Identity authentication method, storage medium, processor and system
A technology of identity authentication and identity information, applied in the field of identity authentication, can solve the problems of increasing the target search range, increasing the cost of server hardware, and reducing the recognition accuracy, so as to achieve the effect of improving accurate search capabilities, fast server resources, and reducing the number of searches
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
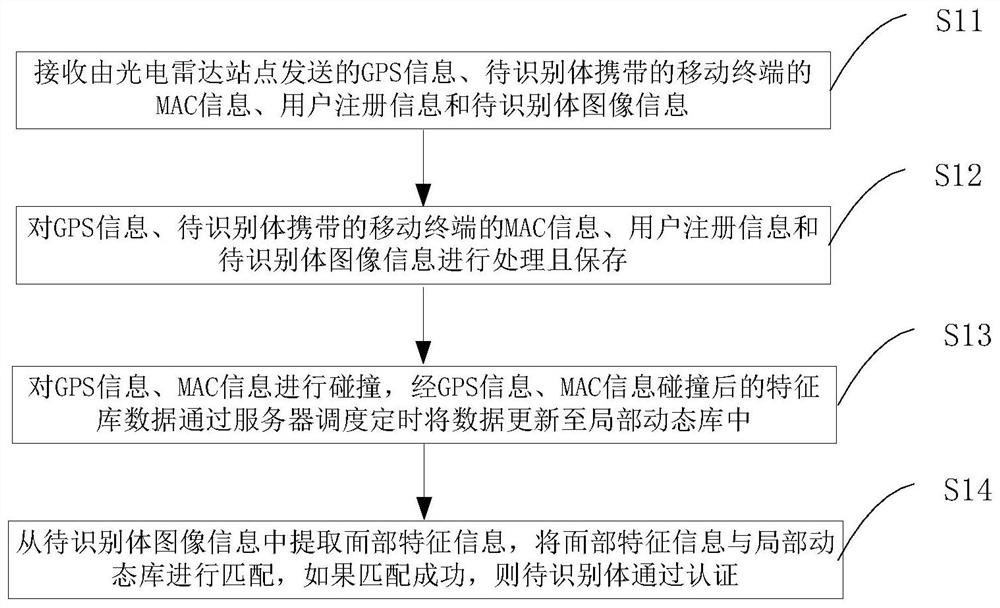
[0057] figure 1 It is a flowchart of an identity authentication method of the present invention. Such as figure 1 As shown, an identity authentication method includes steps:
[0058] S11. Receive GPS information sent by the photoelectric radar site, MAC information of the mobile terminal carried by the object to be identified, user registration information, and image information of the object to be identified;
[0059] S12. Process and save the GPS information, the MAC information of the mobile terminal carried by the object to be identified, the user registration information, and the image information of the object to be identified;
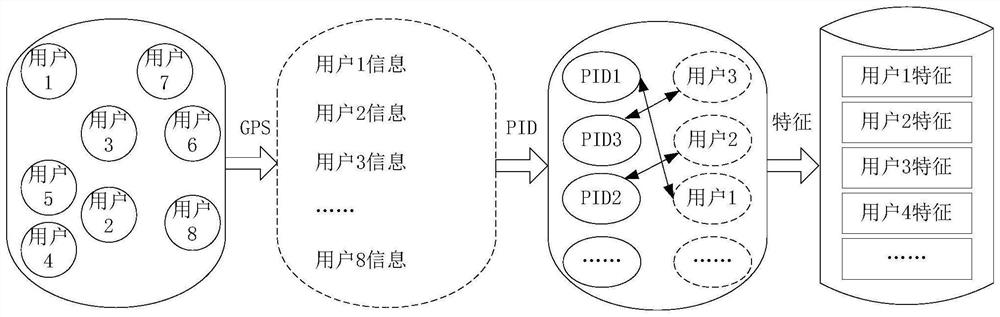
[0060] S13, collide with GPS and MAC, and update the data in the local dynamic database regularly through server scheduling for the feature database data after GPS and MAC collision;
[0061] S14. Extract biometric information from the image information of the object to be identified, and match the biometric information with the local dynamic...
Embodiment 2
[0081] An embodiment of the present invention also provides a storage medium, the storage medium includes a stored program, wherein the above-mentioned identity authentication method process is executed when the above-mentioned program is running.
[0082] Optionally, in this embodiment, the above-mentioned storage medium may be configured to store program codes for executing the following flow of the face attribute recognition method:
[0083] S11. Receive GPS information sent by the photoelectric radar site, MAC information of the mobile terminal carried by the object to be identified, user registration information, and image information of the object to be identified;
[0084] S12. Process and save the GPS information, the MAC information of the mobile terminal carried by the object to be identified, the user registration information, and the image information of the object to be identified;
[0085] S13, collide with GPS and MAC, and update the data in the local dynamic da...
Embodiment 3
[0090] An embodiment of the present invention also provides a processor, which is used to run a program, wherein the steps in the above identity authentication method are executed when the program is running.
[0091] Optionally, in this embodiment, the above program is used to perform the following steps:
[0092] S11. Receive GPS information sent by the photoelectric radar site, MAC information of the mobile terminal carried by the object to be identified, user registration information, and image information of the object to be identified;
[0093] S12. Process and save the GPS information, the MAC information of the mobile terminal carried by the object to be identified, the user registration information, and the image information of the object to be identified;
[0094] S13, collide with GPS and MAC, and update the data in the local dynamic database regularly through server scheduling for the feature database data after GPS and MAC collision;
[0095] S14. Extract biometr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com