Privacy-protected mobile communication authentication method
A mobile communication and privacy protection technology, which is applied in the field of privacy protection mobile communication authentication, can solve the problems of not being able to stop opponents and leak user privacy, and achieve the effect of protecting user privacy and protecting user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
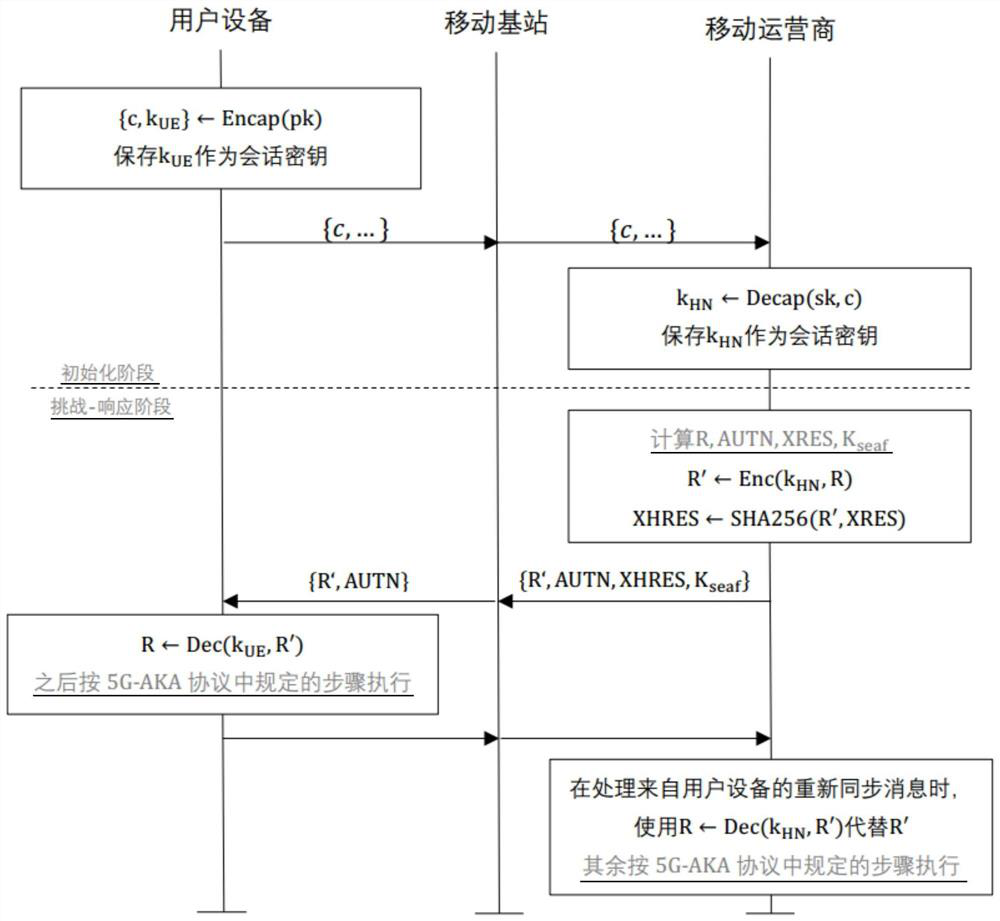
[0035] Embodiment 1. Apply the ECIES algorithm included in the 5G-AKA protocol to implement a privacy-protected mobile communication authentication method proposed by the present invention. The KEM scheme included in the ECIES algorithm is denoted as KEM ECIES =(Encap ECIES ,Decap ECIES ).
[0036] The procedure of this method is as follows figure 1 As shown, the specific description is as follows:
[0037] 1) During the initialization phase of the 5G-AKA protocol, the user equipment encrypts its user identifier (SUPI) and sends it to the mobile operator through the ECIES algorithm (the encrypted SUPI is denoted as SUCI).
[0038] 1-1) The user equipment executes EncapECIES Algorithm, get {c,k UE}. Afterwards, in addition to using k in accordance with the provisions of the 5G-AKA agreement UE Encrypt SUPI with the corresponding data encapsulation algorithm, and send SUCI to the mobile operator, and save k UE as a session key for the challenge-response phase.
[0039] ...
Embodiment 2
[0052] Embodiment 2. Using the KEM scheme resistant to quantum computer attacks to implement a privacy-protected mobile communication authentication method proposed by the present invention.
[0053] In this embodiment, the KEM scheme that is resistant to quantum computer attacks is used to protect user privacy in a 5G mobile communication system. Remember KEM PQ =(Encap PQ ,Decap PQ ) is a KEM scheme that can resist quantum computer attacks, and the specific description of this embodiment is as follows:
[0054] 1) During the initialization phase of the 5G-AKA protocol, the user equipment and the mobile operator pass the KEM PQ Negotiate a session key:
[0055] 1-1) The user equipment calls Encap PQ The algorithm obtains {c,k UE}, store k UE , and send c to the mobile operator via the 5G-AKA information flow.
[0056] 1-2) The mobile operator calls Decap PQ Algorithm to get k HN , and store k HN .
[0057] 2) In the challenge-response phase of the 5G-AKA protocol,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com