Host machine monitoring system based on plugin architecture
A monitoring system and plug-in technology, applied in the field of network security, can solve the problems that terminal computer security functions cannot be added, modified or deleted, terminal users are difficult to know the terminal status security policy, and administrators are difficult to ensure performance degradation or even crashes. , to achieve the effect of ensuring high concurrency and high fault tolerance, reducing communication overhead, and high customizability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
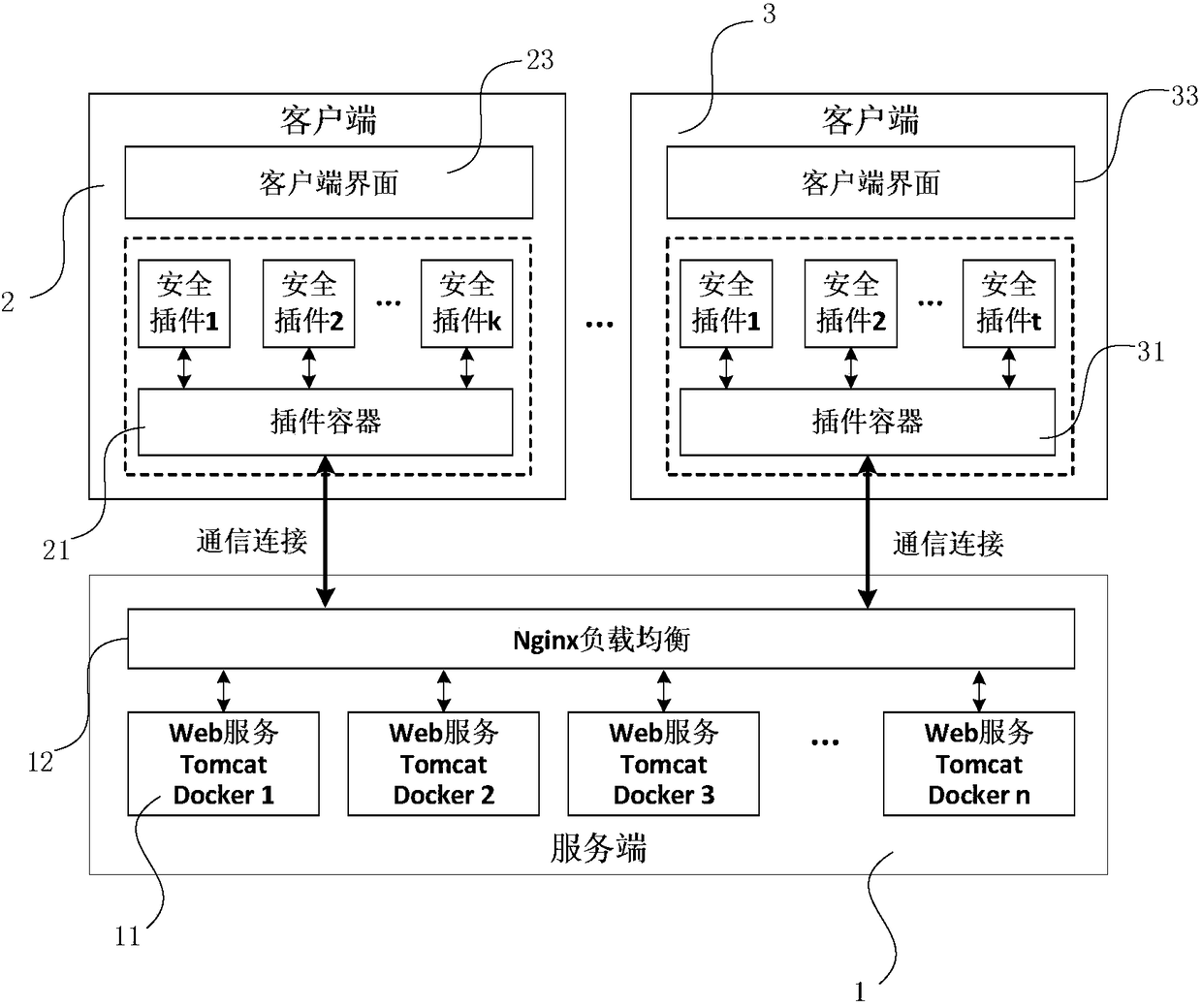
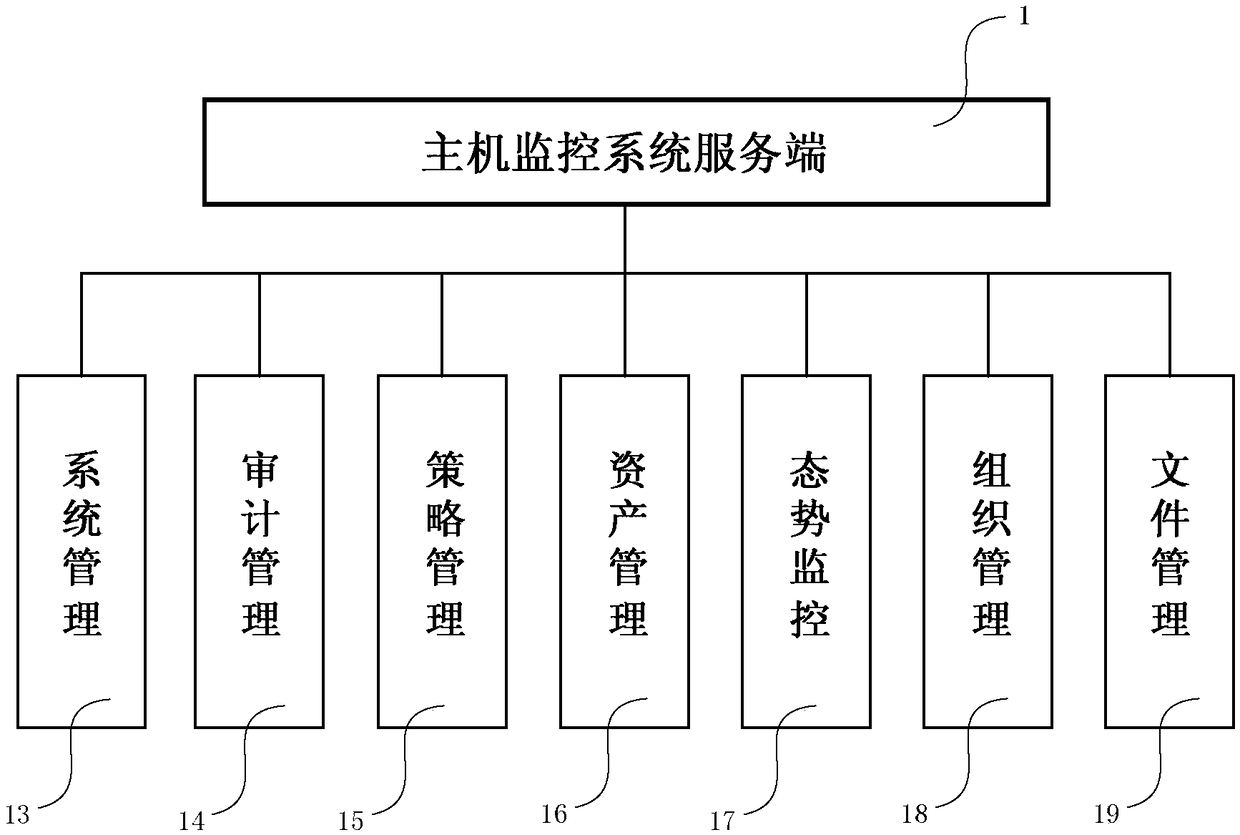
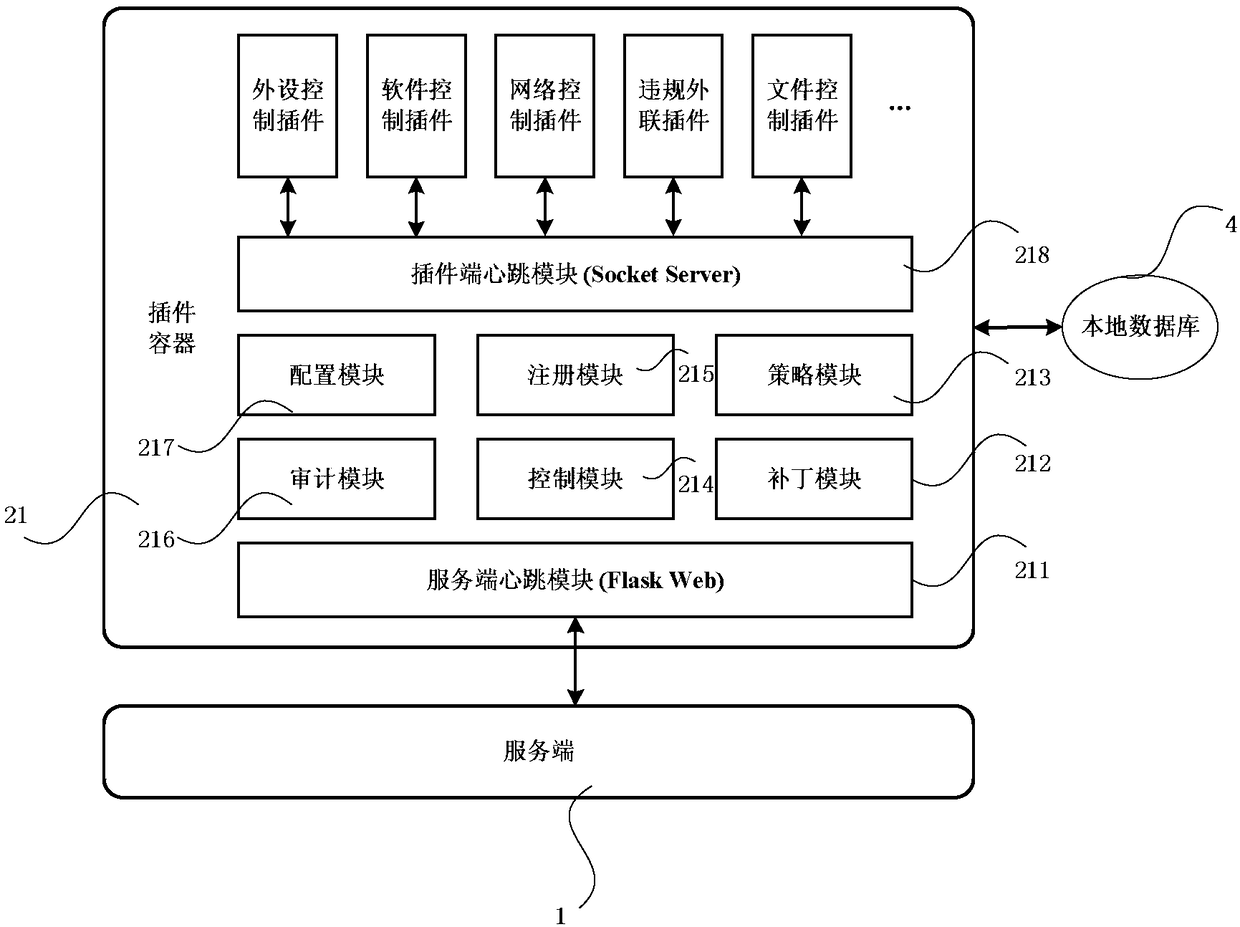
[0025] figure 1 Shown is the module diagram of the host monitoring system based on the plug-in architecture of the present invention, as figure 1 As shown, the host monitoring system based on the plug-in architecture of the present invention is mainly composed of two parts: a server and a client. This embodiment includes a server 1 , a client 2 and a client 3 . The client 2 includes: a plug-in container 21 , security plug-ins 1-k, and a client interface 23 . The client 3 includes: a plug-in container 31 , a security plug-in 1-t, and a client interface 33 .
[0026] Such as figure 1 As shown, in order to meet the high concurrency requirements generated by tens of thousands of terminals, the server uses Nginx load ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com