DDoS malicious code detection and traceability method based on breeding
A malicious code detection and malicious code technology, applied in the field of breeding-based DDoS malicious code detection and traceability, can solve the problems of difficult malicious code association, error, failure to actively defend, etc., to achieve the effect of expanding the scope of application and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be further described in detail and in-depth below in conjunction with the accompanying drawings.
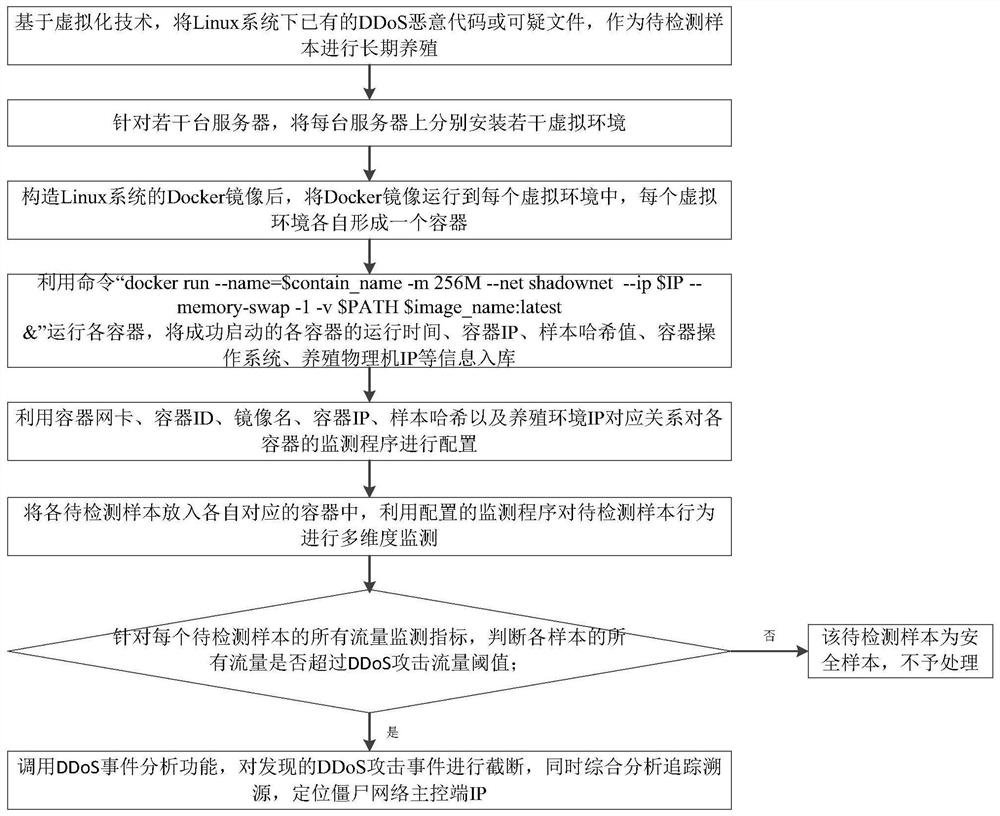
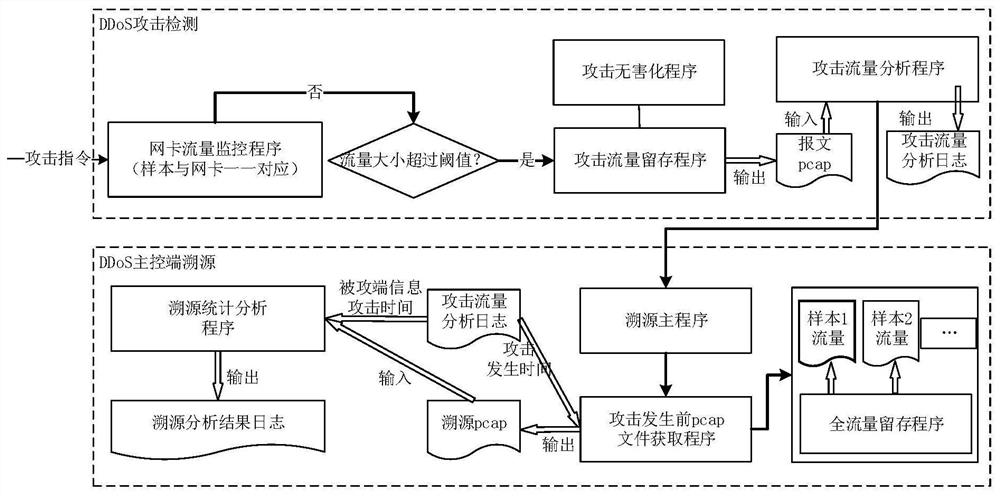
[0036] The present invention provides a breeding-based DDoS malicious code detection and traceability method, including long-term breeding of the samples to be detected under Linux; monitoring the flow changes in the breeding environment, detecting and identifying DDoS attack flow; and performing DDoS traceability on discovered attack events , to locate the main control terminal of the botnet.
[0037] like figure 1 As shown, the specific steps are as follows:
[0038] Step 1. Based on virtualization technology, use the existing DDoS malicious code or suspicious files under the Linux system as samples to be detected for long-term cultivation;
[0039] The malicious code architecture supported by breeding includes: x86_64, x86, MIPS, MIPS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com