Database event association method and auditing system
An event correlation and database technology, which is applied to other database retrieval, transmission systems, network data query, etc., can solve problems that need to be further improved, and achieve the effect of improving the effectiveness of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
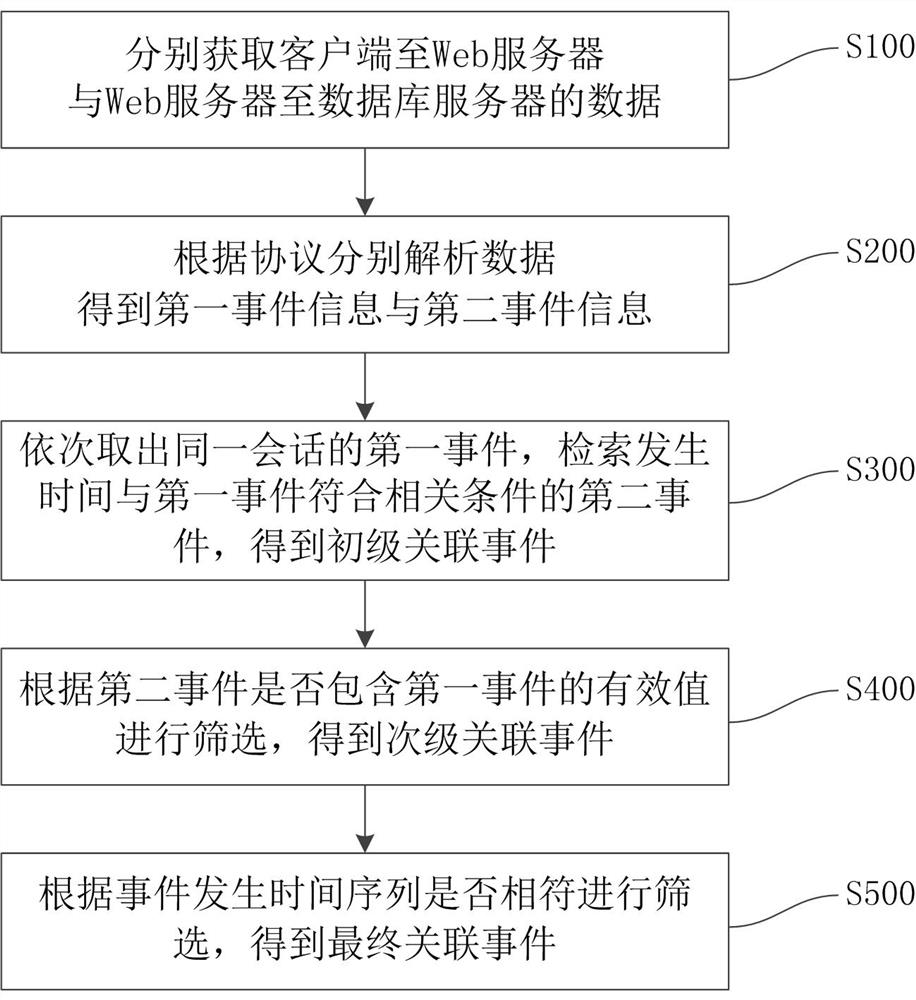
[0037] This embodiment uses the DCOM-based three-tier architecture as an example to describe a specific event correlation process.
[0038] Step 1: Client -> application server (DCOM) (ie the first event) data self-learning and content audit
[0039] The audit engine analyzes the network data packets from the client->application server, and parses the tubdata (valid data) according to the DCOM protocol format. The tub data data format is generally XAa1Aa2, XBb1Bb2Bb3, (X, A, B are characteristic keywords, a1, a2 , b1, b2, b3 are valid data). Through the regular extraction of tub data and continuous data analysis, learning and verification, the analysis rule base is continuously improved, so that the effective data of tub data can be directly analyzed from network data packets.
[0040] Record client -> application server event information, including occurrence time (in microseconds), session ID (the value obtained from source IP, destination IP, source port, destination port,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com