Android malicious software detection method and device based on capsule network
A malware and detection method technology, applied in the field of network security, can solve problems such as inability to apply smart mobile device terminals, complex detection model design, software signature library cannot detect unknown malware, etc., achieve good detection results and facilitate classification detection Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
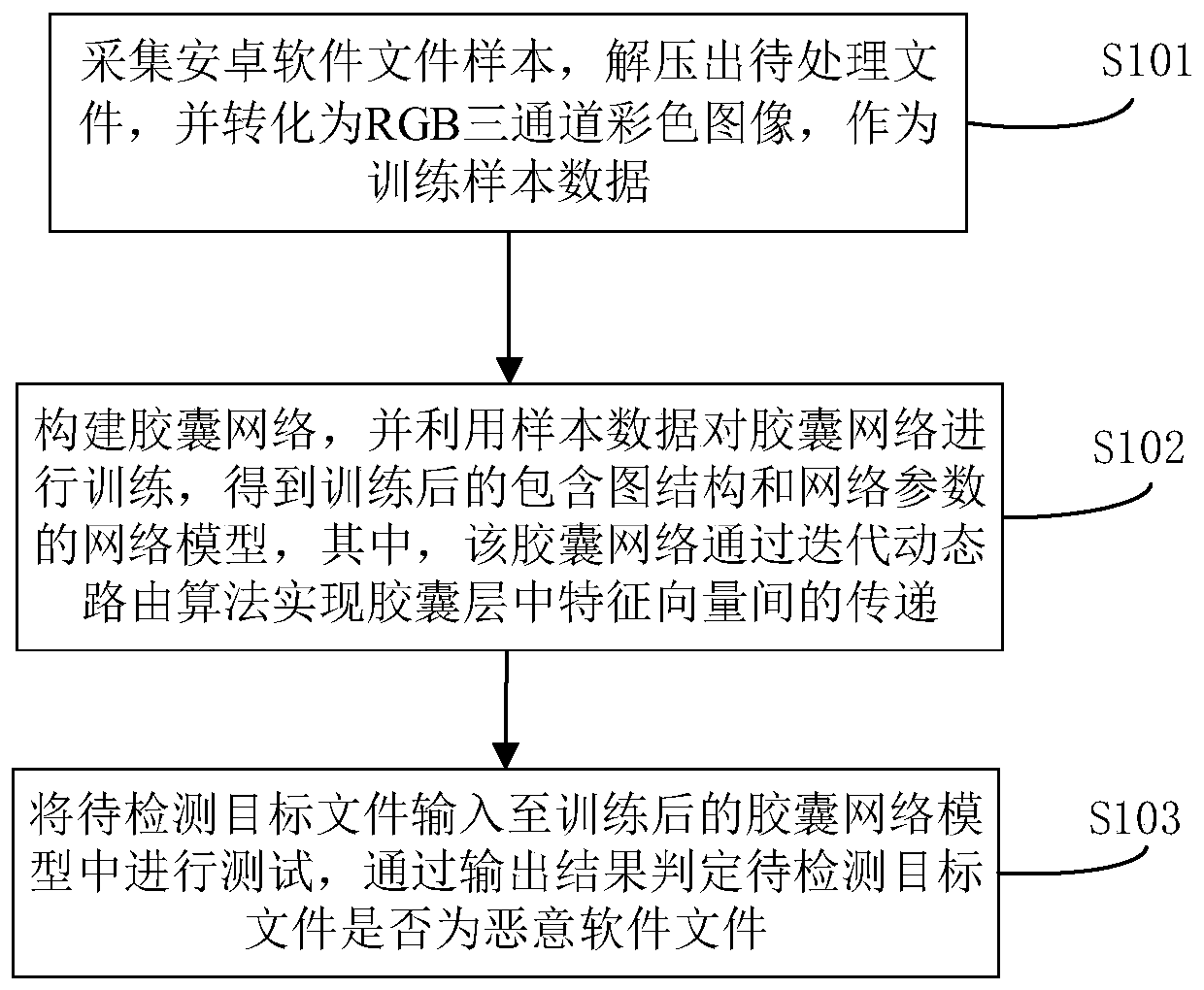
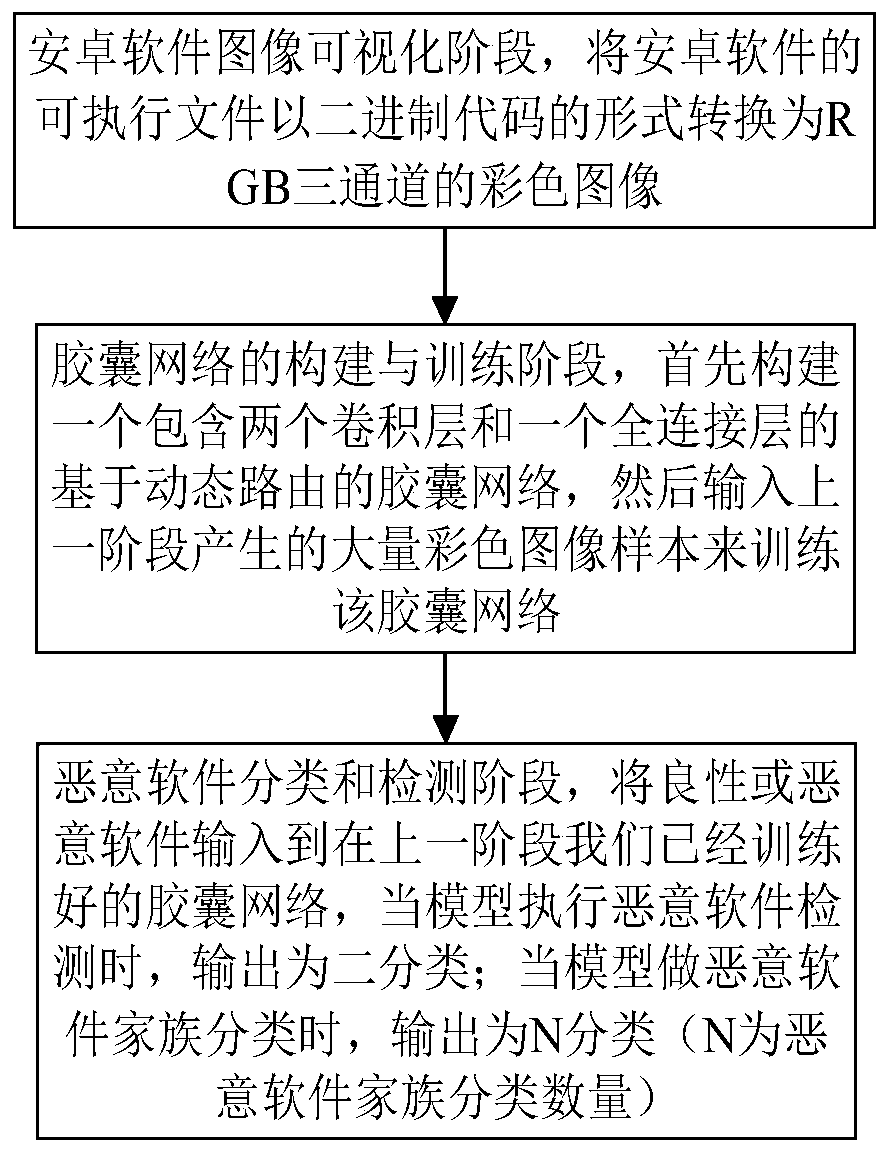
[0028] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
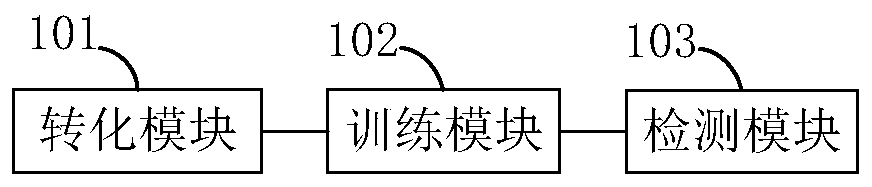
[0029] At present, there are many problems in the field of malware detection. The detection rate of traditional static detection algorithms is significantly reduced in the face of code obfuscation, packing, signature and other masquerade technologies; detection methods based on dynamic behavior monitoring occupy more system resources and cannot be applied to Android smart mobile Terminal; the feature extraction and screening of malware in the early stage of the machine learning algorithm is too complicated, and the cross-platform detection model has poor versatility. In view of this, in the embodiment of the present invention, see figure 1 As shown, a capsule network-based Android malware detection method is provided,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com