Linux platform process memory malicious code forensics method, controller and medium
A malicious code and process technology, applied in the field of network security, can solve the problem of lack of malicious code detection technology, and achieve the effect of avoiding complete acquisition and independent acquisition, the method is simple and accurate, and the security is improved
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
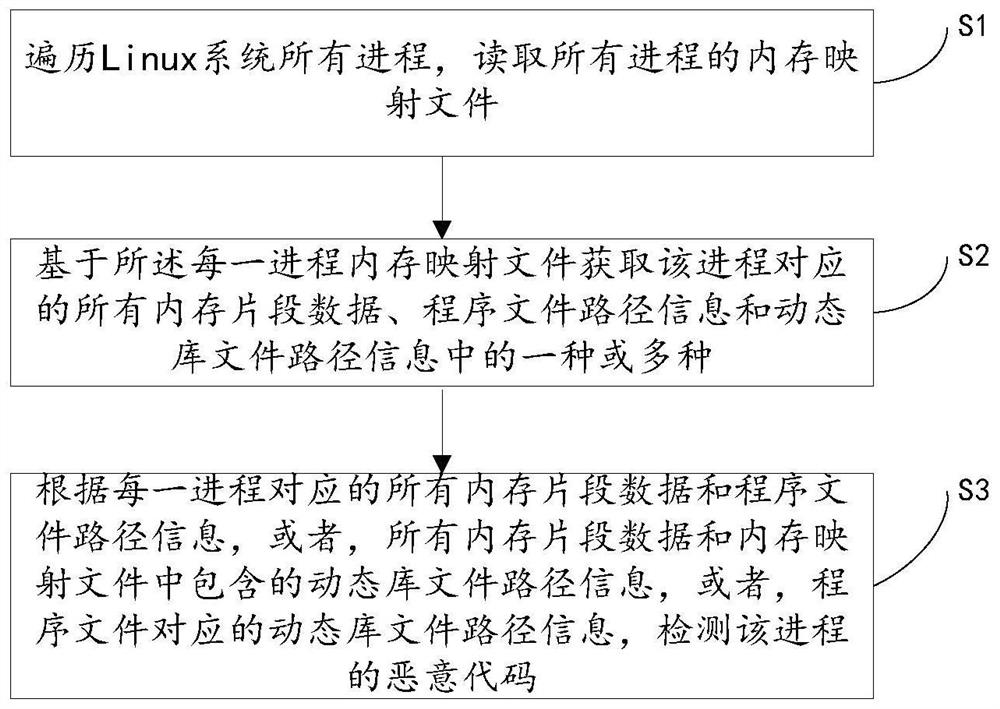
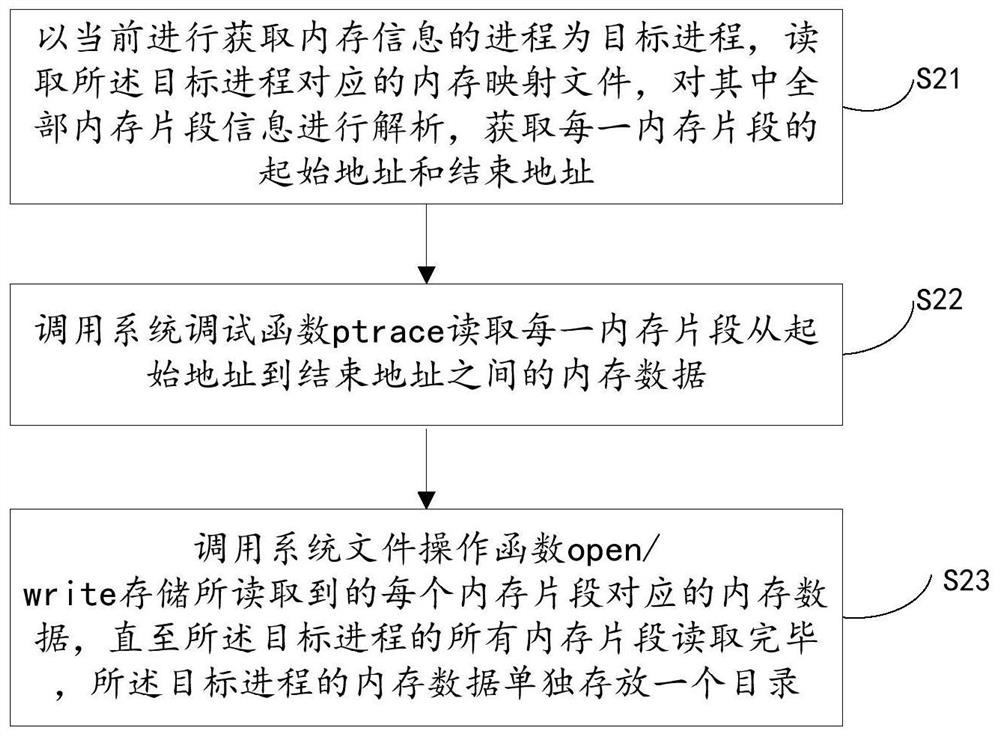
[0064] Detect malicious codes of the process based on all memory segment data and program file path information corresponding to each process, including:
[0065] Step S301. Obtain the preset code segment in the process memory according to all the memory segment data corresponding to each process;
[0066] Step S302, acquiring the program file according to the program file path information;
[0067] Step S303, analyzing the program header structure corresponding to the program file, and obtaining the preset code segment corresponding to the program file;
[0068] Specifically, by analyzing the elf structure of the program file, the corresponding program header structure is obtained. The program header contains the layout of the file in memory when the file is running. The program linker (a necessary tool in the code compilation process) connects many program segments (ie sections) are connected as a memory segment (segment), and each segment has a different purpose and memory...
Embodiment 2
[0071] Detect the malicious code of the process according to all the memory segment data corresponding to each process and the dynamic library file path information contained in the memory mapping file, including:
[0072] Step S311, acquiring the preset code segment in the process memory according to all the memory segment data corresponding to each process;
[0073] Step S312, obtaining the dynamic library file according to the dynamic library file path information contained in the memory-mapped file;
[0074] Step S313, analyzing the program header file corresponding to the dynamic library file, and obtaining the preset code segment corresponding to the dynamic library file;
[0075] Specifically, by analyzing the elf structure of the dynamic library file, the corresponding program header structure is obtained. As an example, the preset code segment is .text segment data.
[0076] Step S314 , comparing the preset code segment in the process memory with the preset code segm...
Embodiment 3
[0078] According to the dynamic library file path information corresponding to the program file corresponding to each process, the malicious code of the process is detected, including:
[0079] Step S321, according to the dynamic library file path information corresponding to the program file corresponding to each process, obtain the dynamic library file list corresponding to the process;
[0080] Step S322, obtaining the dynamic library file information contained in the memory-mapped file corresponding to the process;
[0081] Step S323, comparing the dynamic file information contained in the memory-mapped file with the list of dynamic library files;
[0082] Step S324, if the memory-mapped file contains one or more dynamic files not in the dynamic library file list, it means that there is malicious code, and the path of the dynamic library file and the corresponding memory segment data are output.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com