Token-based industrial network data tamper-proofing method and system
An industrial network, tamper-proof technology, applied in digital transmission systems, transmission systems, user identity/authority verification, etc., can solve problems such as insecure data transmission, achieve data content verification, accelerate research and development cycles, prevent theft and Tampering effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
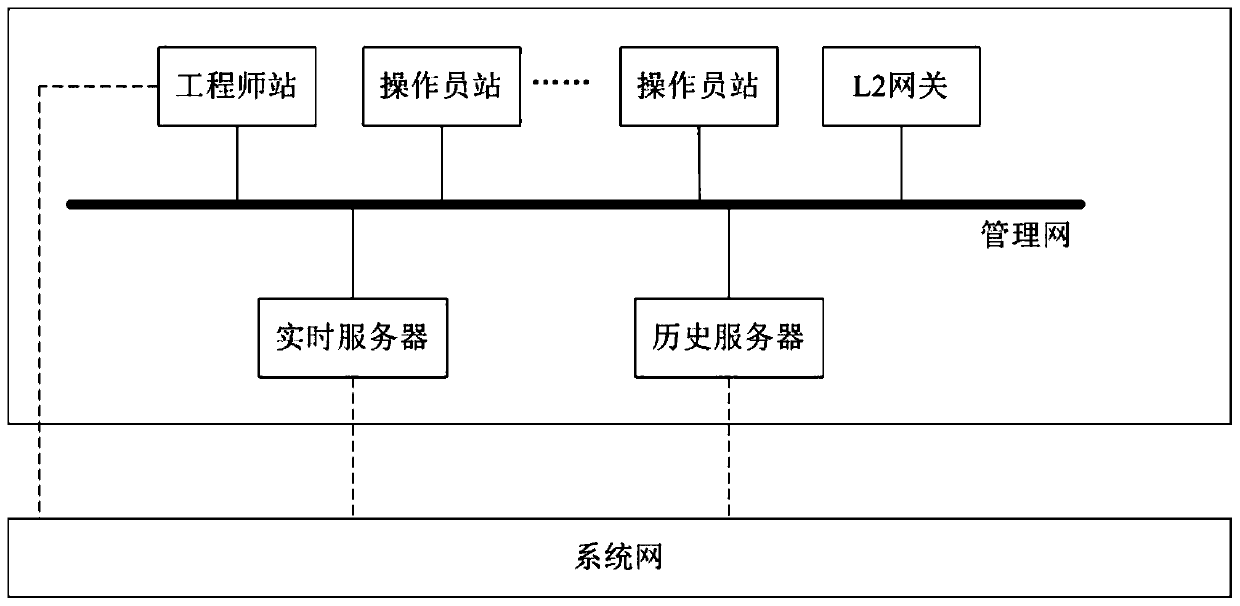
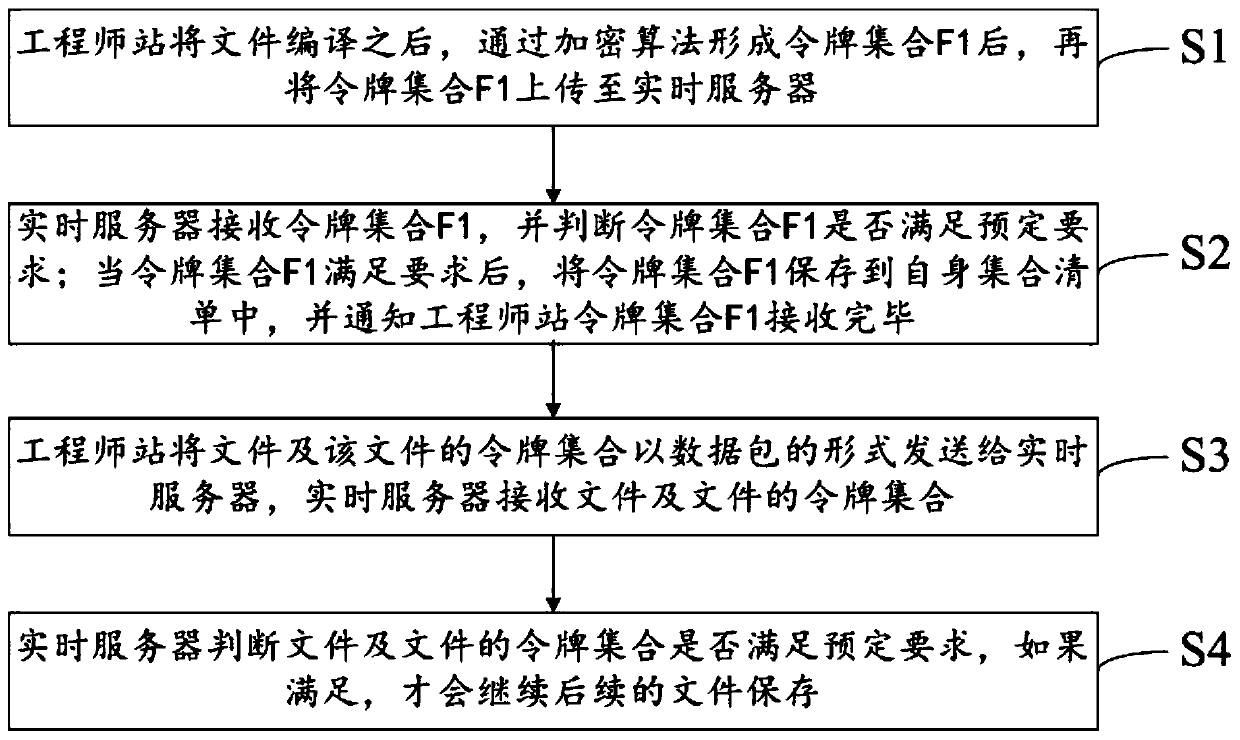
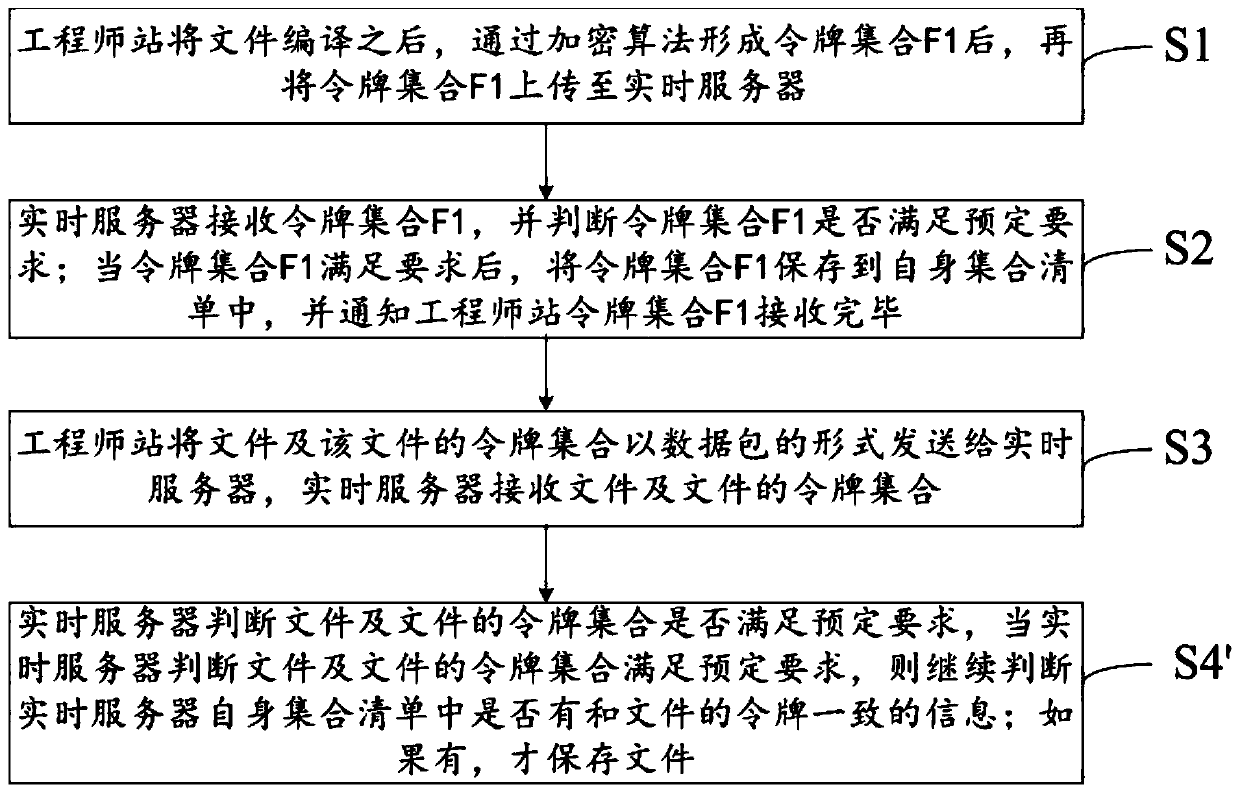
[0049]This embodiment provides a token-based anti-tampering method for industrial management network communication data. The method includes: before the engineer station sends communication data to the management network node, extracts the key information of the sent data and encodes it to generate text; The hash algorithm encrypts the text to generate a signature; the text and the signature form a token and send it together with the communication data; after the server receives it, it uses the built-in hash algorithm and the text in the token to generate a verification text; verifies the verification text and the token Whether the signature in the token matches, after matching, extract the key data of the received information and verify it with the Chinese text of the token, and prove that the communication data has not been tampered with after passing the verification.
[0050] Wherein, the token refers to a data packet describing the information to be sent, and the data pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com