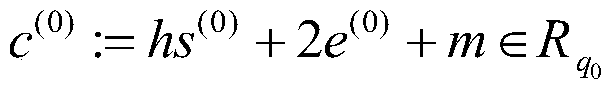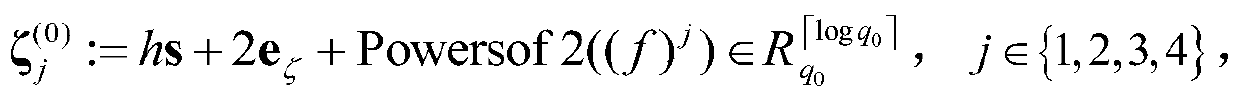An NTRU type multi-key fully homomorphic encryption method with a fast homomorphic operation process
A fully homomorphic encryption and multi-key technology, which is applied in the fields of information security and privacy protection, can solve the problems of being unable to add new users in real time, vulnerable to illegal organizations and users, snooping and attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
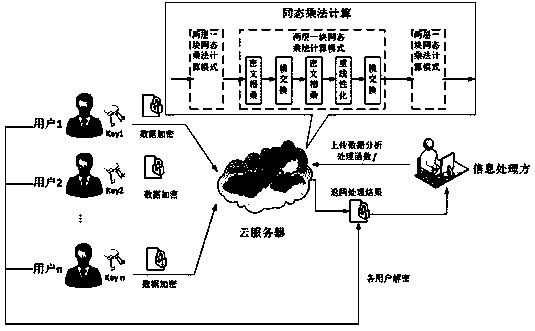
[0073] Such as figure 1 As shown, the NTRU type multi-key fully homomorphic encryption method with a fast homomorphic operation process comprises the following steps:
[0074] Step 1: Optimize the DHS16 scheme to construct a single-key fully homomorphic encryption scheme, which greatly reduces the number of relinearization operations in the homomorphic calculation process;
[0075] Step 2: Using the construction method of the multi-key fully homomorphic encryption scheme in the LATV12 scheme, transform the efficient single-user fully homomorphic encryption scheme in step 1 into a multi-key fully homomorphic encryption scheme;
[0076] Step 3: On the basis of the multi-key fully homomorphic encryption scheme in step 2, an independent distributed decryption process is constructed to reduce the inter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com