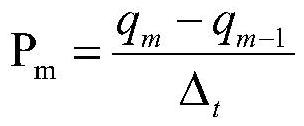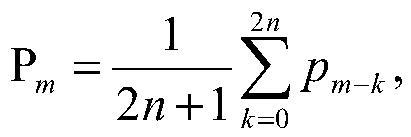A Method of Combining Symbolic Execution to Improve the Efficiency of Software Fuzz Testing
A technology of fuzz testing and symbolic execution, applied in software testing/debugging, error detection/correction, instrumentation, etc., which can solve the problems of high complexity, blindness of test cases, low code coverage, and inability to be well compatible with non-source code Binary programs and other issues to achieve the effect of improving overall performance and improving defect mining performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
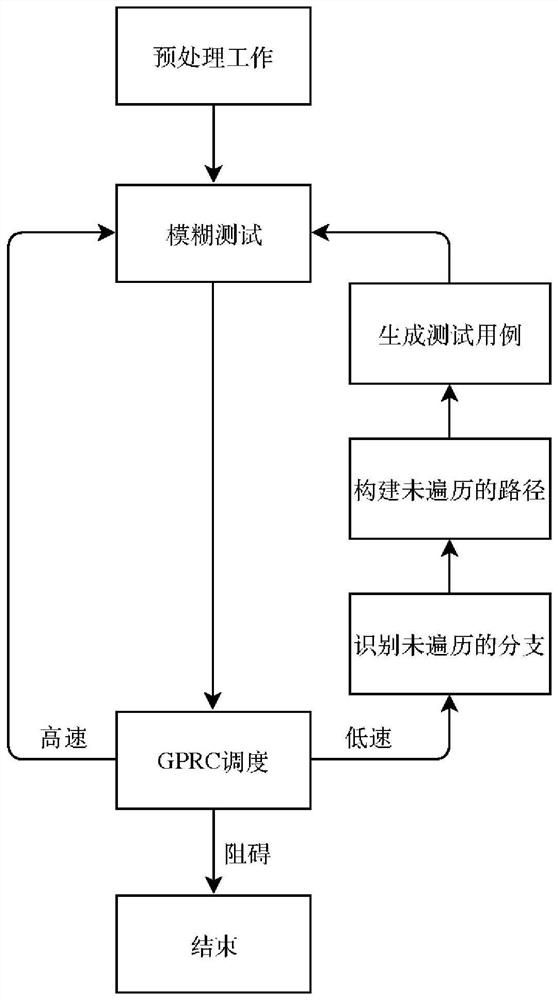
[0049] Such as figure 1 As shown, the present embodiment combines symbolic execution to improve the method for software fuzz testing efficiency, and the steps include:
[0050] S1. Preprocessing: perform preprocessing on the target program including disassembly, stub insertion, etc., and obtain information including assembly code, control flow graph CFG, etc. of the target program;
[0051] S2. Fuzz testing: input the fuzz tester to the target program to generate test cases, and detect whether the program is abnormal. If a program abnormality occurs, record the corresponding test case, that is, record the test case that can trigger the program abnormality;
[0052] S3. Scheduling based on path coverage: construct scheduling parameters for scheduling based on pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com