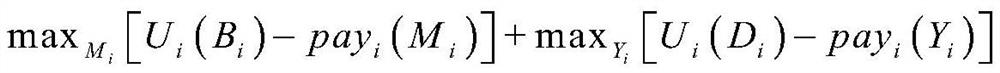Resource safety transaction method based on block chain
A resource security and transaction method technology, applied in the field of power resources and communication spectrum resource transactions, can solve the problems of centralized information leakage and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
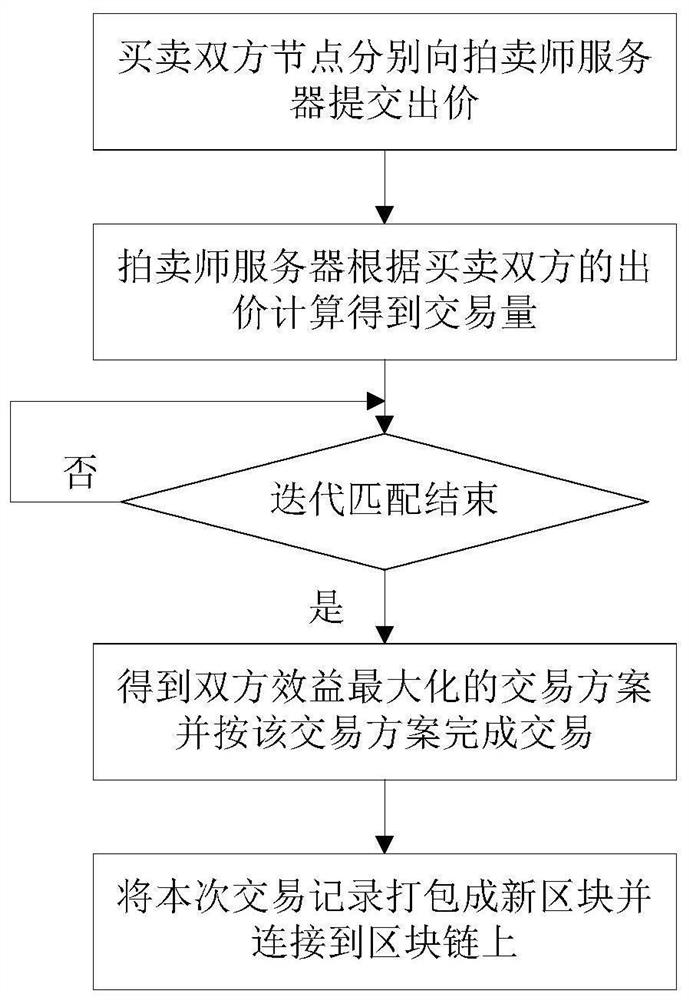
[0063] like figure 1 Shown, a resource block chain secure transaction method based on the steps comprising:
[0064] S1: the buyer submitted a bid to the auctioneer node server according to its demand, sellers submit bids to the auctioneer server nodes based on their availability;
[0065] S2: get trading volume is calculated according to the bid the auctioneer server buyers and sellers;
[0066] S3: auctioneer server based on iterative matching of buyers and sellers bid, to get the two sides to maximize the benefits of the trading scheme trading scheme and press to complete the transaction;
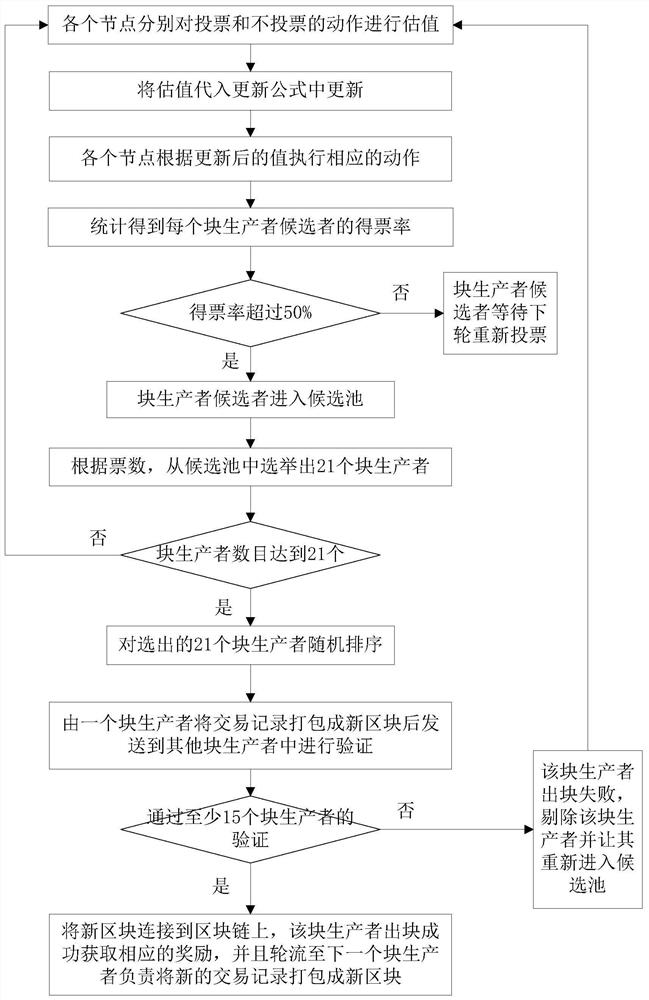
[0067] S4: The transaction recording and packed into a new block attached to the block chain.
[0068] In the implementation process, the traditional auction buyers and sellers need to provide their own specific needs, such direct trade fairs residential users of electricity leak information and personal privacy; iterative double auction mechanism, buyers and sellers do not give themselves a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com