Binary software vulnerability detection system and method based on dynamic taint tracking
A dynamic binary and dynamic taint technology, applied in software testing/debugging, error detection/correction, hardware monitoring, etc., can solve the problems of incomplete taint propagation logic semantic information, high performance overhead of dynamic taint tracking, and poor applicability, etc. The effect of extending applicability, reducing performance overhead, and increasing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
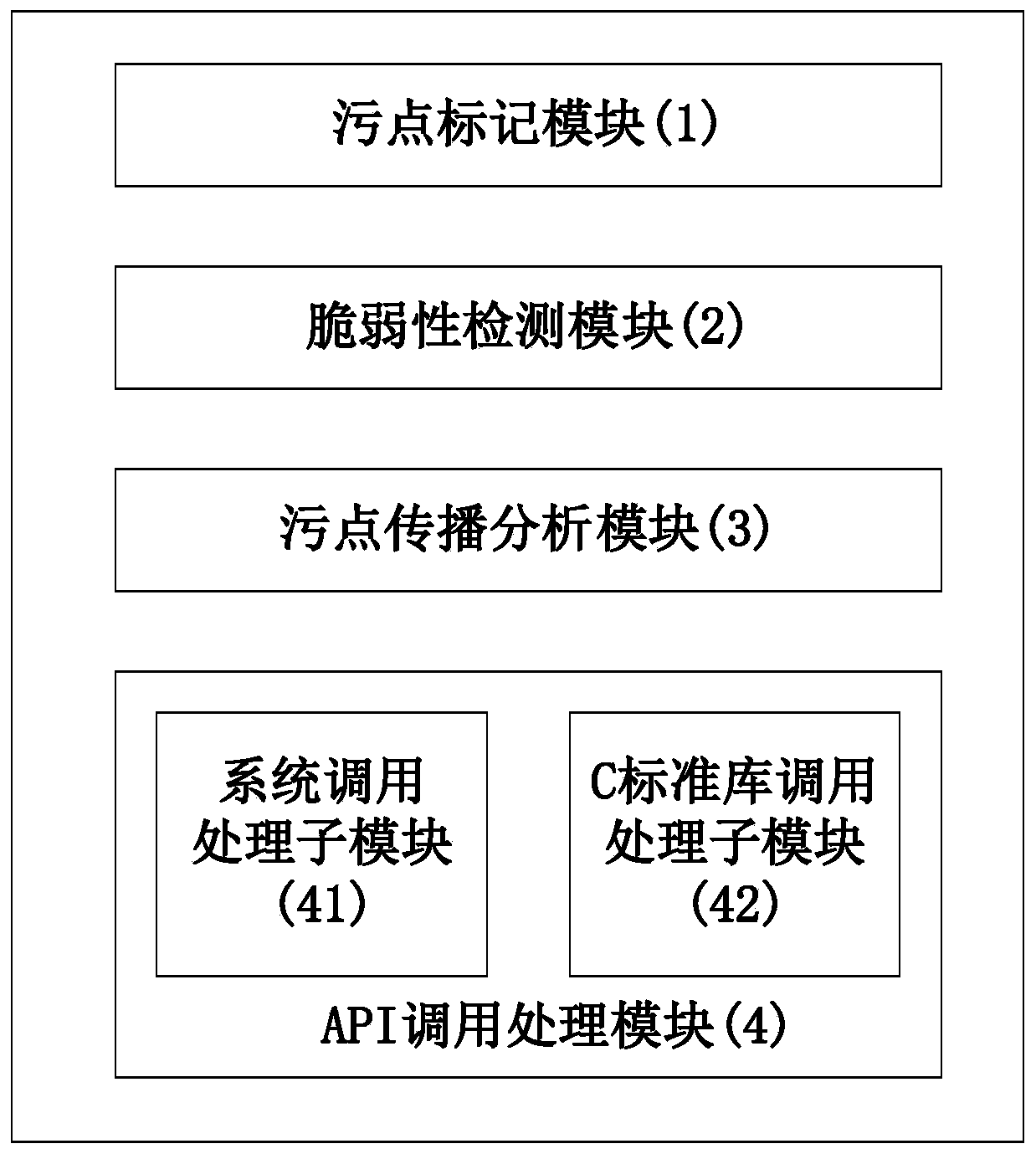
[0040] refer to figure 1 , the detection system of the present invention includes a taint marking module 1, a vulnerability detection module 2, a taint propagation analysis module 3 and an API call processing module 4, wherein:
[0041] The stain mark module 1 is used to store the stain mark of the data in the monitored software process address space and the thread general register, and provides the stain mark operation function for the stain propagation analysis module 3 and the API call processing module 4, and the stain mark operation function Including: setting taint marks, clearing taint marks, and getting taint marks.
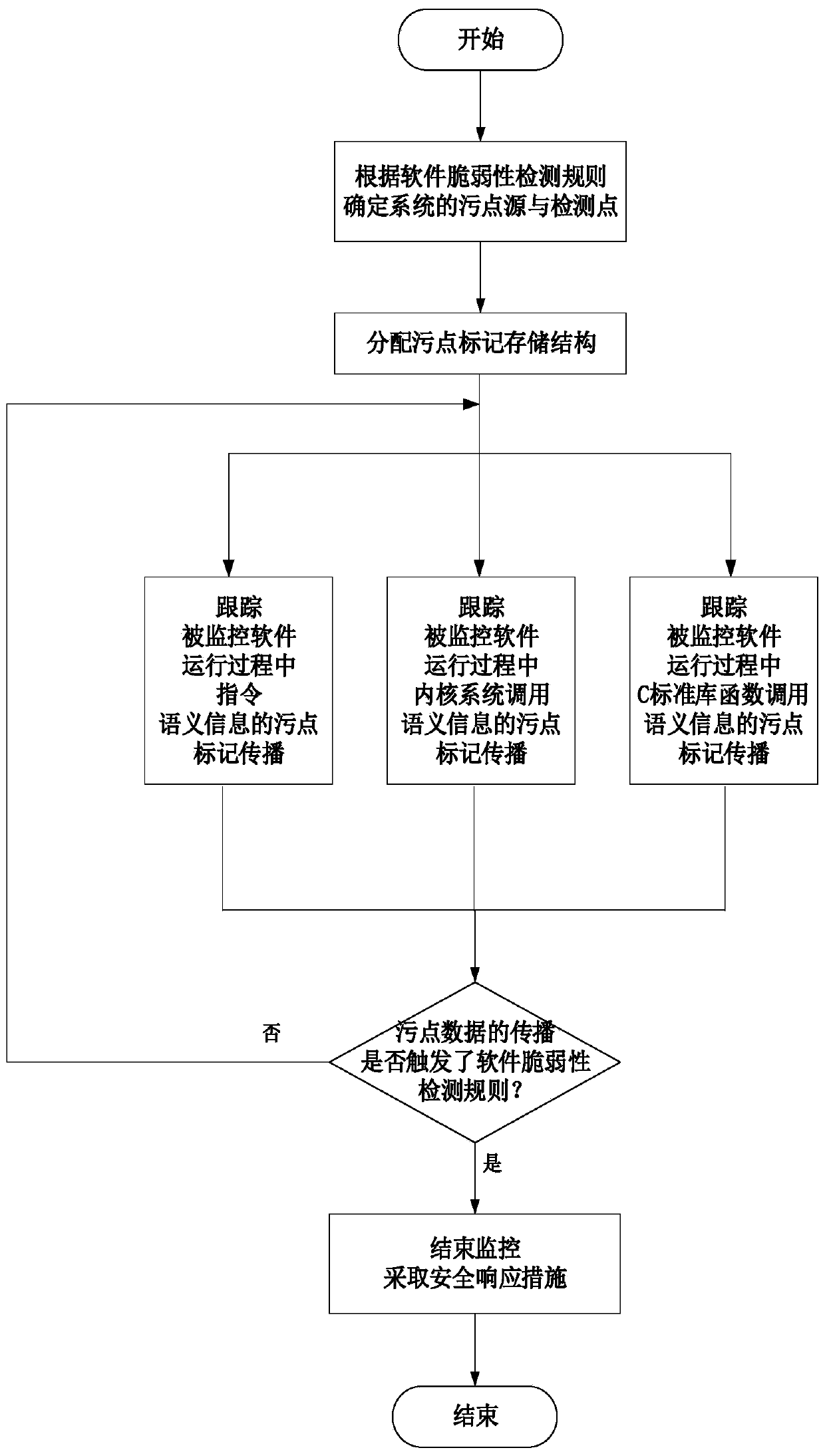
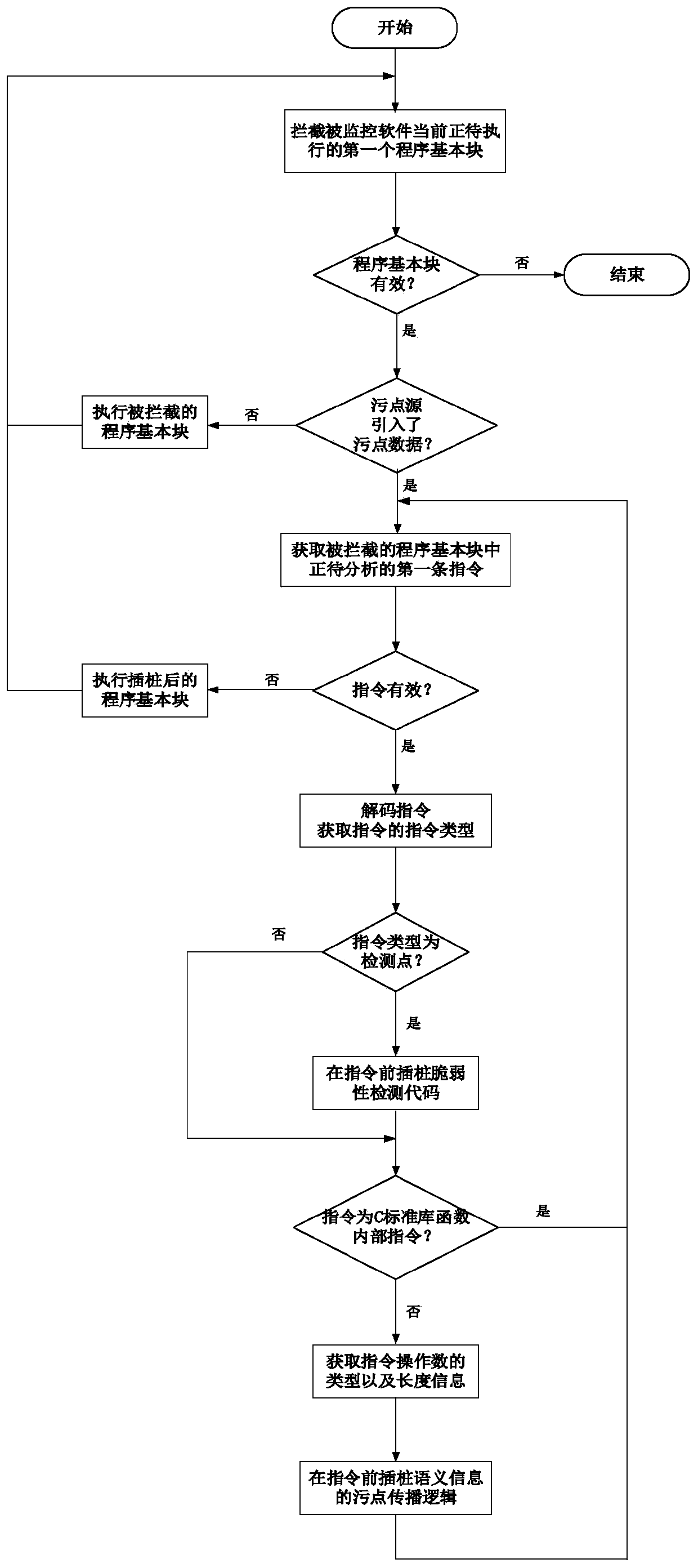
[0042] The vulnerability detection module 2 is used to detect whether the pre-established software vulnerability detection rules are triggered during the running of the monitored software, and take corresponding security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com