Tamper-proof data storage method, device and system based on blockchain
A data storage device and data storage technology, applied in data processing applications, digital data protection, electronic digital data processing, etc., can solve problems such as forged log records, insufficient protection, and tampering with a single log file
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
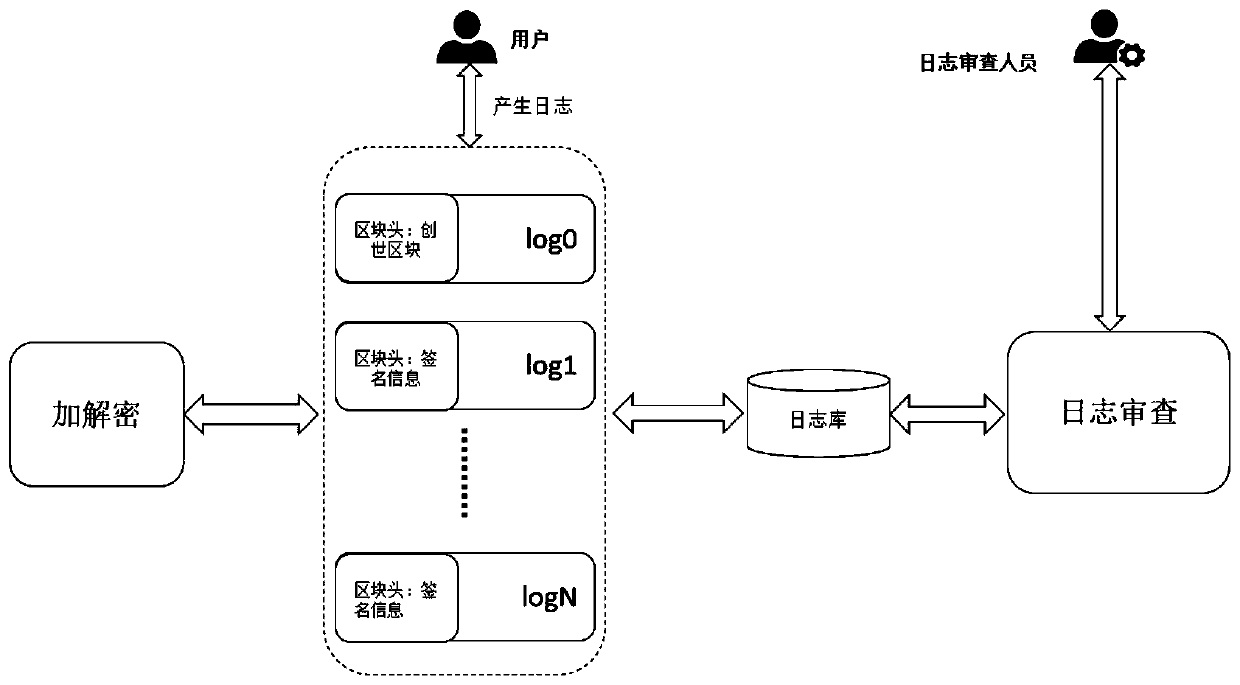
[0098] In the embodiment of the present invention, the original data is set as log information, and the collection of the log information uses the original interface of each system, and the review of the log involves users and log examiners. In other embodiments of the present invention, the The above data can also be set to other types of data as required.
[0099] In the embodiment of the present invention, it is first necessary to collect and process the logs generated by user behavior, store them in the log library in chronological order, and then present the log data to the log examiners in the form of a list. In addition, it is also necessary to ensure the storage security of the log, so the log must be tamper-proof. The specific method in the embodiment of the present invention is: when storing the log to the log library, the log needs to be stored in a block chain, and the log at every other section is used as a log block (ie block), and the log blocks are linked befor...
Embodiment 2
[0128] The difference between the embodiment of the present invention and embodiment 1 is:
[0129] The method also includes: chain verification, which is used to implement log review, specifically including the following steps:
[0130] Based on the input start date and end date, filter out the corresponding block set;
[0131] For any block in the block set, calculate the hash value hash3 of the block; decrypt the hash value hash4 of the saved block from the signature information of the next block of the block; compare hash3 with hash4, if the two are the same, it indicates that the block has not been tampered with.
[0132] specifically:
[0133] A. Based on the input start date S and end date E, filter out the corresponding data blocks SA, ..., EA; in the actual application process, the start date S and end date E may be input by auditors, When the input start date S and end date E are received, the corresponding blocks are automatically screened out. This implementatio...
Embodiment 3
[0144] The difference between the embodiment of the present invention and embodiment 1 or 2 is:
[0145] The method also includes Merkle root verification for implementing log inspection, specifically:
[0146] Based on the input start date and end date, filter out the corresponding block set;
[0147] List the block corresponding to the merkle root of the leaf node with the hash value of a certain block in the block set;
[0148] For any block randomly selected from the block, compare the merkle1 saved in the block with the calculated merkle2 of the block. If the two are inconsistent, the block corresponding to the root leaf node of the merkle One or more of the blocks have been tampered with.
[0149] More specifically: based on the input start date S and end date E, filter out the corresponding data block SA, ..., EA; in the actual application process, the start date S and end date E can be input by auditors Yes, when the input start date S and end date E are received, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com