Industrial control security defense system
A security defense and industrial control technology, applied in general control systems, control/regulation systems, comprehensive factory control, etc., can solve the problems of endangering personnel health and public property safety, inability to quickly identify and eliminate crises, and increasing risks of industrial control systems, etc. problems, to achieve the effects of easy search and analysis, improvement of information security protection capabilities, and improvement of alarm response time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027]In order to make the objects, technical solutions, and advantages of the present invention, the present invention will be further described in detail below with reference to the accompanying drawings. It should be understood that these descriptions are merely exemplary and are not to limit the scope of the invention. Further, in the following description, a description of known structures and techniques is omitted to avoid unnecessary obscuring the concepts of the present invention.
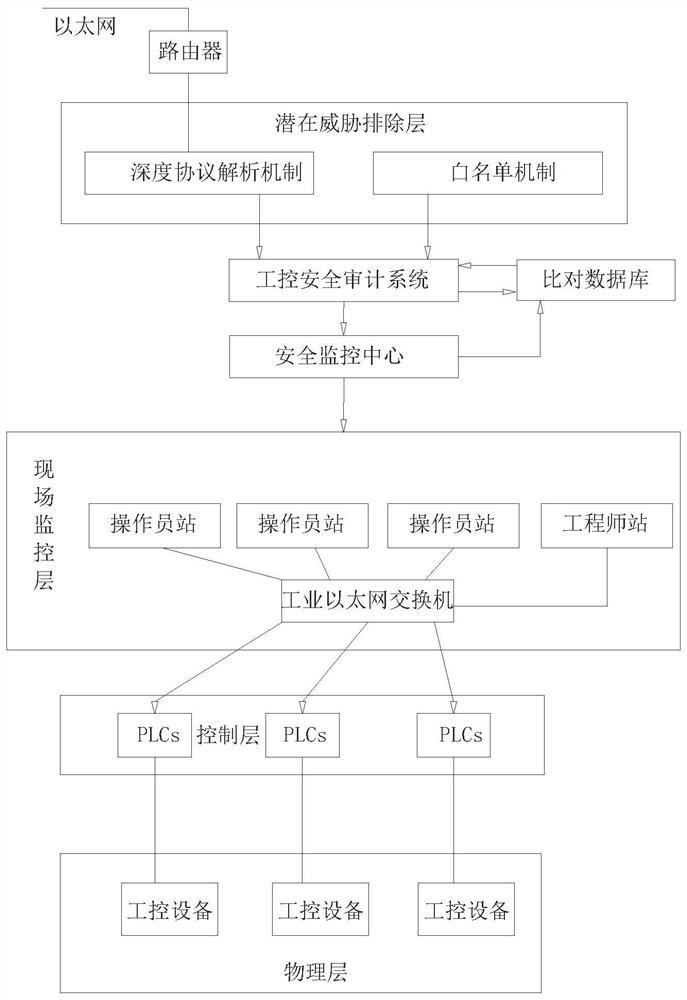
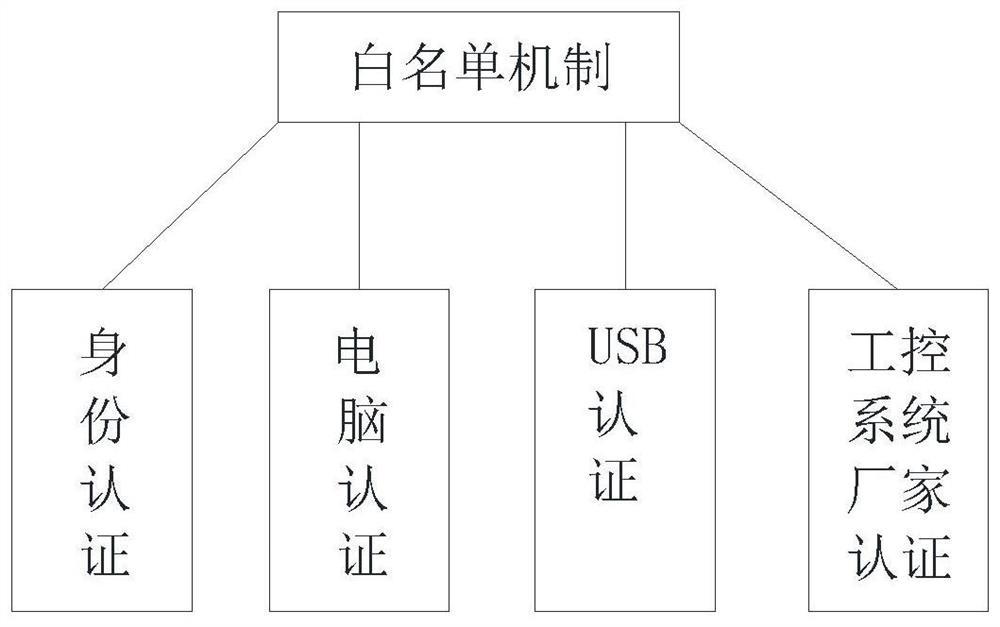
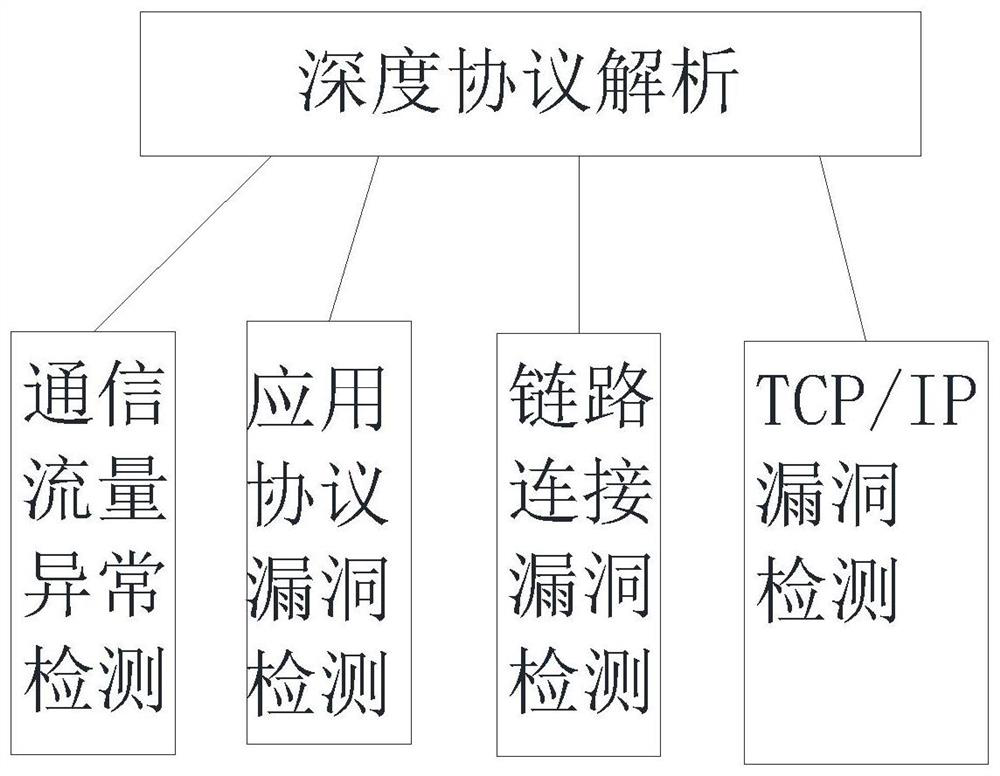
[0028]Such asFigure 1-4As shown, a industrial control safety defense system proposed by the present invention includes a potential threat exclusion layer, an industrial control security auditing system, a monitoring center, a field monitoring layer, a control layer, and a physical layer; potential threat exclusion layers include depth protocol parsing mechanisms and white List mechanism; field monitoring layer performs data exchange and behavior control over the control layer and physical layer by i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com