L algorithm-based digital currency anti-counterfeiting and verification method and system and equipment
A digital currency and verification method technology, applied in the field of information security, can solve problems such as ignoring the anti-counterfeiting value of digital currency, difficult to solve anti-counterfeiting problems, loss of asset ownership, etc., to avoid the problem of massive data downloading, high effectiveness, and less online interaction Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
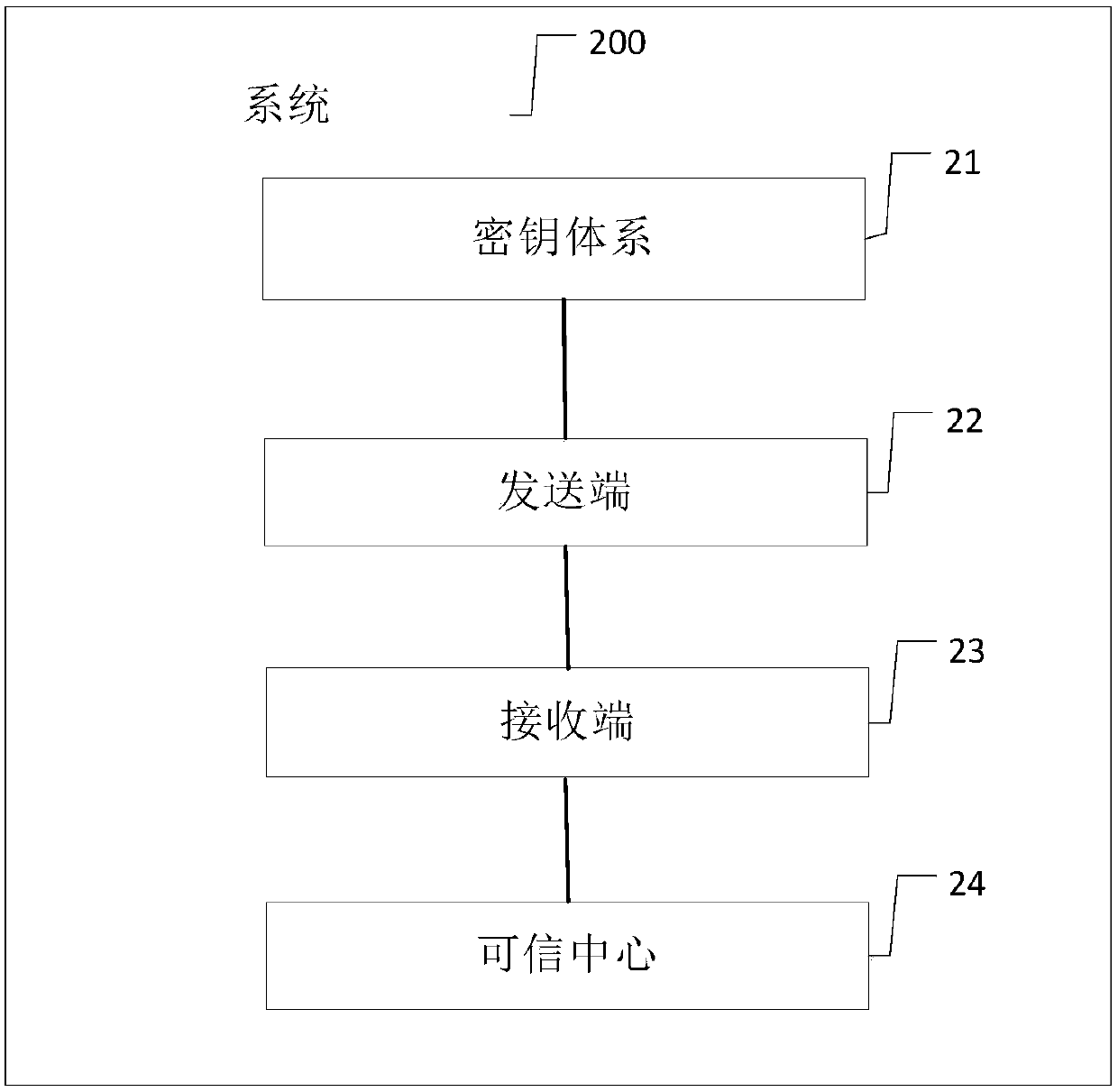
[0109] refer to figure 1 , figure 1 A flow chart of an embodiment of an L algorithm-based digital currency anti-counterfeiting and verification method provided by the present invention is shown. The method includes: step one to step four.
[0110] Step 1. Split the anti-counterfeiting key corresponding to the digital currency public key stored in the trusted center into a stub key stored in the trusted center, a digital currency key stored in the digital currency, and a user key stored in a non-terminal.
[0111] Among them, the digital currency public key stored in the trusted center and its corresponding anti-counterfeiting key satisfy the following relationship:
[0112] [L 0 L 1 L 2 ] -1 G=P+G;
[0113] Among them, L 0 is the stub key; L 1 is the digital currency key; L 2 is the user key; P is the digital currency public key; G is the base point of the elliptic curve. All three keys must be calculated correctly in order to pass the public key verification and ac...
Embodiment 2
[0152] Embodiment 2 of the present invention provides a digital currency anti-counterfeiting and verification method based on the L algorithm. The method is described from the sending end side. The method includes:
[0153] Split the anti-counterfeiting key corresponding to the digital currency public key stored in the trusted center into a stub key stored in the trusted center, a digital currency key stored in the digital currency, and a user key stored in a non-terminal;
[0154] The sending end updates the digital currency key through the stored digital currency key, the sending end user key and the receiving end update parameters sent by the receiving end, and uses the receiving end encrypted public key sent by the receiving end to encrypt the plain text of the digital currency to generate a digital After the currency ciphertext is transferred offline to the receiving end; so that the receiving end can restore the plaintext of the digital currency with the encrypted private k...
Embodiment 3
[0161] Embodiment 3 of the present invention provides a digital currency anti-counterfeiting and verification method based on the L algorithm. The method is described on the receiving side, and the method includes:
[0162] Split the anti-counterfeiting key corresponding to the digital currency public key stored in the trusted center into a stub key stored in the trusted center, a digital currency key stored in the digital currency, and a user key stored in a non-terminal;
[0163] The receiving end uses the receiving end encrypted private key to restore the digital currency ciphertext sent by the sending end to the digital currency plaintext, and performs local banknote verification to verify the authenticity of the digital currency. If the verification fails, an error will be prompted and the process will be terminated; if the verification is successful, the receiving end will pass The once-updated digital currency key in the received digital currency, the receiving end updat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com