Secret key management system, updating method and reading method based on KeyStore secret key tree
A key management system and key update technology, which is applied in the field of secure communication, can solve the problems of unable to reflect the key layered management system, unable to ensure key security, internal ghosts, etc., and achieve multi-user key system management, The effect of facilitating hierarchical key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
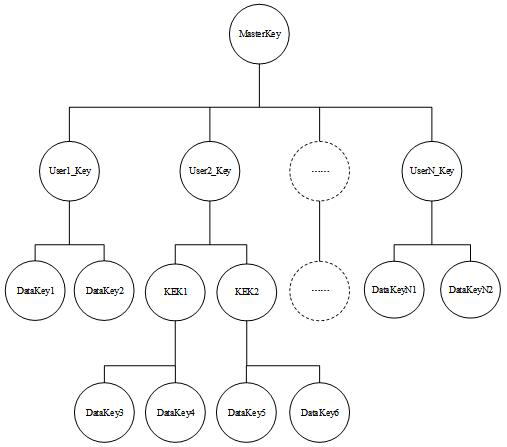
[0056] refer to figure 1 As shown, this embodiment provides a key management system based on a KeyStore key tree, including a key tree, and the key tree includes several layers of key layers in a hierarchical topology, specifically, as image 3 Shown:
[0057] The key tree includes the following layers of keys:
[0058] The master key, denoted as MasterKey, is located at the highest level of the entire key tree hierarchy;
[0059] The user key, denoted as UserKey, is located in the second layer of the entire key tree hierarchy and is encrypted and protected by the master key, which is used to encrypt the key of the branch node of its subordinate layer; the key of this layer can be distributed to cloud users by the cloud service system Or background management personnel and maintenance personnel with different authority levels. If this layer contains multiple user keys, they are recorded as User1_Key, User2_Key, User3_Key... respectively.
[0060] The key encryption key, de...
Embodiment 2
[0088] This embodiment provides a method for updating a key, which is applied to the key management system based on the KeyStore key tree described in Embodiment 1;
[0089] It is used to update the key of the lower branch node corresponding to the current node key when the key of the current node is updated, which specifically includes the following steps:
[0090] S100. First, the system randomly generates a new key;
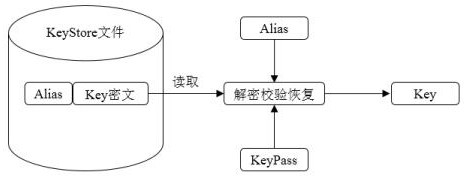
[0091] S200. Traverse the lower layer node key of the node key through the original key, and read out the plaintext of the key;
[0092] S300. Using the new key to calculate the KeyPass of the lower node key;
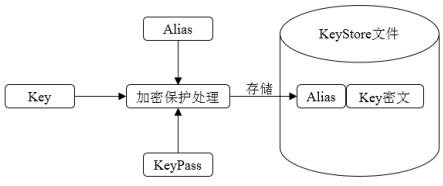
[0093] S400, according to the KeyPass calculated in step S300, and the Alias corresponding to the lower node key to re-encrypt and overwrite the storage key;
[0094] S500. Encrypt the new key using the associated name Alias of the current node key and KeyPass, and overwrite the original ciphertext of the current node key.
[0095] In order to un...
Embodiment 3
[0102] Since there are two situations when the key is updated, the first one is the situation in Embodiment 2 (the key system update brought about by the node key update); the second one is caused by the associated name Alias of the node key The key system update brought
[0103] Therefore, this embodiment provides a key update method for the second situation, which is applied to the key management system based on the KeyStore key tree described in Embodiment 1.
[0104] It is mainly used to update the associated name Alias of the lower branch node key corresponding to the node key when the associated name Alias of the current node key is updated, specifically including the following steps:
[0105] T100. Read all branch node keys with the current node key as the root node key;
[0106] T200. Correspondingly replace the associated name Alias of all branch node keys with the current node key as the root node key;
[0107] T300. Recalculate the KeyPass of all branch no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com