Trusted server policy deployment method, device, system and computing system
A technology for deploying systems and servers, applied in the field of policy deployment methods for trusted servers, systems and computing systems, and devices, can solve problems such as poor independence and flexibility, and achieve the effect of saving time and energy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] According to an embodiment of the present application, an embodiment of a trusted server policy deployment system is provided, which is used to deploy, update or delete related policies of trusted computing. It should be noted that this embodiment can be applied to the measurement of trusted servers in any network application or service system.
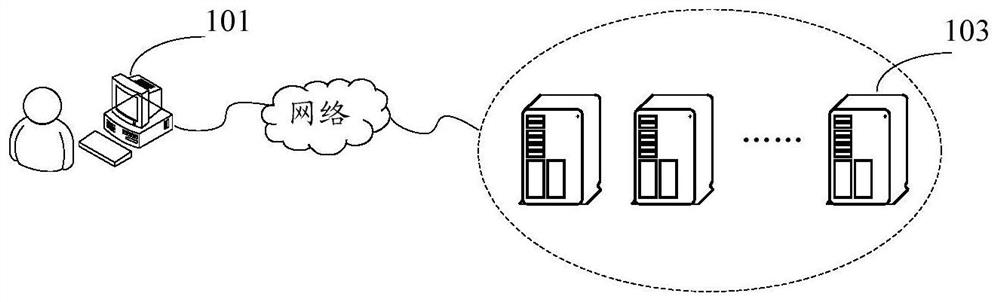
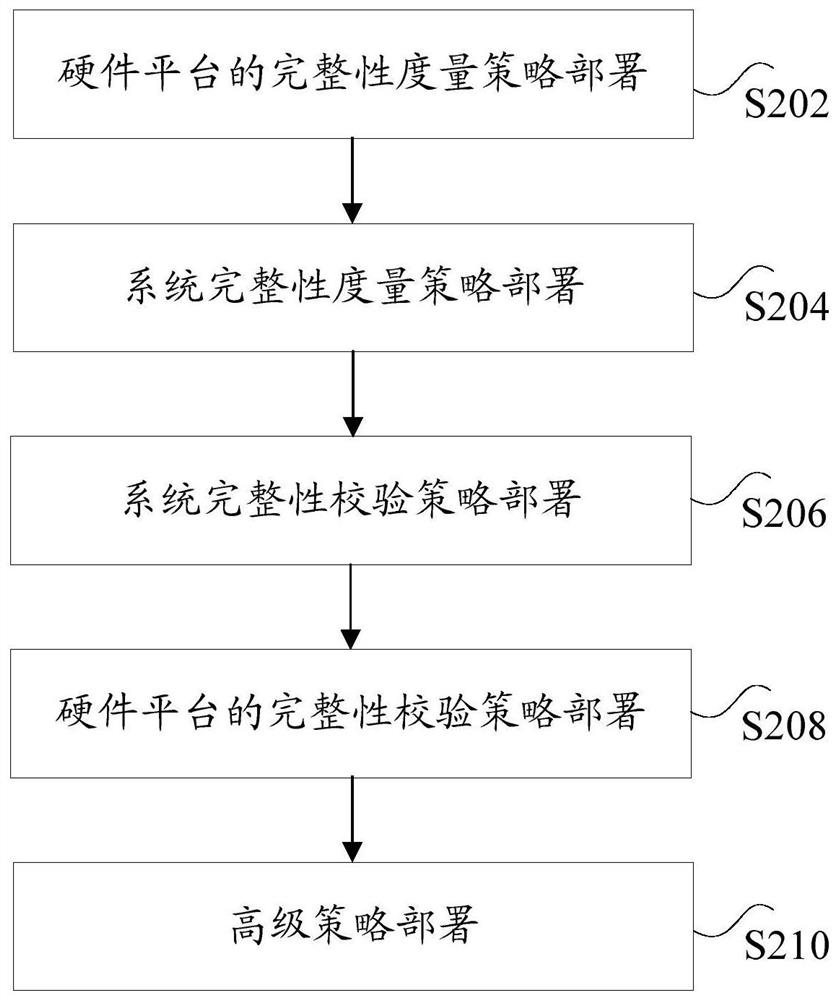
[0049] As an optional embodiment, figure 1 is a schematic diagram of an optional trusted server deployment system according to an embodiment of this application, such as figure 1 As shown, the system includes: a terminal device 101 and a trusted server 103, and a user can deploy relevant policies of the trusted server 103 by logging in locally or remotely to a single computer through the terminal device 101. figure 2 is an optional trusted server deployment flowchart according to the embodiment of this application, such as figure 2 As shown, the deployment process of the measurement strategy may include the following steps:...
Embodiment 2
[0058] According to the embodiment of the present application, a system embodiment of trusted server detection is also provided to overcome the problem of non-independence and flexibility caused by the strict hierarchical relationship in the deployment, update and deletion of trusted related policies in embodiment 1, It should be noted that this embodiment can be applied to the measurement of trusted servers in any network application or service system.
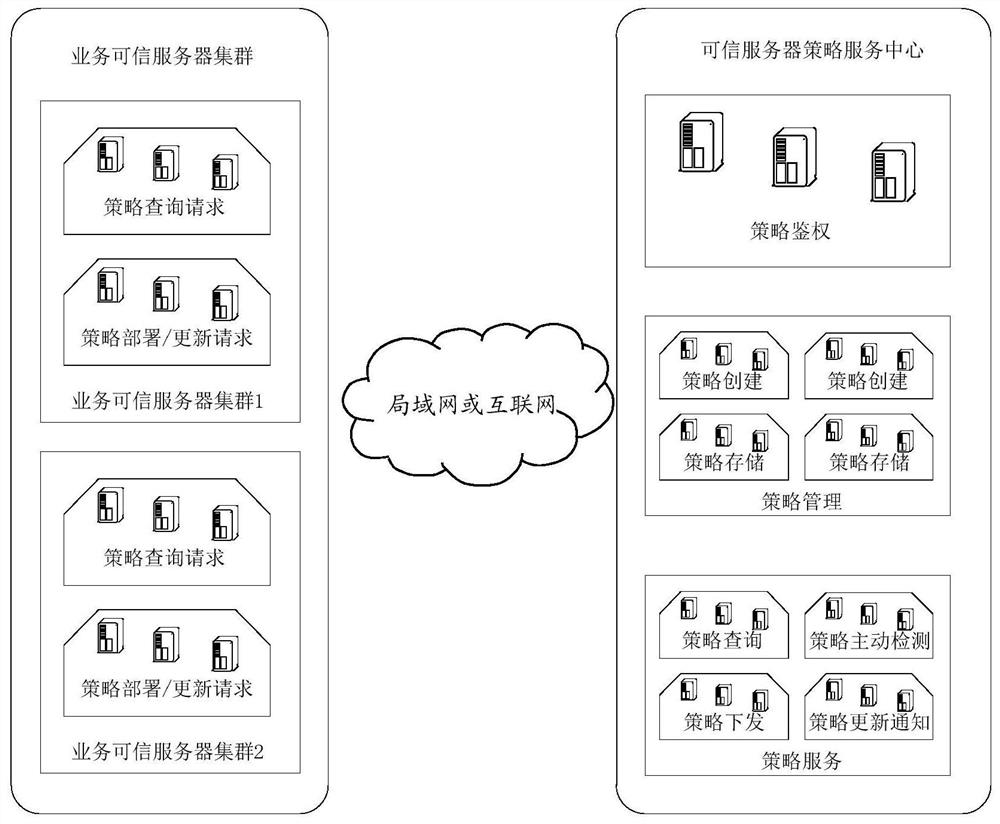
[0059] The inventor found through research that in order to realize the centralized management of trusted servers, a trusted server policy management platform based on cloud platform can be provided, its functions include but not limited to the initial deployment of trusted servers in various business environments, intelligent management and control and operation and maintenance etc. The trusted server policy management platform based on the cloud platform can not only simplify the trusted software and hardware environment co...
Embodiment 3
[0079] According to the embodiment of this application, an embodiment of a trusted server policy deployment method is also provided. This embodiment can be applied to the trusted server in the trusted server policy deployment system in Embodiment 2, including but not limited to implementing Scenario in Example 2. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here.
[0080] At present, in the existing trusted server strategy deployment scheme, the measurement algorithm and measurement object of the measurement strategy determine the measurement algorithm and measurement object of the verification strategy, and when the measurement algorithm of the verification strategy is inconsistent with the measurem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com