IPv6 network node data security transmission method
A network node and node data technology, applied in the IPv6 network field, can solve the problems of the D-H key agreement system no longer safe, the difficulty of application in the embedded physical network field, and potential safety hazards, so as to improve convenience and key relay path Safety, the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] According to Figure 1 to Figure 6 The specific implementation of the present invention is further explained:
[0043] This embodiment provides a method for secure transmission of IPv6 network node data, including:
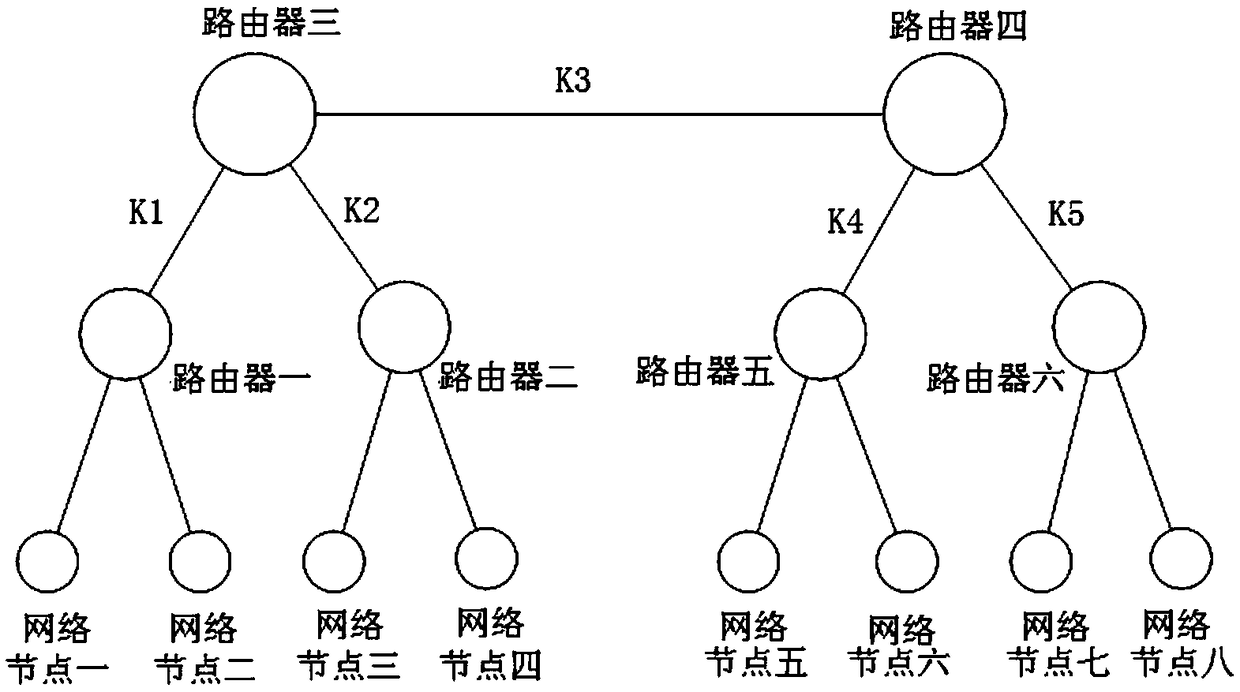
[0044] Step 1: Network node one (also can be expressed as network node A, the expression is not limited, all represent IPv6 network nodes) according to the routing path sequence, send the encrypted communication request packet to network node five through multiple routers (also can be expressed as network Node B, the expression method is not limited, all represent IPv6 network nodes);
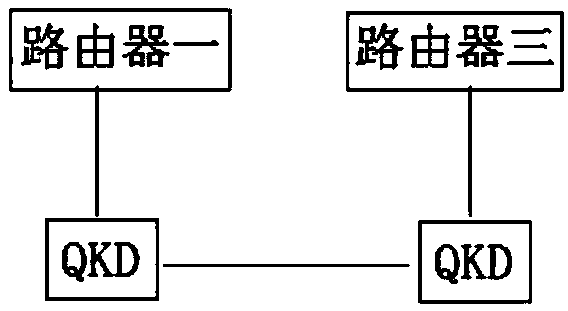
[0045] Step 2: Network node five shares a set of key data K with network node one through a key relay path consistent with the routing path;
[0046] Step 3: Network node 1 combines the key data K, the IP address of network node 1 and the IP address of network node 5 to obtain a new set of key K AB ;
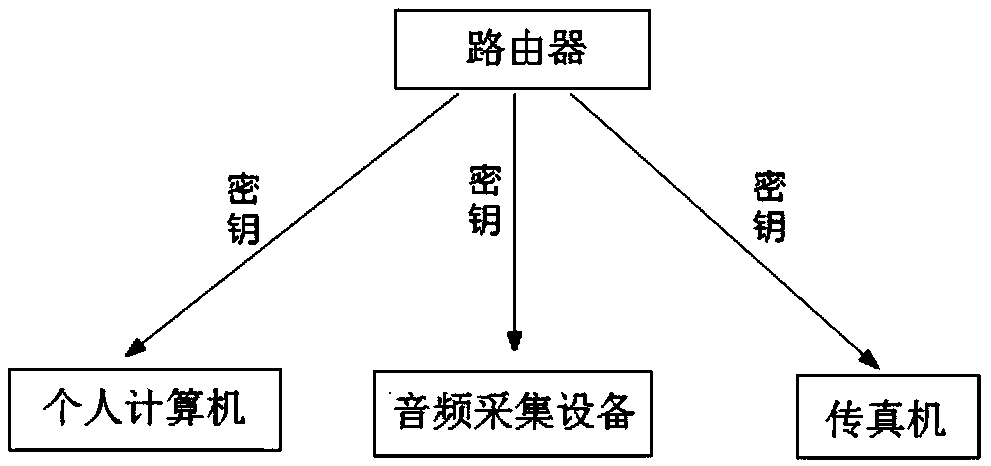
[0047] Step 4: Network node one uses the calculated new key K AB Encrypt and pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com