A safe, controllable and efficient data sharing method and system in a cloud computing environment
A cloud computing environment and data sharing technology, applied in transmission systems and key distribution, can solve the problem that verifiable outsourcing decryption schemes cannot provide data authentication functions, bottlenecks in the use of devices with limited computing resources, and the growth of decryption computing access control structures, etc. problem, to achieve the effect of reducing communication and computing overhead, facilitating the use of resource-constrained devices, and efficiently verifying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
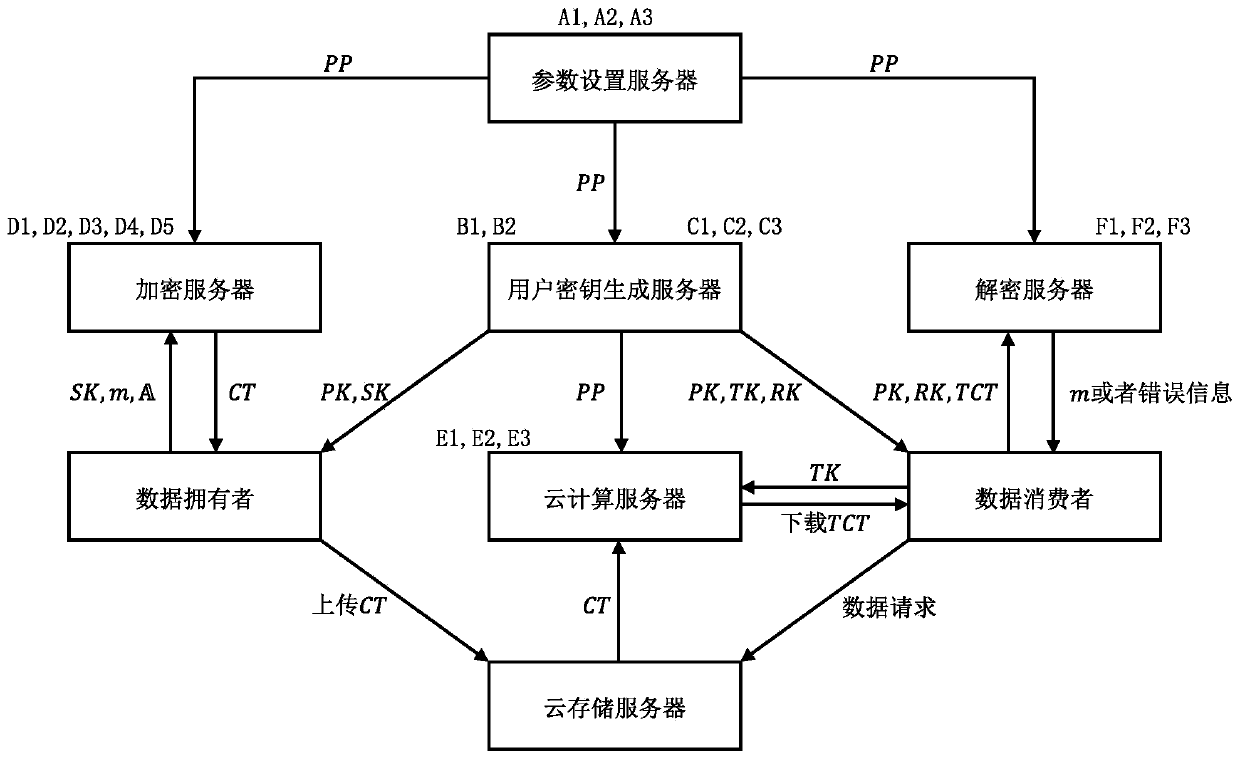
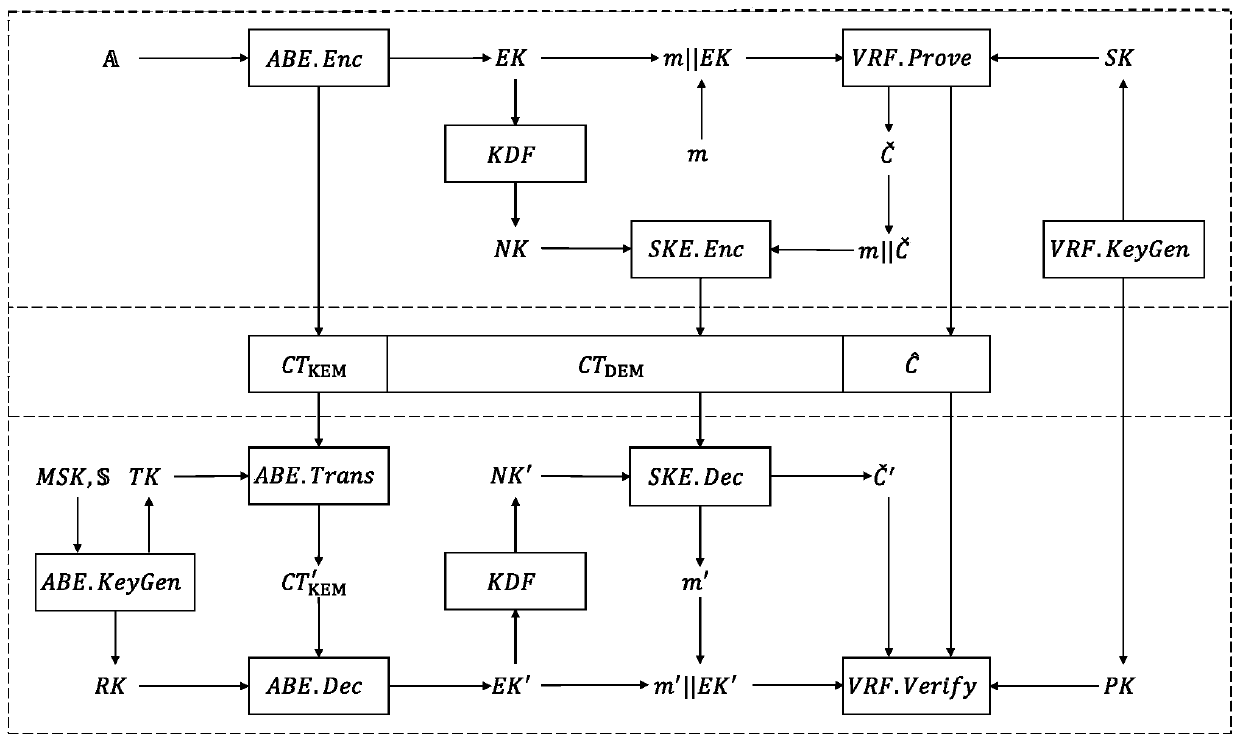
[0029] Attached below figure 1 with figure 2 The technical scheme of the present invention is described in further detail.
[0030] First, we introduce a safe, controllable and efficient data sharing method in a cloud computing environment and a cryptographic module required by the system.
[0031] 1. Attribute encryption algorithm ABE, including five sub-algorithms:
[0032] This scheme uses the attribute encryption algorithm ABE as the key encapsulation (KEM), so the description of the sub-algorithm is different from the general attribute encryption algorithm.
[0033] initialization algorithm Input the security parameter λ and the attribute space Output system public parameters PP and system master key MSK;
[0034] key generation algorithm Input system public parameter PP, system master key MSK and attribute set Output transformation key TK and recovery key RK;
[0035] Encryption Algorithm Input system public parameters PP and access control structure Out...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com