Intelligent security face recognition system
A security face and recognition system technology, applied in the field of intelligent security face recognition system, can solve problems such as inability to accurately identify identities, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
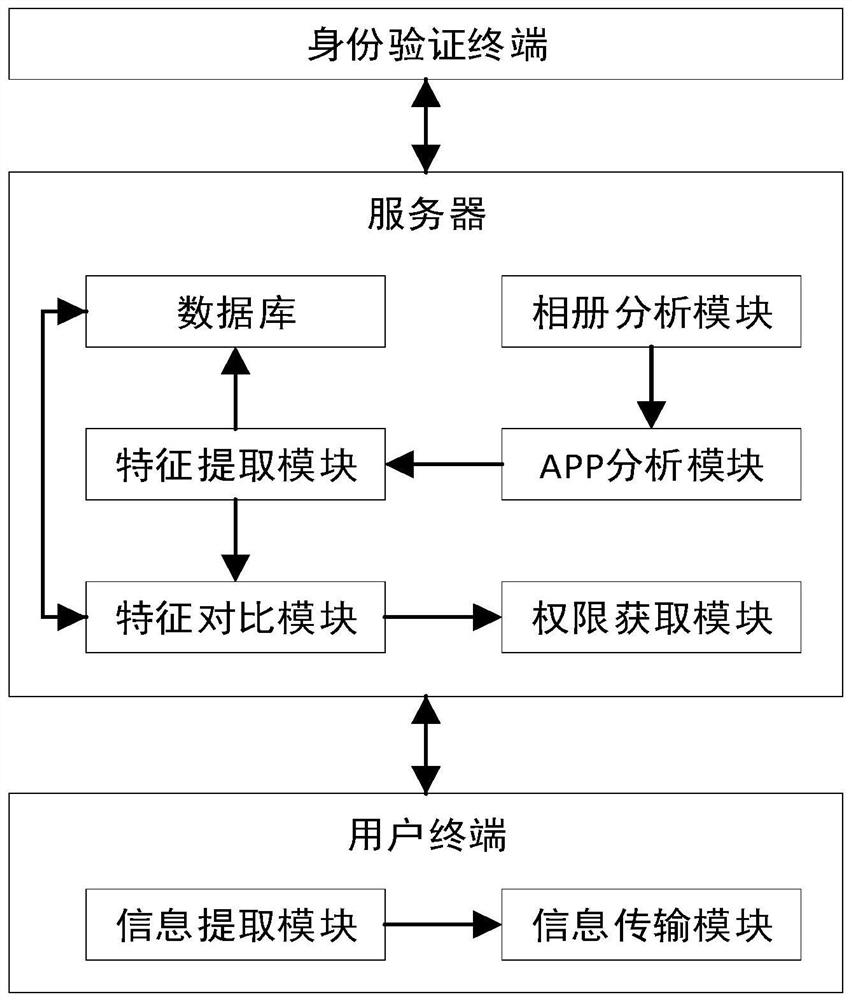
[0034] Intelligent security face recognition system, as attached figure 1 As shown in the figure, it includes an identity verification terminal, a server and a user terminal. In this embodiment, the identity verification terminal includes a camera set at the access control of the confidential department of the enterprise, and the face verification images of personnel entering and leaving the confidential department of the enterprise are collected through the camera. The user terminal is Smart devices that everyone carries with them, such as cell phones.
[0035] The server includes a database, a feature extraction module, a feature comparison module, a permission acquisition module, an album analysis module and an APP analysis module.
[0036] Before performing face recognition, it is necessary to collect the information of employees who have access to the confidential department of the enterprise. The identity verification terminal is used to collect the standard face image ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com