Circular range query method and system in cloud environment based on position privacy protection
A privacy protection and query method technology, which is applied in the circular range query field in the cloud environment, can solve problems such as circular range query difficulties, ciphertexts cannot directly reveal query results, and limit query use, so as to reduce query time and solve security problems. Hidden dangers, the effect of improving query efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] Embodiment 1 of the present disclosure provides a method for querying a circular range in a cloud environment based on location privacy protection, which is applied to a location query terminal and includes the following steps:
[0058] The location query terminal requests the location server for the key pair of the location query terminal, the atomic area code of the area where the query location is located, and the key pair of the hash function, and obtains the atomic area code of the query area encrypted by the public key of the location query terminal;
[0059] The location query terminal uses the private key to decrypt the atomic area code of the query area, and determines the atomic area set within the query range and the atomic area set intersecting the query range boundary according to the circular query range, and the circular query range represented by the query position and radius Convert to query vector form;
[0060] The location query terminal uses the has...
Embodiment 2
[0109] Embodiment 2 of the present disclosure provides a circular range query device in a cloud environment based on location privacy protection, including a processor, including the following steps:
[0110] The processor requests the key pair of the processor, the atomic area code of the area where the query location is located, and the key pair of the hash function from the location server, and obtains the atomic area code of the query area encrypted by the public key of the processor;
[0111] The processor uses the private key to decrypt and obtain the atomic area code of the query area, determines the set of atomic areas within the query range and the set of atomic areas intersecting the boundary of the query range according to the circular query range, and converts the circular query range represented by the query position and radius to In query vector form;
[0112] The processor performs hash processing on the atomic region set within the range and the atomic region c...
Embodiment 3
[0116] Embodiment 3 of the present disclosure provides a circular range query method in a cloud environment based on location privacy protection, which is applied to a location server and includes the following steps:
[0117] The location server generates the key required for the encryption vector and the key of the hash function, and at the same time generates a unique key pair for each location query terminal;
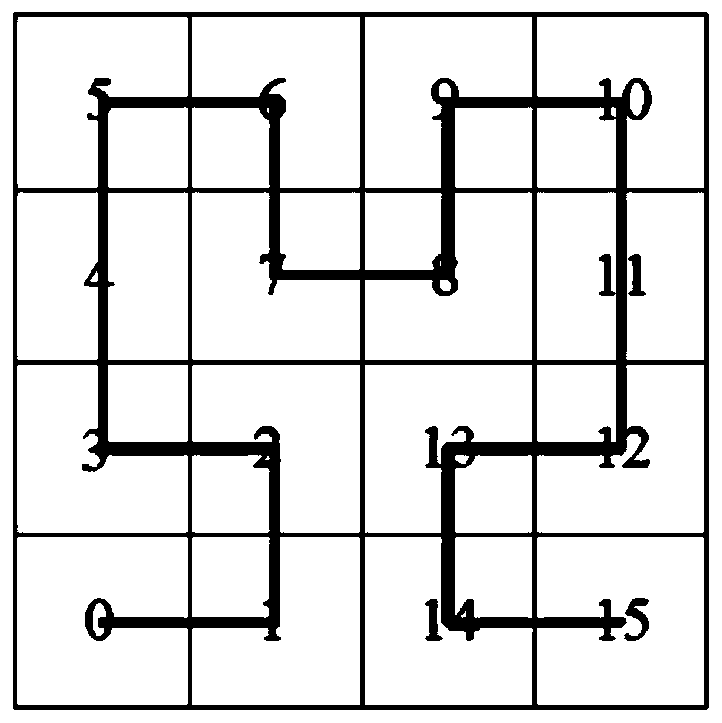
[0118] The location server uses the Hilbert curve to divide the area to be queried into a collection of multiple atomic areas, stores and manages the spatial data points in units of atomic areas, and constructs a position vector and index for each spatial data point;
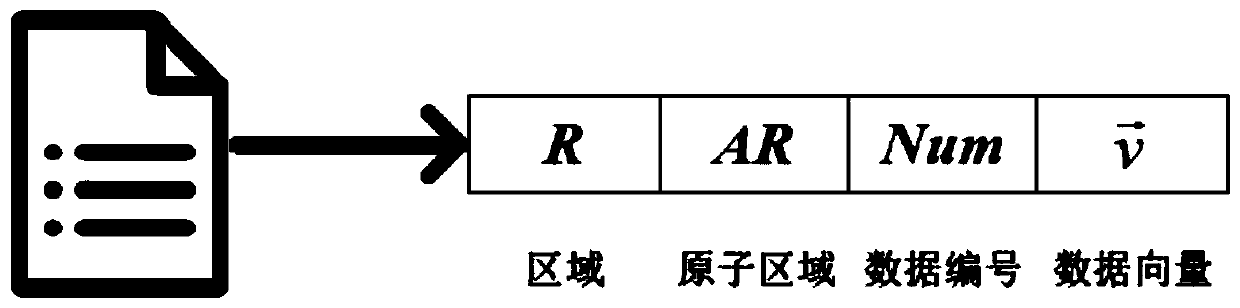
[0119] The location server encrypts the index and sends it to the cloud server, so that the cloud server judges the relationship between the query range and the spatial data according to the location vector in the encrypted index and the encrypted query vector in the token to obtain the final query res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com