Method and system for executing security operation by using security device
A technology for safe operation and safety equipment, applied in the field of electronics, can solve problems such as unfavorable work efficiency, inability to provide better user experience, inability to operate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
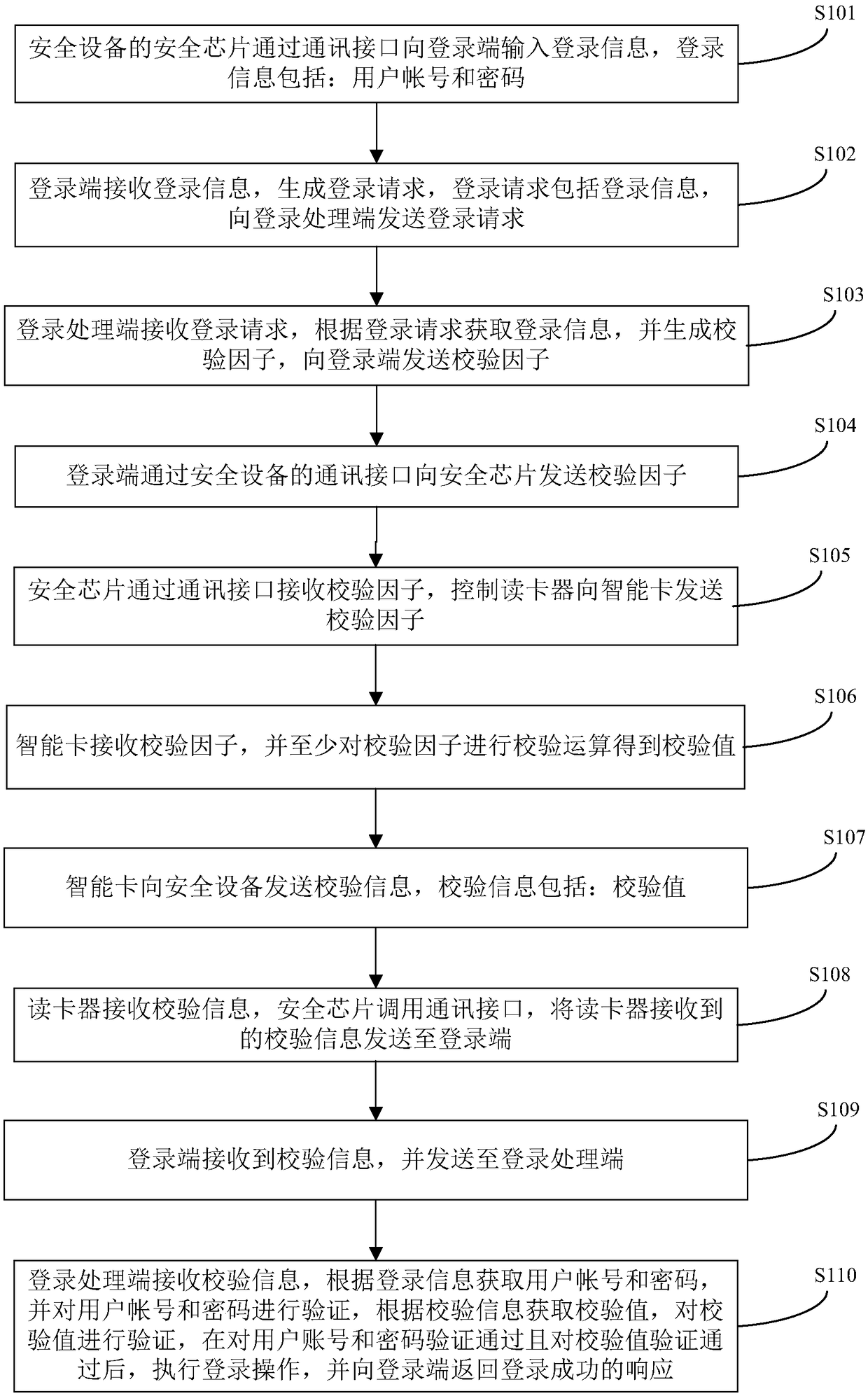
[0045] This embodiment provides a method for using a security device to perform a security operation, using the system architecture mentioned above. The method specifically includes a step of using a security device to read a card to log in (S101-110) and a step of using the security device to control and execute a security operation after logging in (S111-S120).
[0046] Specifically, such as image 3 As shown, the steps of using the security device to read and log in provided by this embodiment are as follows (steps S101-S110):
[0047] In step S101, the security chip of the security device inputs login information to the login terminal through the communication interface, and the login information includes: user account number and password.
[0048] The security chip (such as Z8D64U (national secret batch number SSX43) and Z32 (national secret batch number SSX20) of National Technology Co., Ltd.) has an independent processor and storage unit inside, which can store PKI dig...
Embodiment 2
[0107] This embodiment also provides a method for using a security device to perform a security operation, using the system architecture mentioned above. The difference between this method and the method provided in Embodiment 1 is that the security chip does not make a judgment after receiving the first collection information, but calls the communication interface to send the first collection information to the login terminal, and the login terminal makes a judgment. And execute a security operation or send a security operation request to the login processing end according to the judgment result.
[0108] Among them, the steps of using the security device to read the card to log in are the same as those in Embodiment 1, and will not be repeated here. Please refer to the attached image 3 . Such as Figure 5 As shown, the steps of using the security device control to perform security operations after logging in include (S211-S218):
[0109] Step S211 to step S214 are the sa...
Embodiment 3
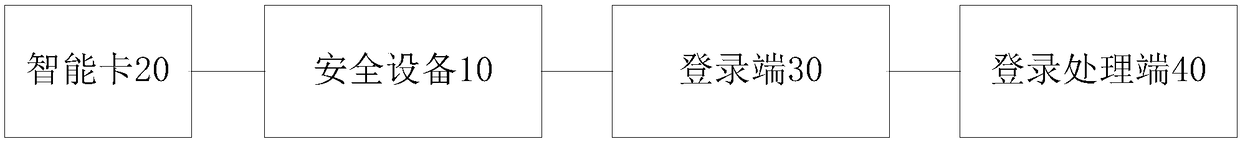
[0115] This embodiment also provides a system for using security equipment to perform security operations. Adopt the method for utilizing the safety device of embodiment 1 to perform safety operation, its specific structure is as follows figure 1 and figure 2 shown. For specific device functions, refer to the specific description in Embodiment 1. This embodiment is only briefly described.
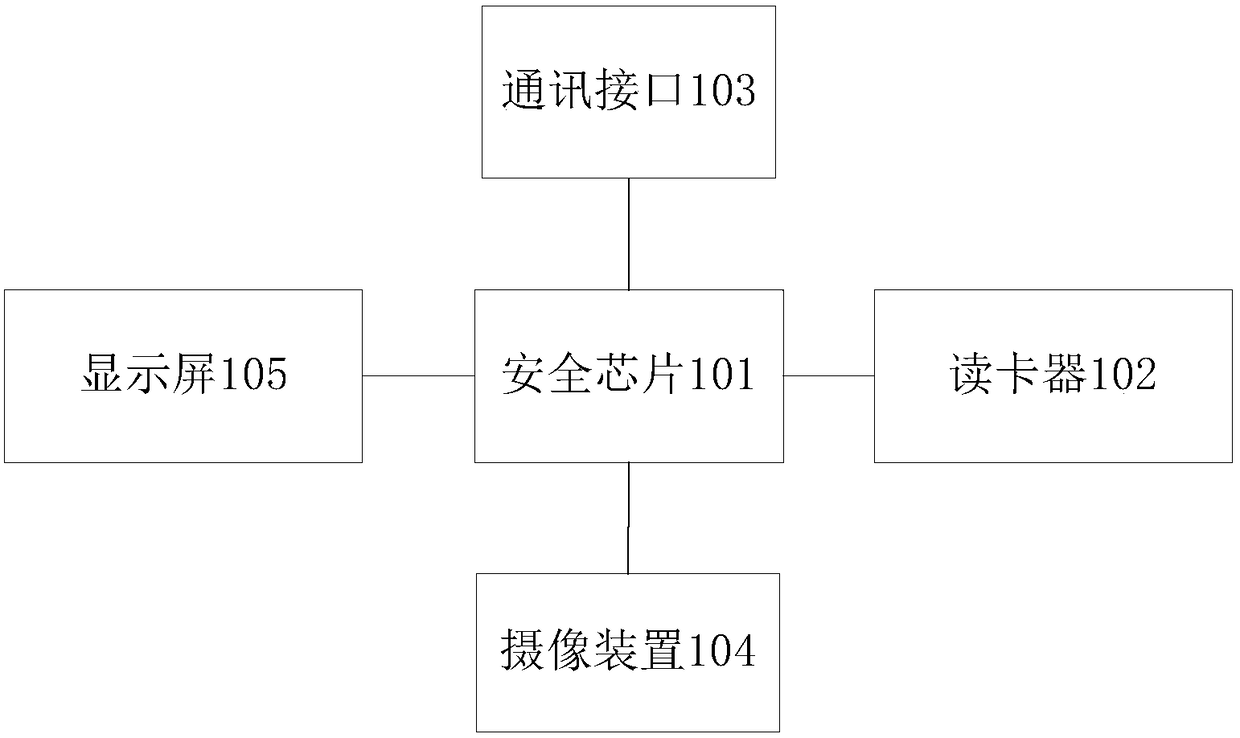
[0116] Such as figure 1 and figure 2 As shown, the system using security devices to perform security operations includes: a security device 10 , a smart card 20 , a login terminal 30 and a login processing terminal 40 . Wherein, the security device 10 includes: a security chip 101, a card reader 102, a communication interface 103 and a camera 104;
[0117] The security chip 101 is used to input login information to the login terminal 30 through the communication interface 103. The login information includes: user account number and password; it is also used to receive the check fact...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com