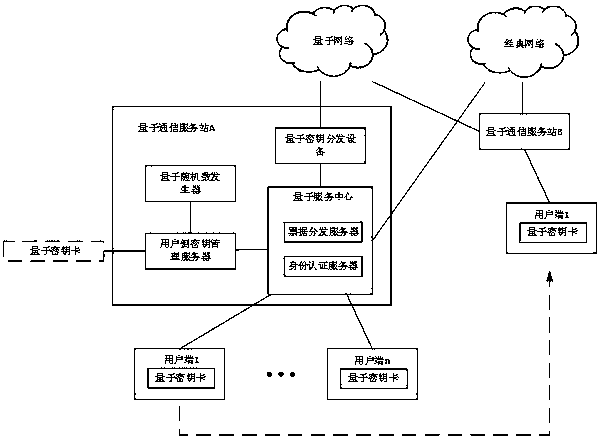
Quantum communication service station key agreement system and method based on secret sharing and timestamps
A technology of quantum communication and secret sharing, which is applied in the field of key agreement system of quantum communication service station, and can solve problems such as user information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
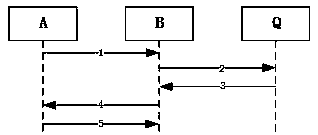
[0090] Embodiment 1, key agreement between two clients in the LAN:
[0091] In this embodiment, client A and client B belong to the same quantum communication service station Q. Flowchart such as figure 2 shown.
[0092] Step 1: A→B.
[0093] Client A obtains the current timestamp timestampA, let x 0A =timestampA
[0094] Client A reads x from the matching key fob 1A , calculate x′ 1A =HASH(x 1A ||x 0A ), x′ 2A =HASH(x 0A ||x 1A ).
[0095] will x 1A , x' 1A and x' 2A For comparison, if any two are equal, the current timestampA does not meet the conditions for replacing the PID. At this time, it is necessary to obtain timestampA again and replace it to check whether the conditions for replacing the PID are met.
[0096] Order N A = timestampA. Use client A's private key pair N A , x' 1A and x' 2A Sign to get SIGN(N A ||x′ 1A ||x′ 2A ,SK A). SIGN(m, k) means an ID-based cryptographic signature with m as the message and k as the key. The signature proce...
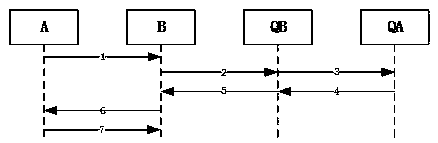
Embodiment 2
[0139] Embodiment 2, the key agreement of two clients in the wide area network:
[0140] Such as image 3 As shown, in this embodiment, client A and client B do not belong to the same quantum communication service station. Among them, client A belongs to quantum communication service station Q A , similarly, client B belongs to quantum communication service station Q B .
[0141] Step 1: A→B.
[0142] Client A obtains the current timestamp timestampA, let x 0A =timestampA
[0143] Client A reads x from the matching key fob 1A , calculate x′ 1A =HASH(x 1A ||x 0A ), x′ 2A =HASH(x 0A ||x 1A ).
[0144] will x 1A , x' 1A and x' 2A For comparison, if any two are equal, the current timestampA does not meet the conditions for replacing the PID. At this time, it is necessary to obtain timestampA again and replace it to check whether the conditions for replacing the PID are met.
[0145] Order N A = timestampA. Use client A's private key pair N A , x' 1A and x' 2A S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com