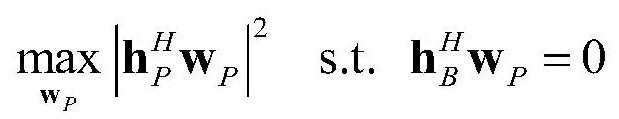A low-complexity and low-latency secure transmission method
A technology of secure transmission and low complexity, applied in the field of secure transmission with low complexity and low delay, and can solve problems such as path loss without considering spatial location distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
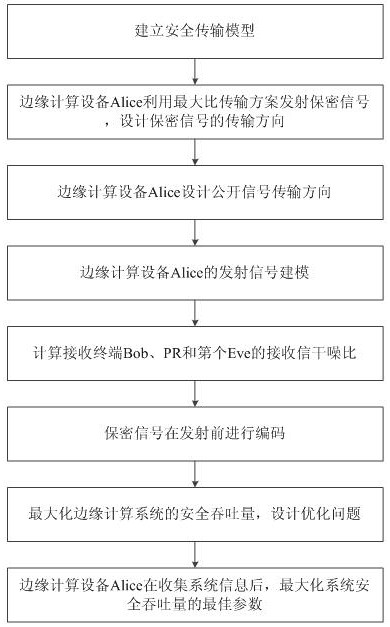
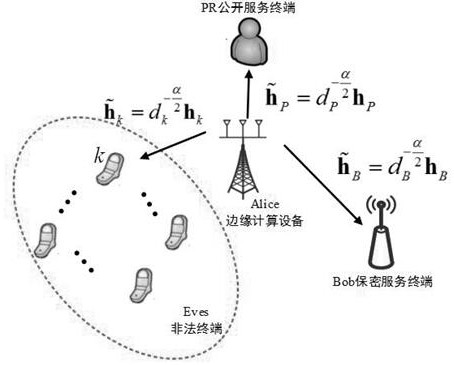
[0055] The present invention relies on the statistical channel information of the main channel and the eavesdropping channel, utilizes the static parameter transmission scheme, and the edge computing device performs offline design and optimization of the transmission parameters. The scheme is simple in design and low in complexity, and can reduce communication delay. For example, the security transmission requirements under industrial communication control, especially the terminal real-time control security transmission scenario in the edge computing scenario, this method is easy to provide specific physical characteristic parameters because the edge side is close to the terminal; it provides equipment support for the realization of this meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com