Authentication system and method of identity authentication system based on block chain technology
A technology of identity authentication and authentication methods, applied in digital data authentication, instruments, data processing applications, etc., can solve problems such as single authentication methods, affect transaction efficiency, and inconvenient authentication, and achieve single identity authentication methods and ensure security , The verification method is convenient and fast
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Embodiments of the invention are described in detail below, examples of which are illustrated in the accompanying drawings. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
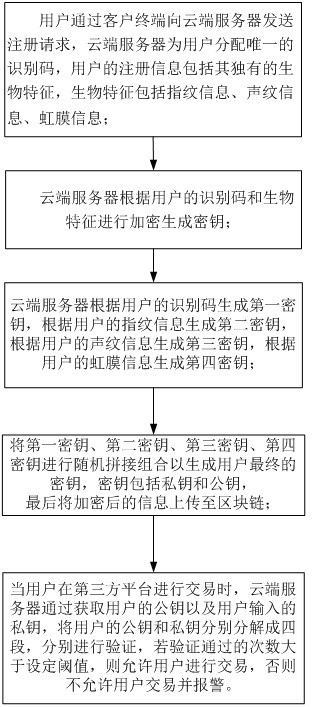
[0025] An identity authentication system based on blockchain technology provided in this embodiment includes a client terminal, a cloud server, and a third-party platform;
[0026] The user sends a registration request to the cloud server through the client terminal, and the cloud server assigns a unique identification code to the user. The user's registration information includes its unique biometric features, which include fingerprint information, voiceprint information, and iris information;
[0027] The cloud server encrypts and generates keys based on the user's identification code and biometric features, including:
[0028] The cloud server generates a first key b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com