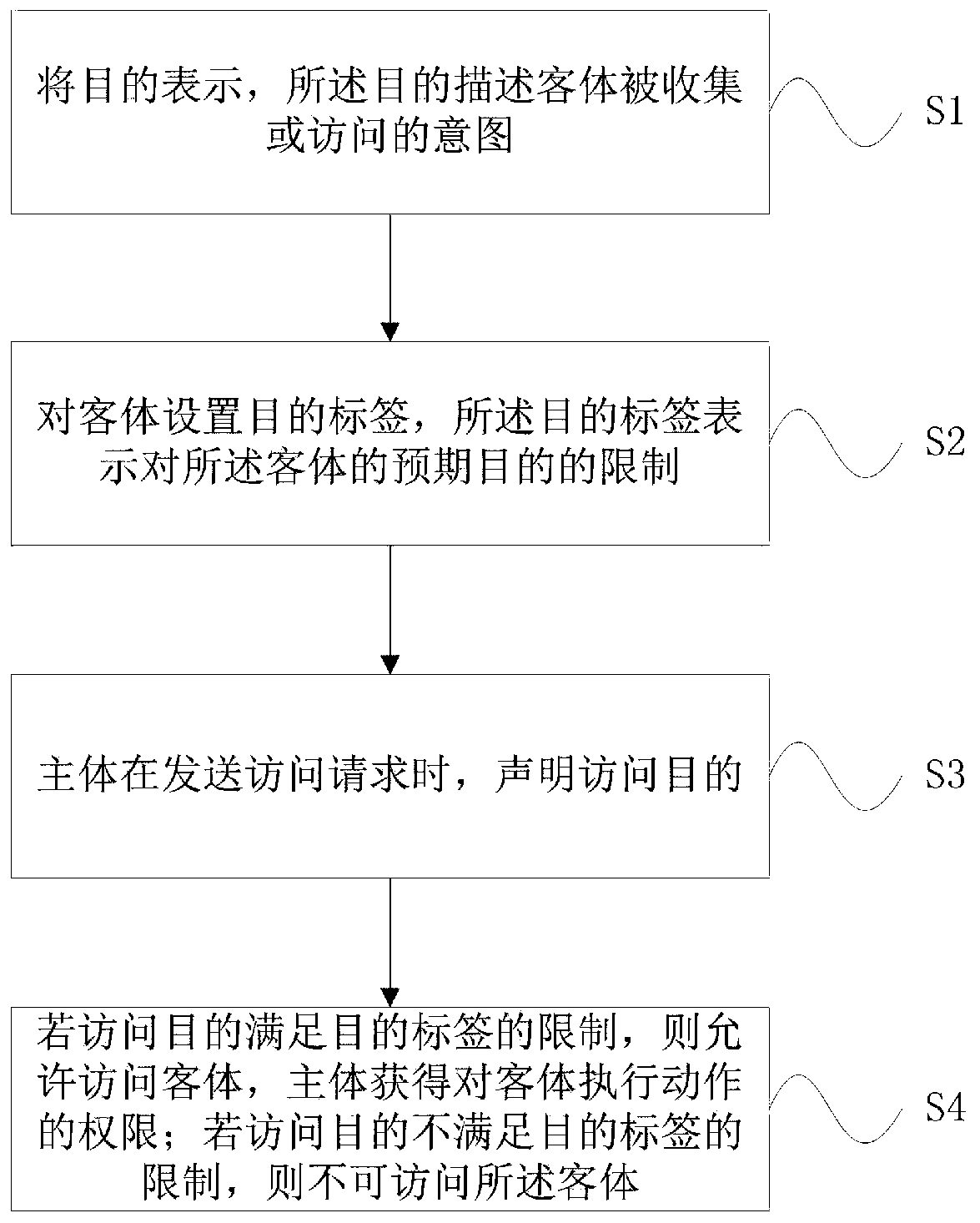
[0050] This embodiment provides a cloud computing-oriented organization-label access control method, such as figure 1 , including the following steps:
[0051] S1: Indicate the purpose, which describes the intention for the object to be collected or accessed;
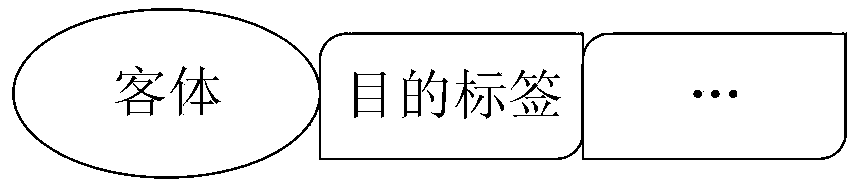
[0052] S2: Set the purpose label on the object, such as figure 2 , the purpose tag represents a restriction on the intended purpose of the object;
[0053] S3: The subject declares the purpose of the access when sending the access request;
[0054] S4: If the access purpose meets the restriction of the purpose tag, the object is allowed to be accessed, and the subject obtains the authority to perform actions on the object; if the access purpose does not meet the restriction of the purpose tag, the object cannot be accessed.
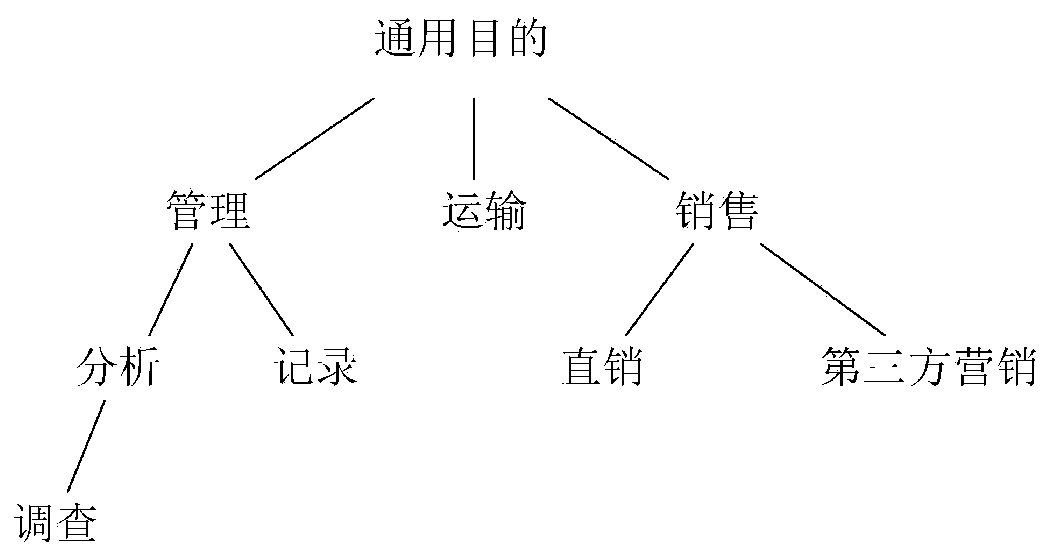
[0055] In a specific example, such as image 3 In the above-mentioned purpose tree, if the purpose tag set for the object is a binary group (management, sales), it indicates that the object’s...
Embodiment 2
[0057] This embodiment provides a kind of Or-LBAC model (organization-label access control model), such as Figure 5 .
[0058] In the Or-LBAC model, the subject declares its own access purpose while sending out the access request, and the data resource owner sets a label indicating the expected purpose of the resource for each data item (object). In the authorization process, only when the subject satisfies the pre-set access policy and the access purpose conforms to the predefined expected purpose of the object, the subject can access the object, that is, "what kind of subject can execute on what kind of object based on what purpose?" What kind of operation" access control requirements. The definitions involved in this model are as follows:
[0059] Organization (Organization): Generated by combining some active entities. In real life, a company or an institution can be regarded as an organization. An organization is represented by org.
[0060] Subject: The access requ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com