A physical layer security transmission method based on subcarrier sorting and xor operation in ofdm system
A technology of physical layer security and transmission method, applied in the field of physical layer security transmission, can solve the problems of difficulty in obtaining eavesdropper channel state information, without considering the situation of active eavesdroppers, and difficulty in guaranteeing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
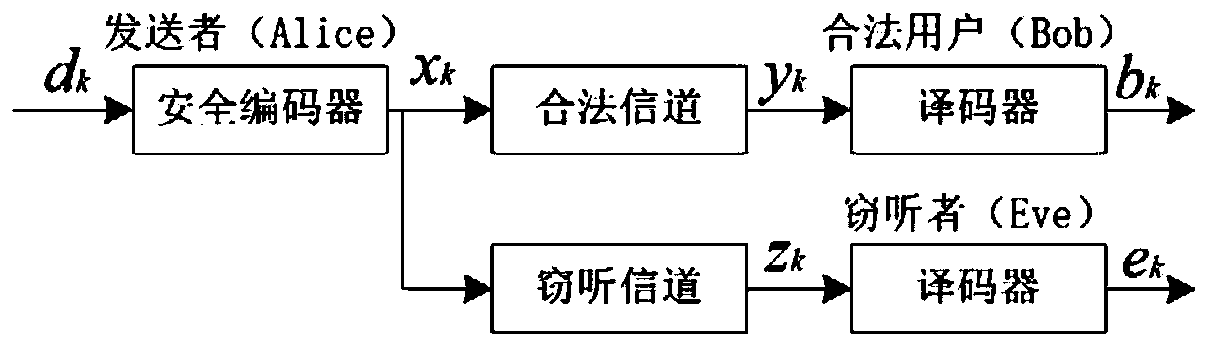
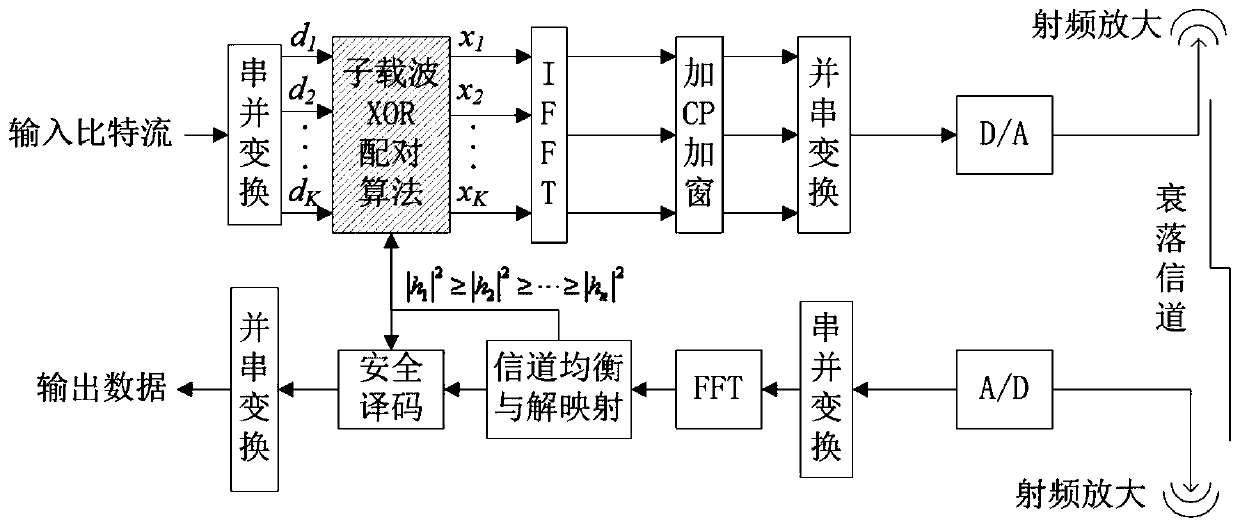
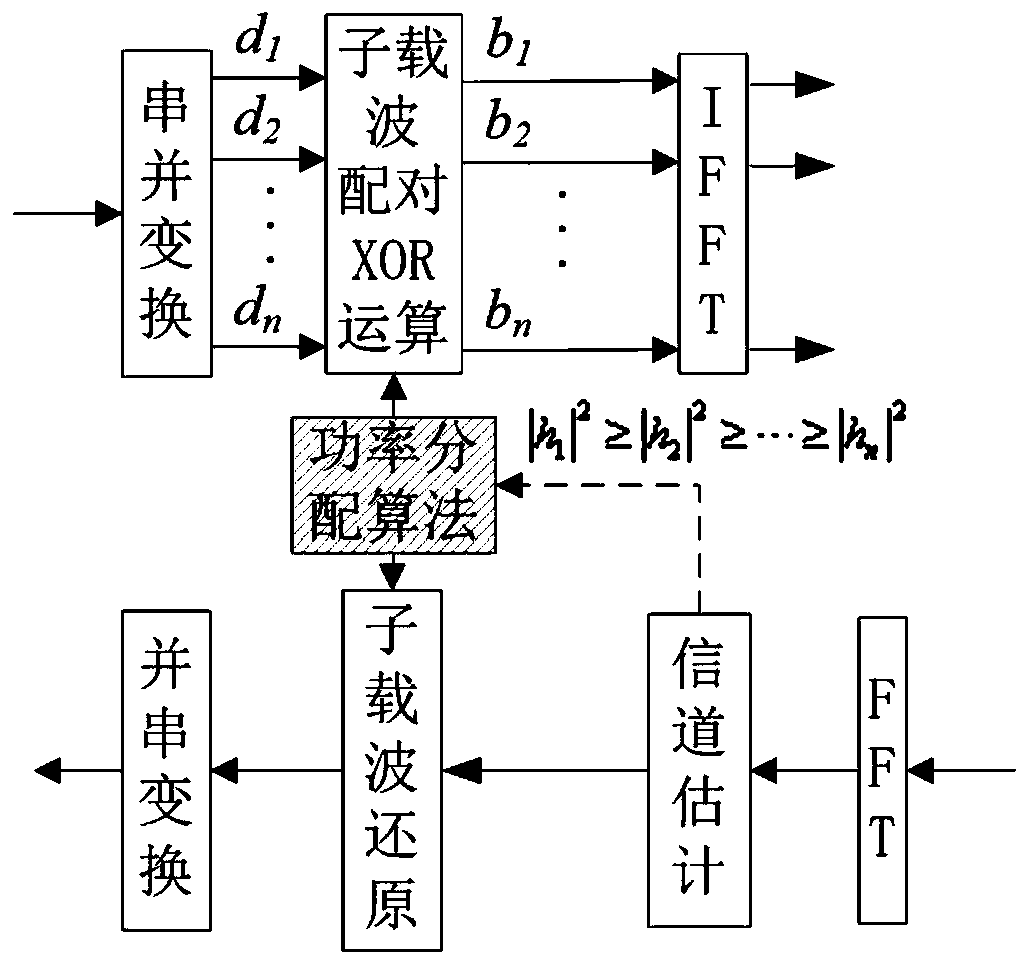
[0076] The present invention designs a physical layer security transmission algorithm based on subcarrier sorting and XOR operation for a wireless transmission system in which the three-node physical layer security model adopts OFDM modulation technology. Considering a TDD system, the uplink and downlink channels are different. Before information transmission, the sending end and the legal user send training sequences to each other in time intervals, and the two ends perform channel estimation respectively to obtain main channel information.
[0077] In the information transmission stage, the sending end will encrypt the sending information according to the main channel characteristics obtained through channel estimation. The specific method is to sort the subcarriers according to the channel quality of each subcarrier, and divide the subcarriers into two parts, the subcarriers with better channel quality in the first half and the subcarriers with poorer channel quality in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com