Implementing system and implementing method for securely sending delay media
A technology for sending delays and media, which is applied in transmission systems, digital transmission systems, and key distribution, and can solve problems such as no implementation scheme, no implementation, and no solution given
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
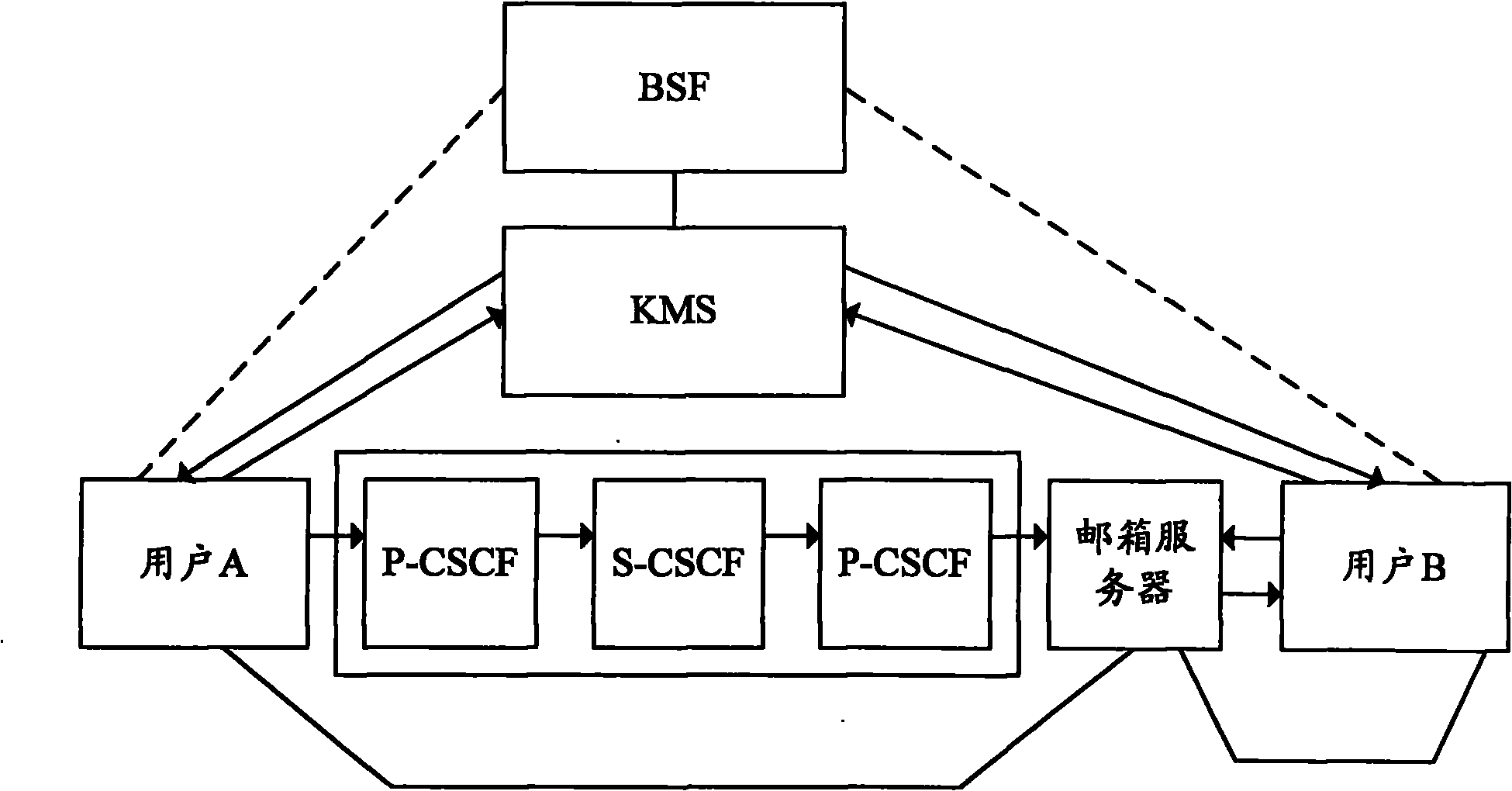
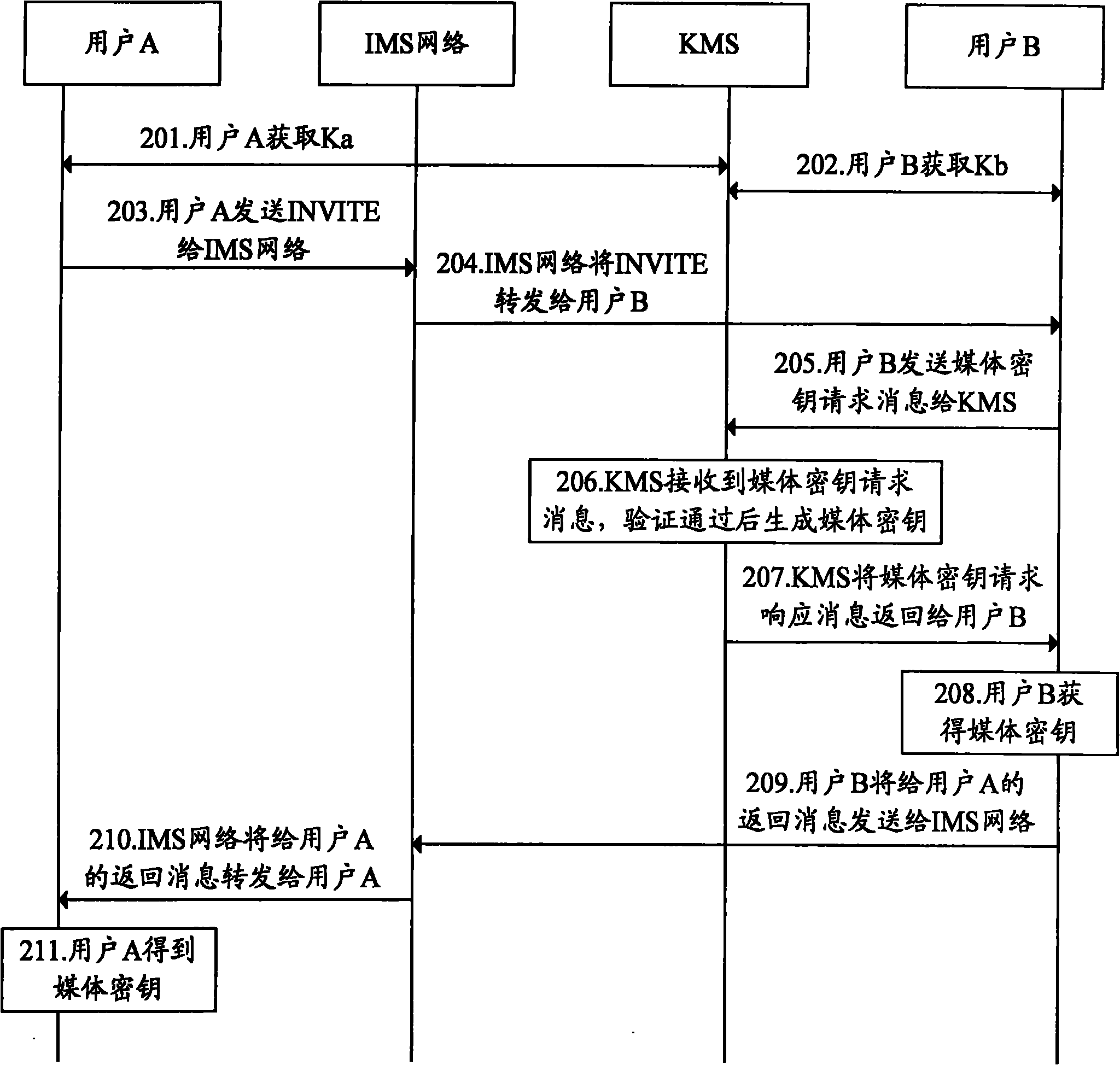
[0092] The basic idea of the present invention is: the calling user terminal initiates a request to the mailbox server of the called user, and obtains K through the mailbox server of the called user; the mailbox server of the called user receives the request, and obtains only the K that the user terminal can decrypt.
[0093] The implementation of the technical solution will be further described in detail below in conjunction with the accompanying drawings.
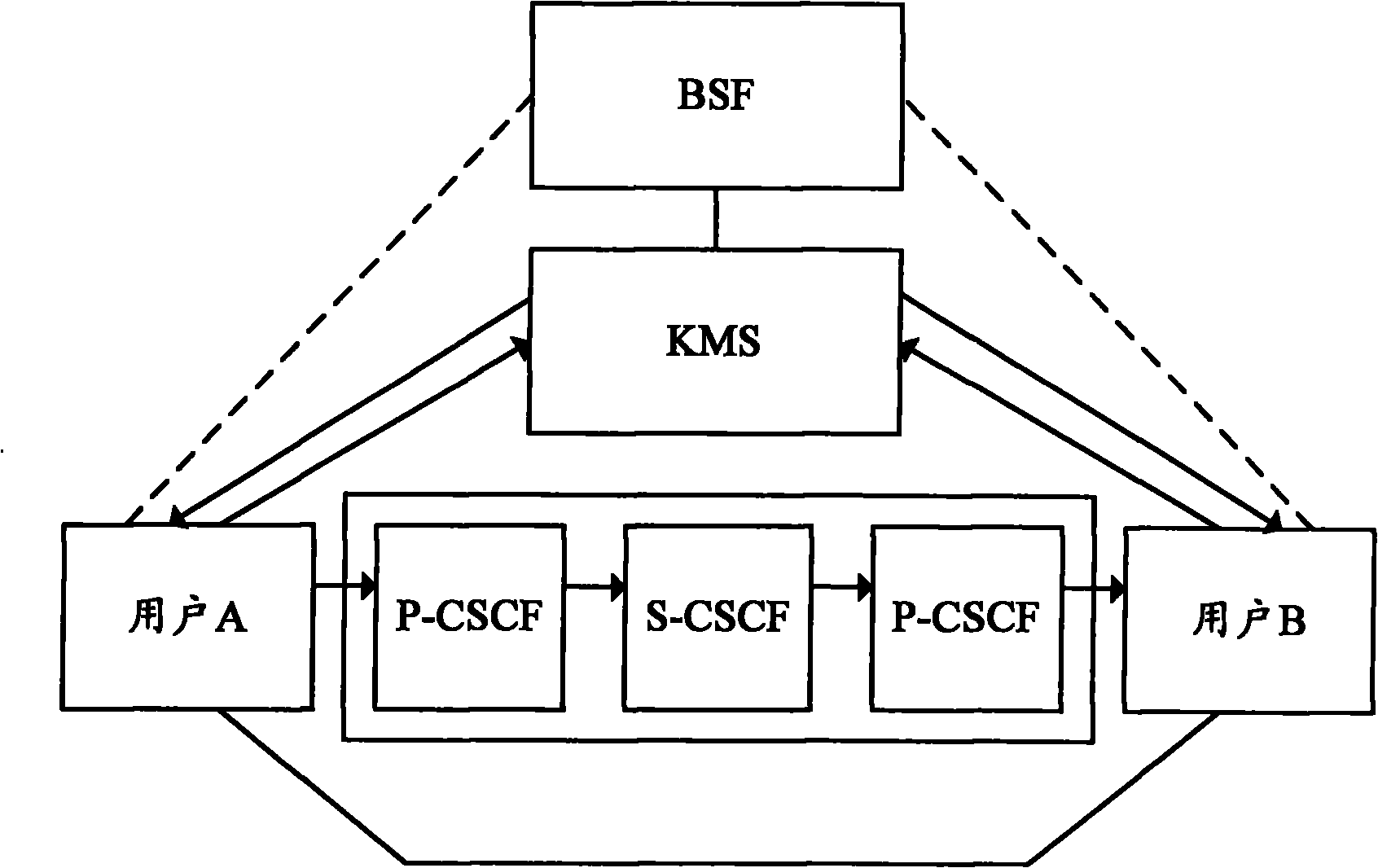
[0094] A realization system for safely sending delayed media, the system includes: an existing KMS, a calling user terminal, and a mailbox server of a called user. Wherein, the calling user terminal is used to initiate a request to the mailbox server of the called user, obtain K through the mailbox server of the called user, and realize sending the delayed media data securely. The mailbox server of the called user is used to receive the request, and obtain K through the KMS that only the calling user terminal can decry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com