A message authentication method between an unmanned vehicle and a multi-mobile edge computing server
A technology of unmanned vehicles and edge servers, which is applied in the field of vehicle network communication security and can solve problems such as data integrity damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the embodiments.
[0053] As shown in Table 1, the meanings of the corresponding parameters and symbols in this implementation are as follows:
[0054] Table 1
[0055]
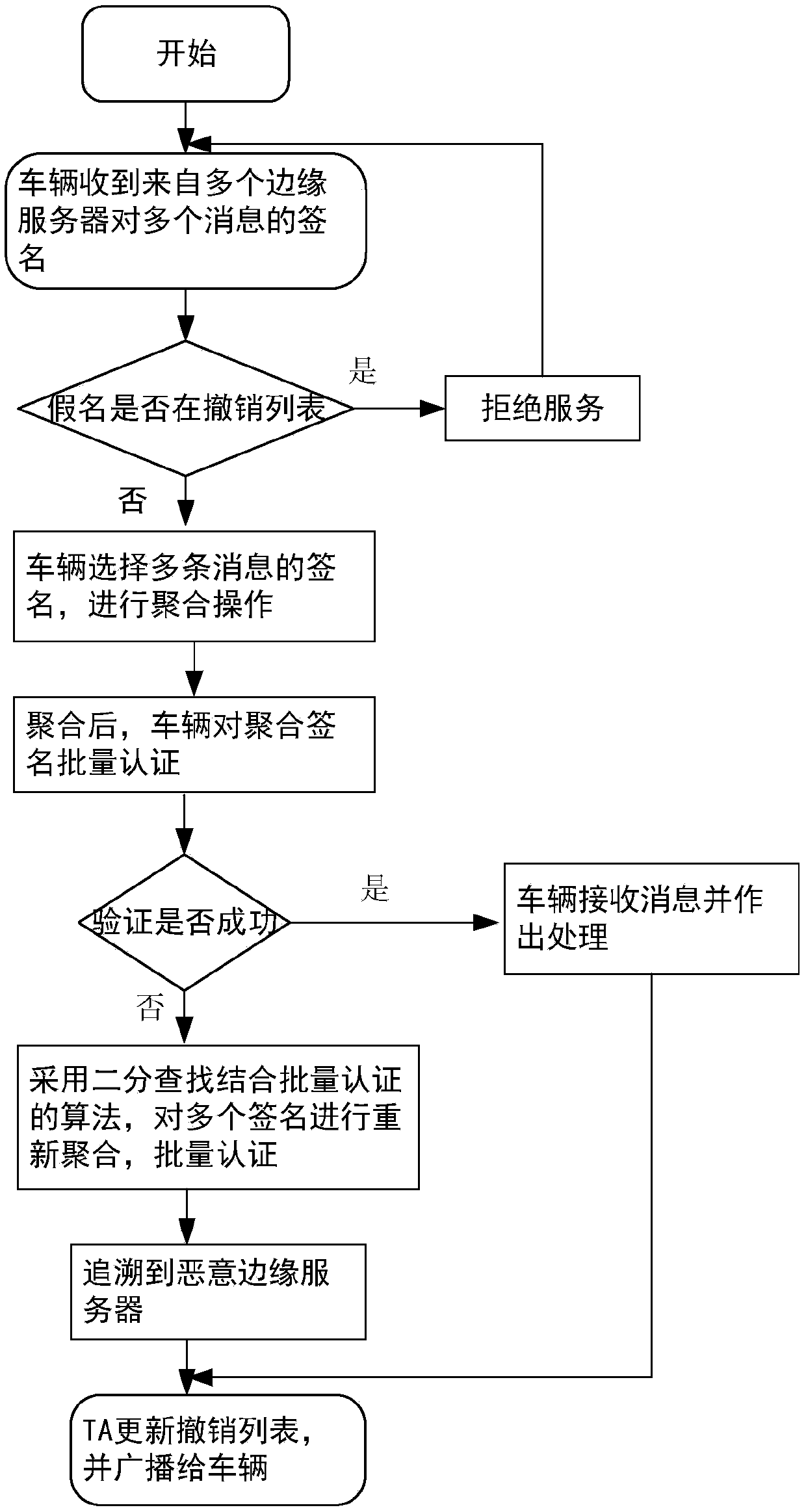
[0056] like figure 1 As shown, in the message authentication method between unmanned vehicles and multi-mobile edge computing servers in this embodiment, the network model mainly includes three types of participants, namely trusted entities (TAs), edge servers, and vehicles.
[0057] Among them, TA is a public parameter of the trusted entity generation system, which can generate semi-private keys and pseudonyms for edge servers according to their real identities. According to the results of the verification phase, TA can trace malicious edge servers; edge servers have certain storage and The edge server of computing power, as the edge server of edg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com