Security chip-based trusted startup method
A security chip and secure boot technology, applied in computer security devices, instruments, platform integrity maintenance, etc. problems, to achieve the effect of simplifying the difficulty of hardware design, reducing the difficulty of development, and reducing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
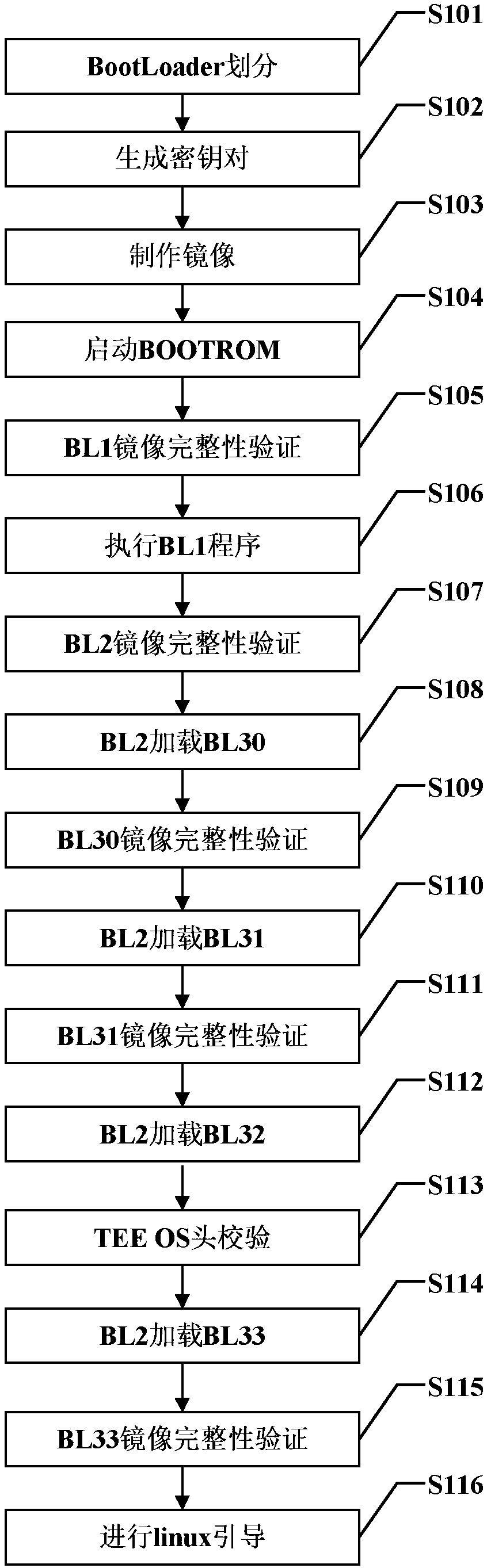
[0035] figure 1 It is a specific implementation flow chart of the security chip-based trusted startup method of the present invention. Such as figure 1 As shown, the specific steps of the trusted startup method based on the security chip of the present invention include:
[0036] S101: BootLoader division:
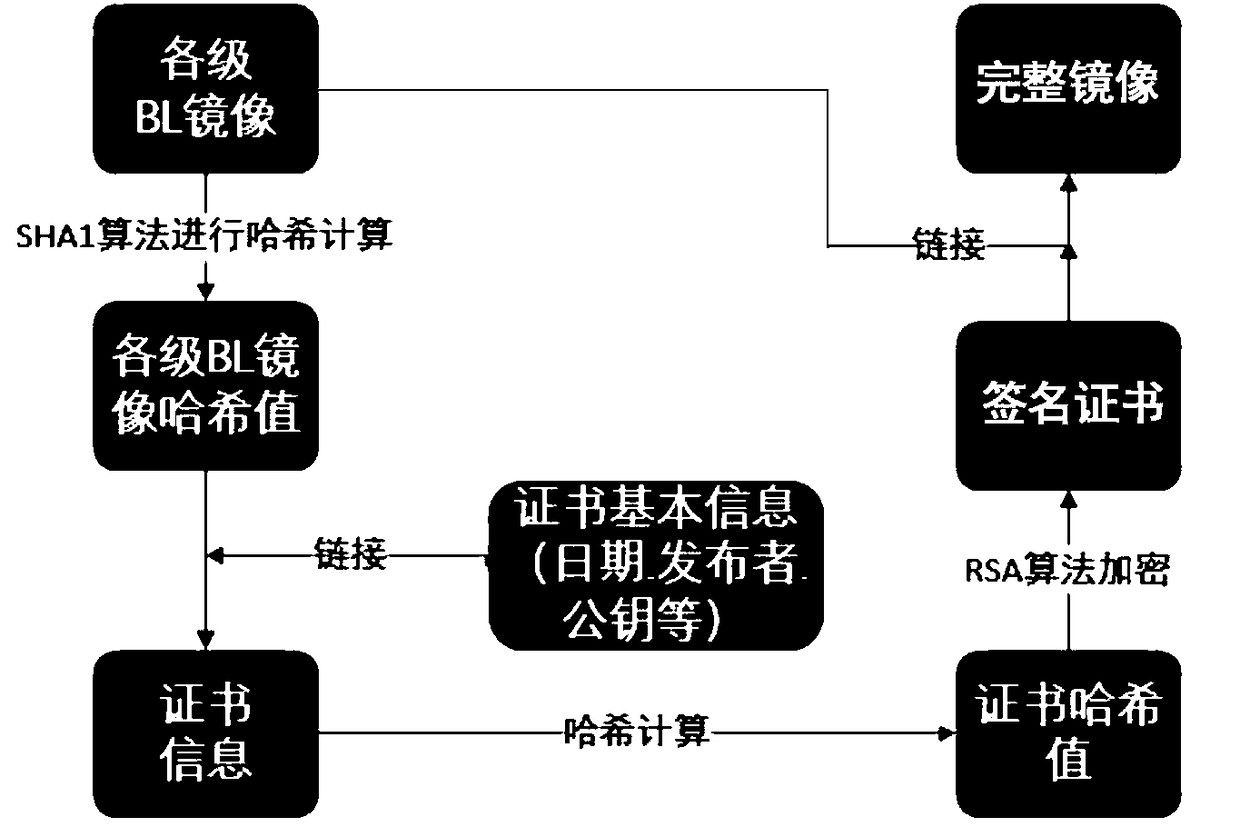
[0037]Boot Loader is a program that runs before the operating system kernel runs. Through this program, hardware devices can be initialized and a map of memory space can be established to bring the system's hardware and software environment to a suitable state for the final call operation. The system kernel prepares the correct environment. In the present invention, firstly, according to the different functions of each part in the secure boot process, the BootLoader is divided into 6 parts, which are respectively BL1 program, BL2 program, BL30 program, BL31 program, BL32 program, and BL33 program, wherein the BL1 program is used to set Exception vector table, initializ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com