Computer-implemented method, computer program product and system for anomaly detection and/or predictive maintenance
An anomaly detection and computer technology, applied in testing/monitoring control systems, computer components, general control systems, etc., can solve the problem of limiting the universal applicability of real-time systems, not providing further clues to the investigation system, constraining the construction or training of network methods, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0317] Example 1: Predictive Maintenance of Turbofan Engines
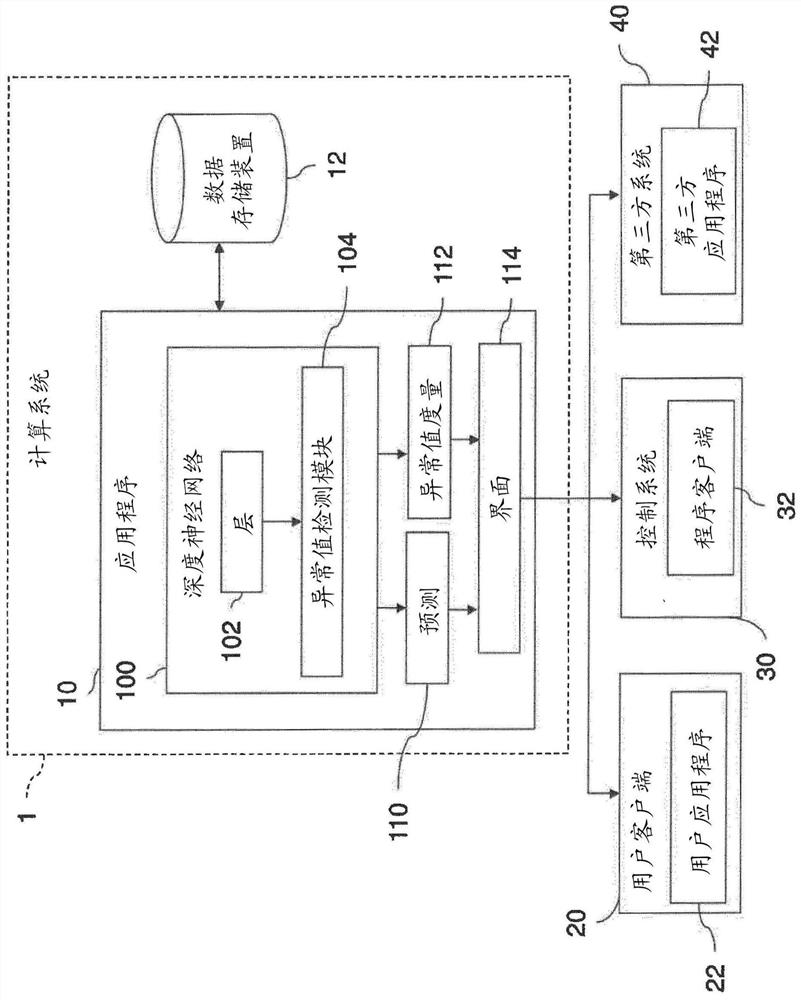
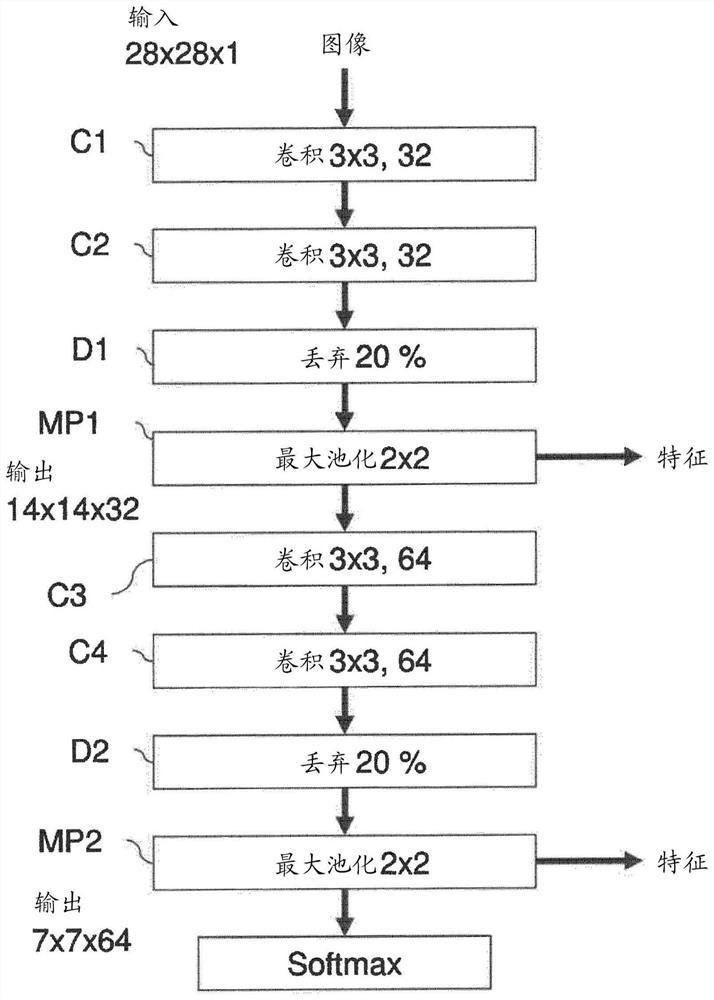
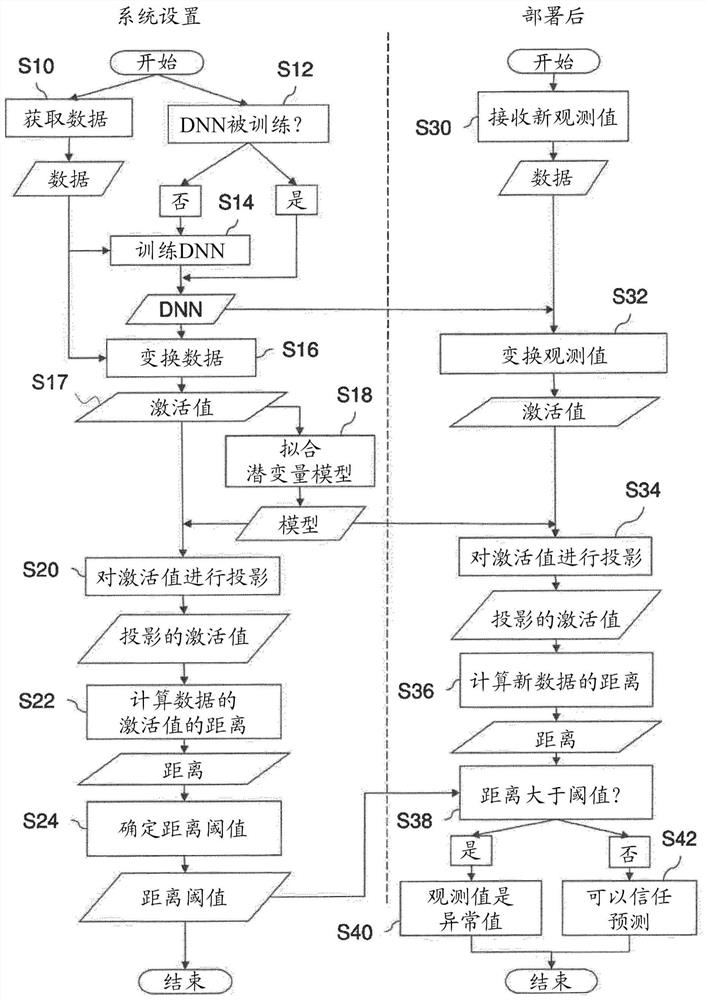
[0318] In some implementations, a CNN can be used as the deep neural network 100 for image analysis. However, the exemplary computing system 1 can also perform outlier detection to analyze data types other than images. For example, outlier detection of the exemplary computing system 1 may be performed for predictive maintenance tasks, wherein the condition of equipment in service is determined in order to predict when maintenance should be performed. This section presents experimental results on outlier detection for predictive maintenance of turbofan engines.
[0319] In this experiment, a turbofan engine degradation dataset provided by the Prognostics CoE of NASA Ames (Saxena A. and Goebel K., "Turbofan Engine Degradation Simulation Data Set", NASA Ames Prediction Data Repository (http: / / ti .arc.nasa.gov / project / prognostic-data-repository), 2008, NASA Ames Research Center, Moffett Field, CA). The dataset consi...
example 2
[0329] Example 2: Anomaly detection in the domain of cybersecurity
[0330] Another particularly effective example of the use of the invention in the field of predictive maintenance is its use in the field of network security. One way to use deep learning in cybersecurity is to detect obfuscated scripts (Hendler D, Kels S, Rubin A., Detecting Malicious PowerShell Commands Using Deep Neural Networks, in: 2018 Asian Computer and Communications Security Conference [Internet] Proceedings, New York, NY, USA: ACM, 2018 [Cited 29 August 2019], pp. 187-197, (ASIACCS'18); Available at: http: / / doi.acm.org / 10.1145 / 3196494.3196511).
[0331] Microsoft Corporation's PowerShell is a command-line tool and programming language that is installed by default on Windows computers and is commonly used by system administrators for a wide range of operational tasks. Symantec recently reported that cybercriminals are increasingly targeting PowerShell (PowerShell Threats Grow Further and Operate in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com