A suspect early warning method and system based on face recognition
A face recognition and early warning system technology, applied to the suspect early warning method and system field based on face recognition, can solve the problems of low efficiency, inaction in work, unclear bus activities of suspects, etc. Achieve the effect of saving data resources, precision features, and fast speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
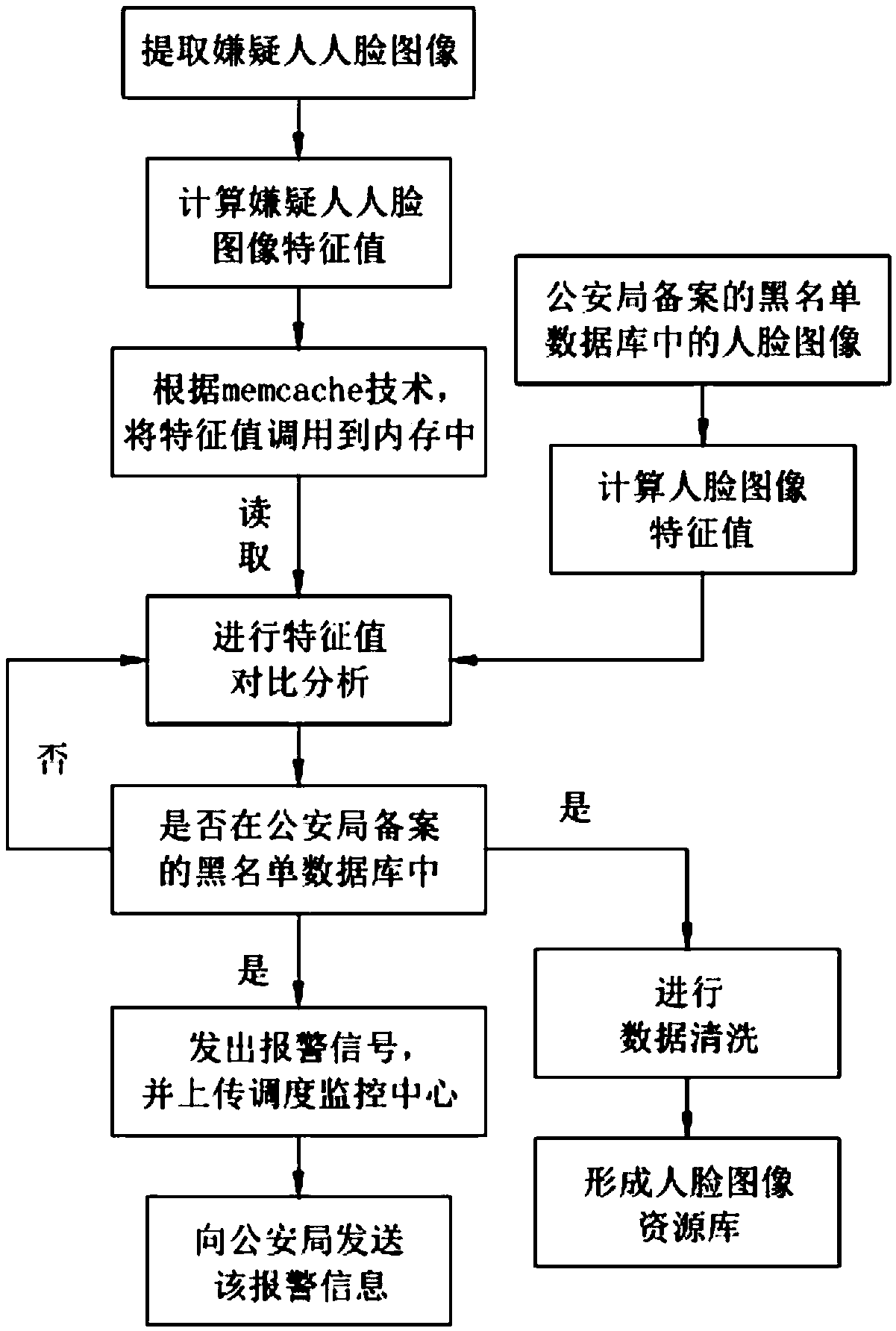
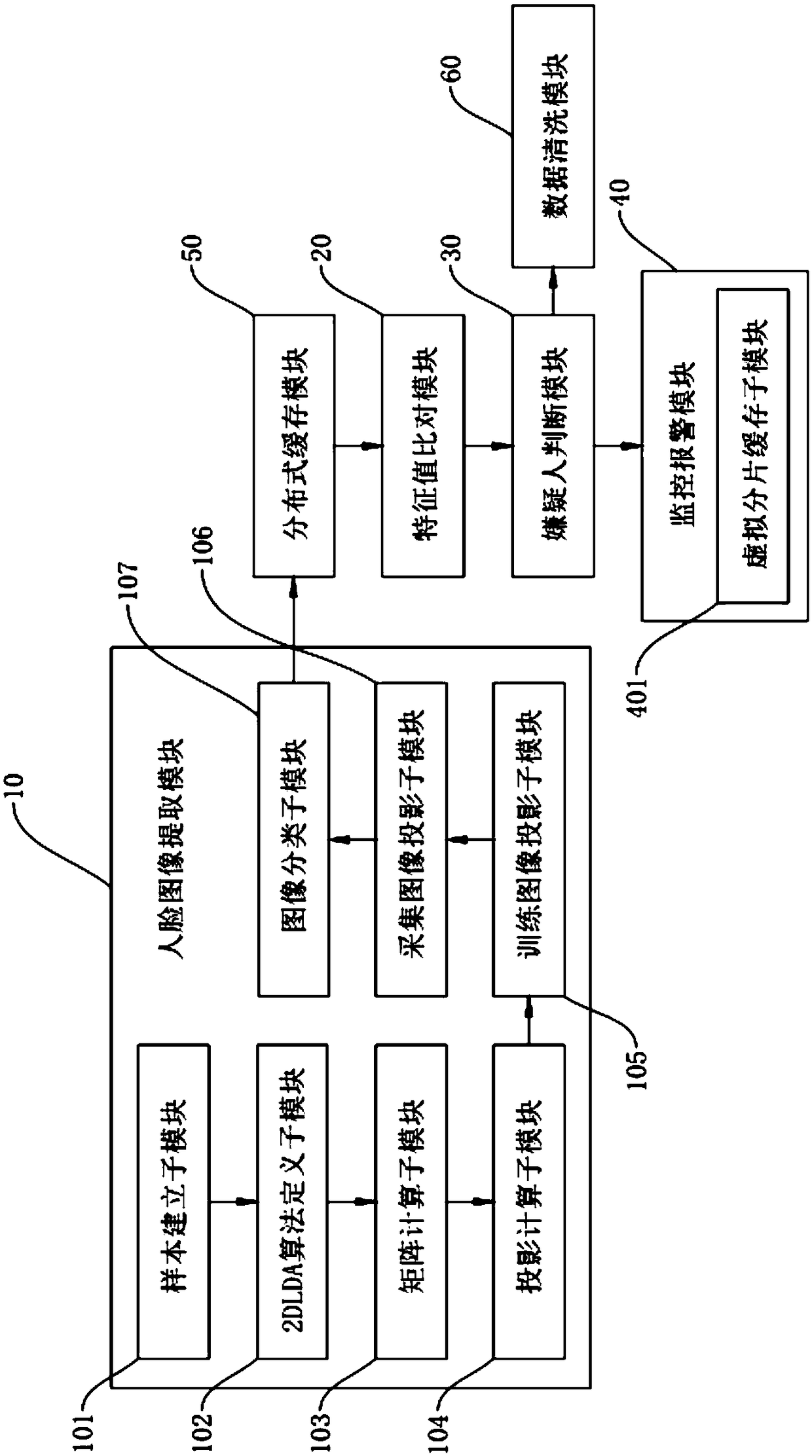
[0069] Such as figure 1 As shown, a suspect early warning method based on face recognition includes the following steps:
[0070] a. Extract the face image of the suspect, and calculate the feature value of the face image of the suspect;
[0071] b. Compare and analyze the feature value of the suspect's face image with the feature value of the face image in the blacklist database filed by the Public Security Bureau;
[0072] C, judge whether this suspect's facial image feature value is recorded in the blacklist database of public security bureau filing, if yes, then send alarm signal to driver, enter step d; If not, then enter step b again;
[0073] d. The dispatch monitoring center automatically receives the alarm signal, retrieves the monitoring video, and sends the alarm information to the Public Security Bureau.
[0074] In this embodiment, when a person boards the vehicle, the face image of the person boarding the vehicle is collected through the infrared high-definitio...
Embodiment 2
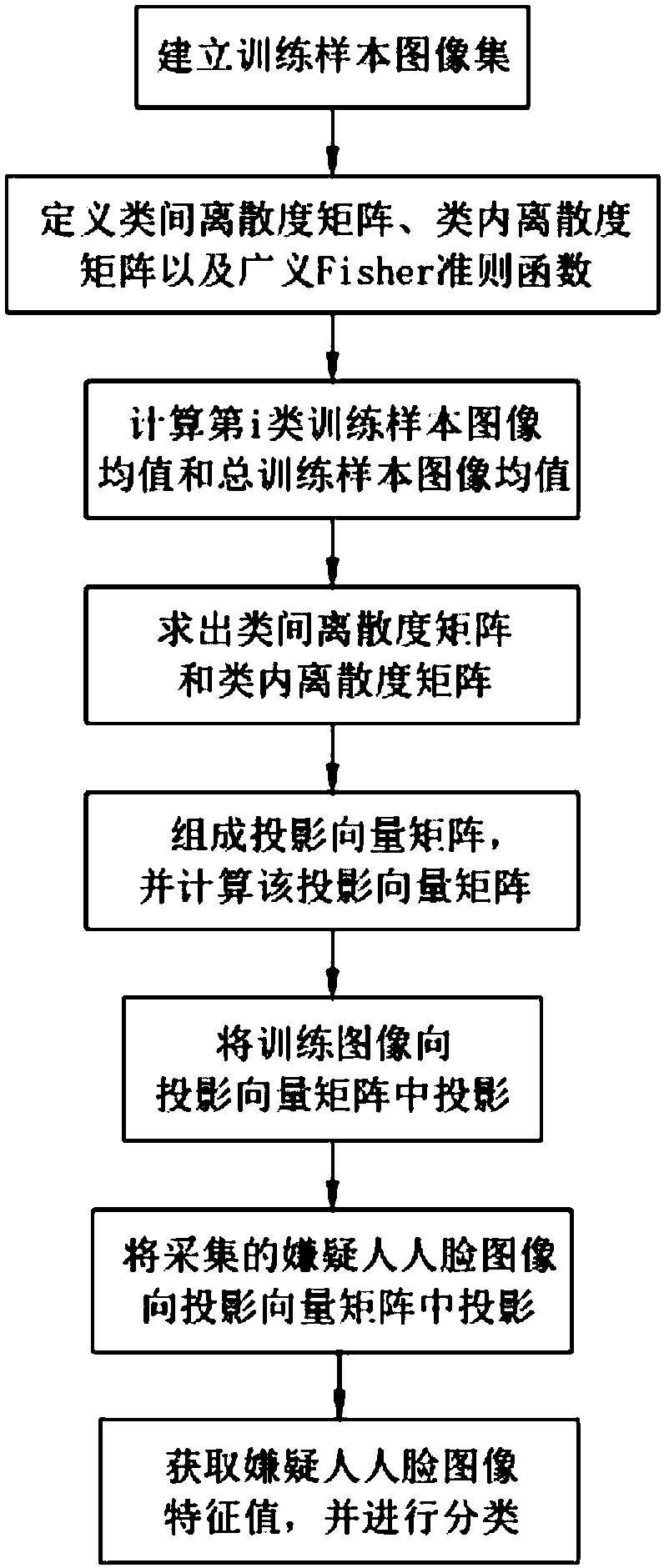
[0076] This embodiment is on the basis of embodiment 1, as figure 2 As shown, the step a includes the following steps:
[0077] a101. Establish training sample image set There are C categories of images, each category n i of which, X k Indicates the kth training sample image, N is the total number of training sample images;
[0078] a102. Define the inter-class dispersion matrix Intra-class dispersion matrix and the generalized Fisher criterion function J F (W)=W T SB W / W T S W W; where, and respectively represent the mean value of the i-th class training sample image and the mean value of the total training sample image, T is the transpose, and W is the best projection direction;
[0079] a103, according to the mean value of the i-th class training sample image calculated and the mean of the total training sample images Calculate the inter-class scatter matrix and intra-class scatter matrix of the training sample image set;
[0080] a104, take The orth...
Embodiment 3
[0086] On the basis of embodiment 2, this embodiment also includes the following steps:
[0087] According to the distributed cache memcache technology, the obtained feature value of the suspect's face image is called into the memory, and when it needs to be called, it is read from the memory. Using the distributed cache memcache technology, the face recognition technology has the characteristics of fast speed and high precision; and it ensures high-performance access to data. When there is no more space in the memory to store new data, memcache will Use the LRU (Least Recently Used) algorithm to eliminate recently infrequently accessed data to make room for new data and save data resources.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com