Verifiable privacy protection single-layer perceptron batch training method
A single-layer perceptron, privacy protection technology, applied in digital data protection, computer security devices, biological neural network models, etc., can solve the problems of slow iterative convergence, inability to achieve multi-model training tasks, and model training without verification functions. , to achieve the effect of privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
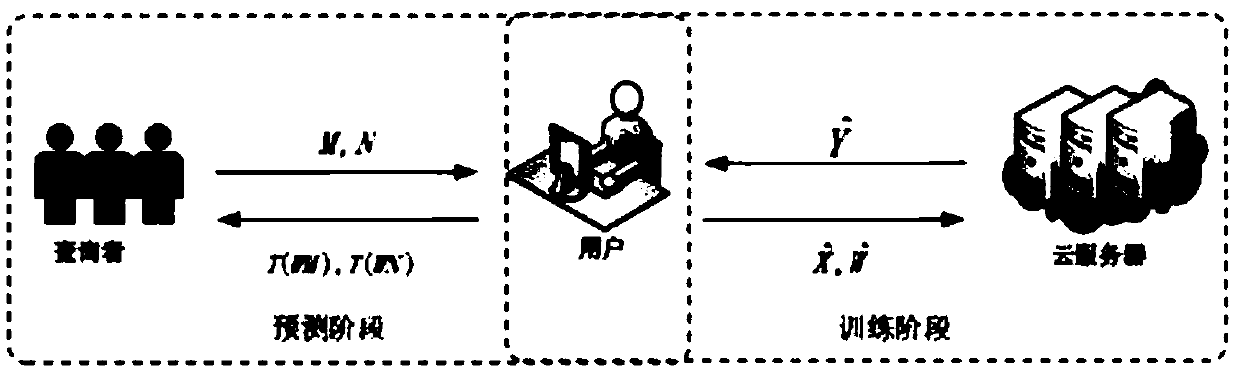
[0064] The present invention supports batch processing model training and verifiability of the returned results by the client; adopts the classic two-party security calculation method, adopts a new lightweight privacy protection model prediction method, and both participants can protect themselves privacy input information. Safety analysis can prove that the present invention has reached safety characteristics. At the same time, the performance evaluation of the scheme is realized on two real data sets, and the experimental results and analysis show that the present invention has high efficiency and practicability.
[0065] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com