Fingerprint lock control system and method based on blockchain technology
A control system and fingerprint lock technology, applied in the field of fingerprint lock control systems based on blockchain technology, can solve problems such as hidden safety hazards of houses, lack of protection effect, etc., and achieve the effect of reducing security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
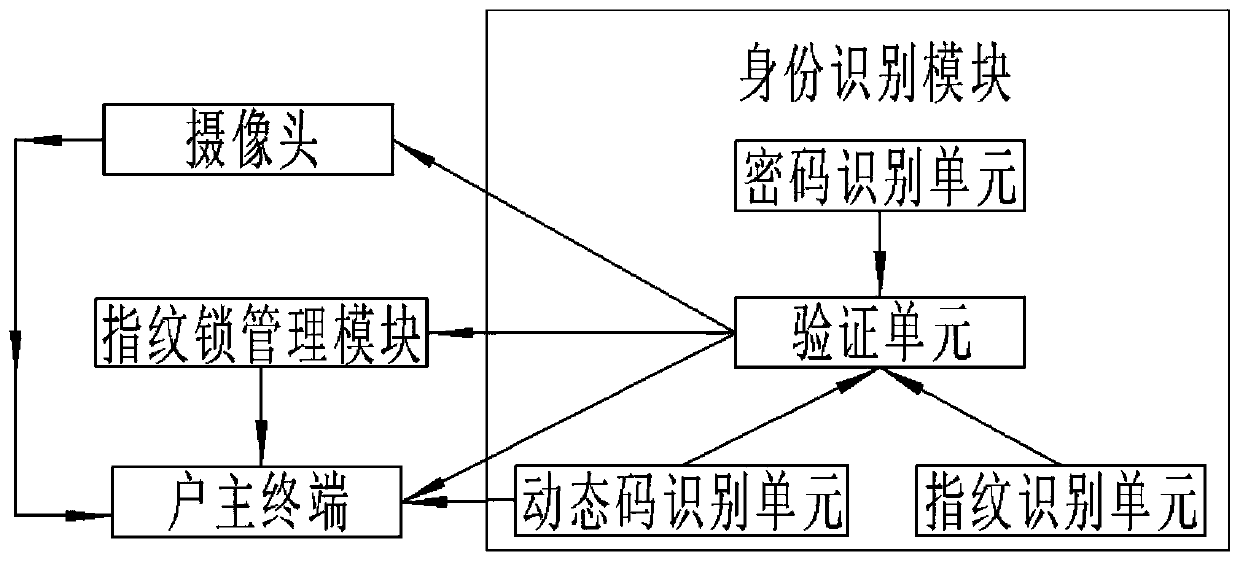
[0127] Embodiment 1: Limiting conditions: the user enters valid password A, fingerprint information B and random dynamic code C; valid password A pre-stored in the verification unit 1 , the fingerprint information database of visitors allowed by the householder to enter the house, and the random dynamic code C obtained by the terminal of the householder 1 ;
[0128] ①If A=A 1 , when the fingerprint information B is compared with the fingerprint information database of visitors allowed to enter the house by the head of household, the corresponding fingerprint information B is found in the information database 1 , B=B 1 ; Then the identity verification is successful, the verification unit prompts "YES", and the fingerprint lock is opened.
[0129] ②If A≠A 1 , when the fingerprint information B is compared with the fingerprint information database of visitors allowed to enter the house by the head of household, the corresponding fingerprint information B is not found in the i...
Embodiment 2
[0132] Embodiment 2: limited condition: continue to operate under the situation of 2., 3., 4. in embodiment 1;
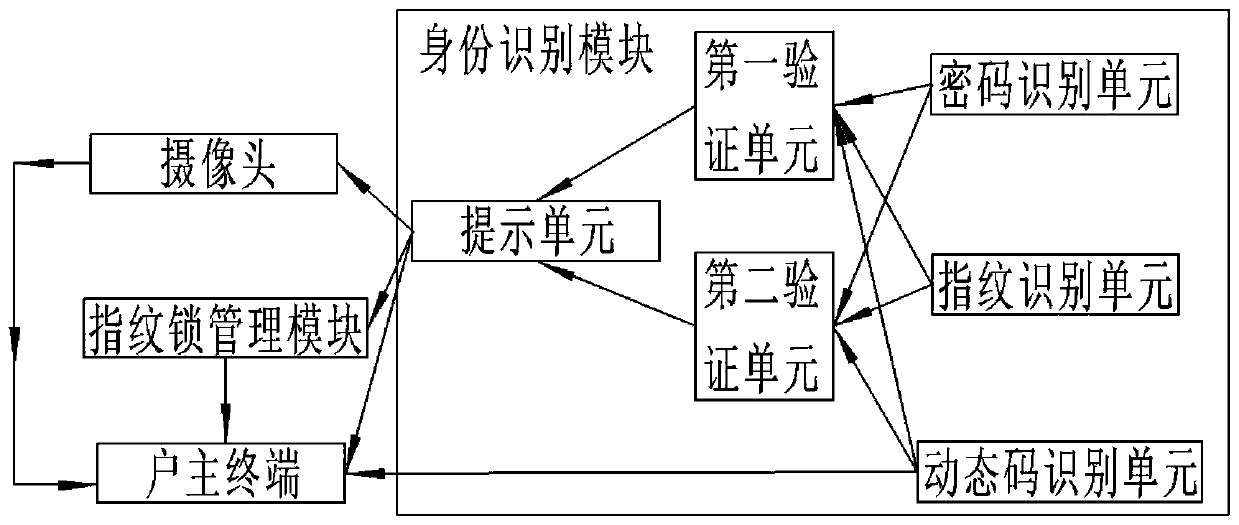
[0133]1. After the user authentication fails, re-authenticate, the authentication succeeds in the second authentication, and the fingerprint lock is opened;
[0134] 2. After the user verification fails, re-authentication, if the user has verified more than 5 times within 5 minutes, if all verifications fail, the head of the household will be alerted.
Embodiment 3
[0135] Embodiment 3: Limiting conditions: continue to operate on the basis of situation 2 of embodiment 2;
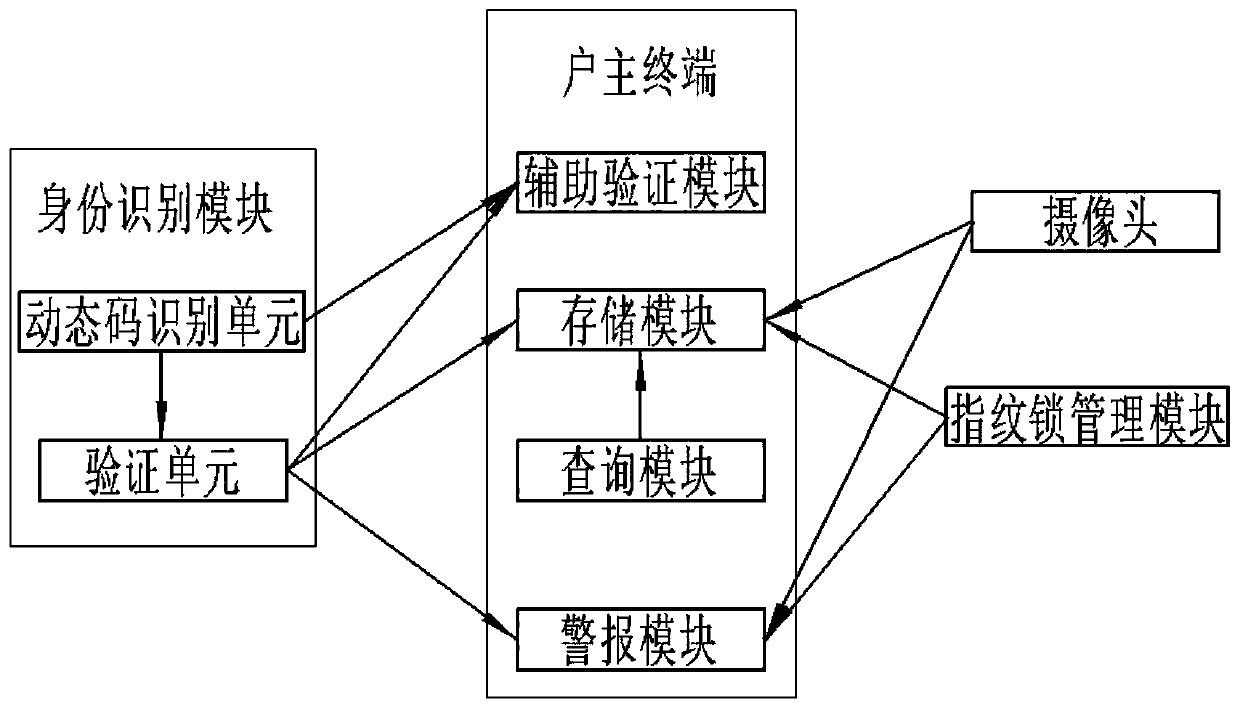
[0136] 1. After the user verification fails, the identity verification is not continued, and the stay time in front of the fingerprint lock is 15 minutes, and the head of the household terminal has no obvious response;
[0137] 2. After the user verification fails, the identity verification is not continued, and the stay time in front of the fingerprint lock is 25 minutes. The terminal of the head of the household sends out an alarm, and the head of the household gets the alarm.
[0138] 3. After the user verification fails, the identity verification is not continued, and the fingerprint lock is violently dismantled, the terminal of the head of the household sends out an alarm, and the head of the household gets the alarm.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com